Operation OKRA Operational Analysis
Australian Operations to Degrade the Islamic State—2014–2024
Executive Summary
Beginning in 2014, the Australian Defence Force (ADF) was committed to Operation Okra in the Middle East, with the aim of degrading the Islamic State, ISIS, or Daesh. This objective was ultimately achieved in 2018, although ongoing operations monitoring the threat have since continued. It has now been a decade since the commencement of this intervention, which the ADF formally concluded in December 2024. The Chief of Defence Force (CDF) acclaimed the ‘excellent work’ of some 4,800 service men and women who served on Operation Okra and ‘made a tangible and important contribution to global security’.[1] While such conclusions are likely correct, little is offered by Defence media releases to truly assess the veracity of CDF’s praise.
Meanwhile, the Islamic State remains. Throughout 2024, isolated guerrilla attacks continued throughout Iraq. One Islamic State ‘franchise’, the Islamic State Khorasan Province (IS-KP), successfully mounted an attack against Russia’s Crocus City Hall on 22 March 2024. Further IS-KP attacks in Europe were successfully prevented. Rounding out the year, ISIS successfully ‘inspired’ an attack in New Orleans.[2] These events demonstrate that ISIS remains a latent threat, capable of external operations (EXOPs) outside the Middle East.
This paper undertakes an operational analysis of the ADF’s contribution to operations against ISIS in Syria and Iraq, particularly focusing on the heightened period of combat operations from 2014 to 2018. It does so with an aim to inform the strategic planning and conduct of current and future counter-terrorism efforts, such as those undertaken by Operation Augury—the ADF framework in support of efforts to counter terrorism and violent extremist organisations around the world.[3]
There is an evident need for such understanding. When it first captured the West’s attention in 2014, the Islamic State was more than a ‘terrorist’ group, and the Middle Eastern conflict in which it was involved was much more than a civil war. Indeed, by 2014, the conflict in Syria had become a messy failed revolution spilling over into Iraq that grew into a proxy civil war involving the US, Russia, Saudi Arabia, Qatar, Iran, Turkey and Jordan. This dynamic was prominent in the surprising success of Turkish-backed Hayat Tahrir al-Sham (HTS) in December 2024 in Syria, seemingly resolving the conflict.
By examining Australia’s recent experience in the Middle East, this paper reflects critically on the planning challenges that emerge from engaging an irregular or non-state adversary (such as the Islamic State) in the context of multi-party strategic competition. While Western military operations against ISIS were ultimately successful, a contemporary appreciation of the competitive environment in which other nations pursued their proxy strategies seemed incomplete at times—perhaps even naïvely absent. Western actions did not always translate into effective strategy; our understanding of our adversary was incomplete, and we created counterproductive second-order effects from our actions. There are therefore clear lessons to be learned from this conflict.
Curiously, there has been little published by Australian authors examining the military challenges, personal experiences, and lessons from Australia’s contribution to national security efforts to counter the Islamic State. This paper aims to remediate this gap.
As the US and Australian national security communities pivot to an era of major power competition, drawing lessons from our past decade of engaging in competition is a curious oversight. Beginning with the Arab Spring in 2011, the decade of conflict in the Middle East has seen competition between the US and Russia, the Sunni and Shi’a branches of Islam, Qatar and the Gulf States, and Turkey and Russia. These examples demonstrate that major and middle powers wish to avoid direct conventional warfare which risks runaway escalation. Major and middle powers avoid the risk of runaway escalation of tension by attempting horizontal escalation directly and indirectly (i.e. via proxies). In so doing, states that are in competition with one another exploit opportunities to impose costs and to undermine the interests of their competitors. Conflict environments provide such opportunities.
This is not new. As Henry Kissinger identified in 1955:
But is there any deterrent to Sino-Soviet aggression other than the threat of general war?... Our immediate task must be to shore up the indigenous will to resist, which in ‘grey areas’ means all the measures on which a substantial consensus seems to exist … Thus, our capacity to fight local wars is not a marginal aspect of our effective strength; it is a central factor which cannot be sacrificed without impairing our strategic position and paralysing our policy.[4]
The relevance of this paper’s analysis to today’s environment of heightened geopolitical competition is evident in the increasing proclivity of states to compete via irregular proxies. The ADF, however, has no publicly available policy guidance that highlights the threat of proxy conflicts and how to appropriately respond.
The Australian Government has responded to contemporary strategic challenges with the Defence Strategic Update 2020 and the Defence Strategic Review 2023. This Defence planning documentation is, however, almost exclusively orientated toward major platform acquisitions—those capabilities required for major conventional warfare (i.e. ‘respond’ tasks), which are of much less utility to the land-based, irregular wars likely to arise from proxy competition (i.e. ‘shape’ tasks). A tension thus emerges between the Defence investments in ‘shape’ tasks versus ‘respond’ tasks.
By raising lessons as to how the ADF can more effectively engage with irregular or non-state actors, this paper aims to help mitigate the opportunity costs that exist where defence policy is sparse, and thereby inform strategic policy options for government. While the intended audience is primarily Australian military officers, the paper’s arguments are also expected to contribute to allies’ understanding of our common challenges in countering today’s proxy and irregular warfare challenges.
Introduction
There are a number of organised groups that are intent on attacking American soldiers … We don’t believe them to be under a central leadership and we are taking appropriate action to deal with the threat. This is not a resistance movement.
Lt. Gen. William Wallace, commander of the US V Corps in Southern Iraq in July 2003[5]
Western militaries have a track record of misunderstanding the use of non-state armed groups, or irregular actors, as a component of a state’s national security strategy. Proxy and irregular warfare were tools in Saddam Hussein’s arsenal. Documents captured by the Israeli Army in Lebanon in 1982 show that Iraq provided support to the Palestinian Liberation Organisation (PLO).[6] A Sa’iqa (lightning or thunderbolt) course enhanced the PLO’s unconventional capabilities and was hosted in Baghdad (the course was also offered in Moscow and Syria), involving so-called ‘special forces’ training.[7]
Inspired by the 1979 Islamic Revolution in Iran, the Syrian Muslim Brotherhood staged an uprising in 1979–80 against the Syrian Hafiz al-Assad regime, centred on the city of Hama. Iraq provided ‘covert support to the Brotherhood, particularly in Aleppo’.[8] This proxy war with Syria occurred in the context of the concurrent Iran–Iraq War of the 1980s, a regional competition for hegemony in the Middle East. During the Iran–Iraq War, Saddam also supported the Democratic Party of Iranian Kurdistan (DPKI) and the Mujahideen e-Khalq (MEK) to undermine the Iranian war effort.
Following the 1991 Gulf War, Saddam learned from his defeat. In 1994, the Fedayeen Saddam was established, a paramilitary force under the command of Saddam’s son, Uday. Ultimately, this force would come to number between 25,000 and 40,000 men.[9] This paramilitary force effected a layered defence, with the innermost layer, located in the cities, called al-Muqawamah (The Resistance). The goal evolved to create ‘Mogadishu on the Tigris’ using relatively autonomous groups cooperating with each other on an ad hoc basis.[10]
Commencing in August 2002, weapons caches were established in the countryside and throughout Iraqi cities.[11] In September of that year, some 1,000 selected intelligence and special operations officers undertook training at the two Fedayeen training camps in Salman Pak and Bismayah.[12] Fedayeen numbers were bolstered by the recruitment of pan-Arab volunteers who had worked or studied in Iraq prior to the commencement of the war, as well as thousands of Syrians who were recruited and who subsequently infiltrated Iraq.[13]
These Fedayeen were coordinated by an underground resistance structure, based upon five-man cells, and led by General Izzat Ibrahim al-Douri.[14] External leadership of this resistance enjoyed sanctuary in Damascus. At its peak, the resistance included 14,800 former Ba’athist regime soldiers, officers and officials on full-time combat operations. Up to 100,000 members of the former Mukhabarat secret police might be added to that list, likely performing underground and auxiliary intelligence functions.[15] At the commencement of the insurgency, US intelligence services ‘estimated that al-Qaeda in Iraq (AQI)-aligned foreign fighters were generally believed to have been no more than two to five percent of the overall resistance’.[16] Over time, however, organisational evolution, atrophy of former regime elements, and tactical alliances blurred this ratio.
AQI established a sanctuary within Fallujah, exploiting popular grievances against the US occupation that were fuelled by the violent American suppression of local protests on 28 to 30 April 2003.[17] AQI worked pragmatically with resistance groups to accelerate the insurgency and seize Fallujah, creating an internal sanctuary area as well as reinforcing a public narrative of spiralling insurgency.
Lieutenant General Wallace (quoted at the beginning of this chapter) misunderstood the threat of Iraq developing irregular actors to operate against its neighbouring countries. In reality, a resistance movement was deliberately created by the Ba’ath Party to impose costs upon an unsuspecting US Army. Wallace’s failure to properly understand the adversary was a common one at the time, a failure to which much of the anguish of the past 20 years of conflict in the Middle East can be ascribed.
Situating the Conflict in the Levant
This chapter explores the key policy challenges that the Operation Okra intervention presented to Australia, building on the history of the Levant—the geographic region of the central Middle East encompassing Syria, Iraq, Jordan, Lebanon and Israel.
This analysis primarily focuses upon the period 2014 to 2018, which saw the emergence of Islamic State (also termed ISIS or Daesh) as a Western foreign policy issue through to its territorial defeat. The period concludes with the challenge that arose when Sunni extremism was replaced by Iranian-sponsored Shi’a terror and patronage networks (termed the Iranian Threat Network, or ITN). The ITN thereafter assumed the role of forefront foreign policy challenge in the Middle East, in the form of Hamas’s war with Israel, the Houthi threat to maritime shipping in the Red Sea, Iranian-aligned militia groups dominating the Iraqi political scene, and the conduct of direct Iranian strikes against Israel on the night of 14 April 2024. This context is important as it describes the pathway to the precipice posed by an Israeli–Iranian war: the closest the region has come to a major conventional conflict since the invasion of Iraq in 2003. The threat of regional conflagration was subsequently realised in June 2025.
The emergence of Islamic State in 2014 created what were seen at the time as unique foreign policy dilemmas that are curiously under-recognised today. First, Islamic State demonstrated a technical sophistication in operations in the cyber domain beyond what Western policymakers dismissively ascribe to non-state actors. It was a ‘digital caliphate’ with technical proficiency underpinning its comprehensive propaganda wing and ability to coordinate EXOPS via ‘inspired’ attacks.[18]
Second, and leveraging the first point, a non-state armed group was simultaneously creating challenges in the ‘deep’ battlespace of the Middle East, the ‘close’ battlespace of the South-East Asian region and the ‘rear’ of domestic intelligence and policing challenges within Australia. Traversing these regions were the Australian foreign fighters—those who travelled to join Islamic State—who contributed to the operational threat overseas, and who would also pose a threat to national security upon their return.[19] Spanning such linkages were funding flows, remote radicalisation efforts, and the sharing of tactics, techniques and procedures that improved the adaptability of Islamic State ‘franchisees’. The rhetoric of whole-of-government approaches became reality, as no single department or agency had the required authorities, mandate or resources required to address this global challenge.
Third, the overlapping influences of middle and major powers (who were competing through their chosen proxies) further complicated the situation. Indeed, it is difficult to accurately define the conflict as a ‘counter-terrorism’ effort, an insurgency, a muddled proxy war, or something in between. In actuality, it was all of these things.
More recently, attacks by Islamic State Khorasan Province (IS-KP or ISIS-K) against Russia in 2024 and the inspired attack of New Year’s Day 2025 in New Orleans demonstrate the enduring threat posed by transnational terrorist organisations. As the Institute of Economics highlighted in their 2024 Global Terrorism Index report, the ‘epicentre of terrorism has shifted out of the Middle East and into the Central Sahel region of sub-Saharan Africa’.[20] Deaths from terrorism are increasing, now at the highest level since 2017, and Islamic State remains the deadliest terrorist group.[21]
The military response to the challenge posed by ISIS specifically, and the Iraqi insurgency in general, highlights the problem with the overuse of ‘terrorism’ as a label, since it elevates the phenomenon of terrorism to a strategy. From the outset of the Iraq insurgency in 2003, there was a tension between whether the violence was being driven by former Iraqi Ba’athist party members (and hence indicative of a resistance) or al-Qaeda (and therefore indicative of a terror campaign).[22] On balance, the evidence pointed initially towards the former. Over time, the distinction was blurred by the incorporation of ex-Ba’athists into al-Qaeda in Iraq (AQI) and AQI’s organisational affiliations with the panoply of insurgent groups in Iraq.
Further tensions are evident. The designation of the Iraqi Shi’a militia, Kata’ib Hezbollah, as a US Department of State-listed foreign terrorist organisation would suggest this group was regarded as a terrorist group, yet the Iraqi government would identify it as state-authorised Iraqi Popular Mobilisation Forces (PMF) and therefore allies in the war against Islamic State.[23] A similar difference of opinion mired the US–Turkish relationship due to the partnership between the US and the Kurdish Partiya Yekîtya Demokrat (Democratic Union Party (PYD)) militia. This relationship was problematic for the Turkish government, who viewed the PYD as an extension of the Kurdistan Workers Party (PKK) terrorist movement.
Overuse of the label ‘terrorism’ risks confusion as to the strategic significance of the threat. Hoffman observed:
Terrorism is a purposeful human political activity which is directed toward the creation of a general climate of fear, and is designed to influence, in ways desired by the protagonist, other human beings and, through them, some course of events.[24]
Simplistically designating ISIS as a terrorist organisation inverts what we typically mean by this term: a clandestine group fighting for survival. The Islamic State was instead, in 2014, better described as a rogue political entity that was trying to function as a state.[25] In contrast, the Assad regime had long sponsored terrorism and, by 2011, might have been viewed as having lost its legitimacy to govern. States were operating in ways we would associate with non-state revisionist actors; non-state actors were operating in ways we would associate with states.
In the context of these challenges of terminology, and with reference to events in the Middle East, former US military officer Liam Collins notes:
The group [ISIS] did not fit neatly into traditional analytical categories: it was a pseudo-state, a terrorist group, and an insurgency simultaneously. This complexity both complicated analysis of the organisation’s rise and challenged transitional metrics for determining progress and victory in the war against them.[26]
A similar criticism could today be levelled towards the challenges posed by Hamas, the Houthis, or Kata’ib Hezbollah.
The reality is that irregular or non-state groups may operate across a spectrum, from civil disobedience to radicalised terrorism. In some situations, irregular groups may seek to create a climate of fear and thus employ terrorist techniques to pursue their ends because they may be too weak to exert other forms of control, or because they seek to influence the domestic audiences that undermine a military force. Over time, irregular groups may grow in strength to the point where they wage insurgency. Importantly, irregular groups may also deliberately abstain from tactics of terrorism if they recognise that it undermines the group’s legitimacy in the eyes of its relevant population. To conflate terrorist radicalisation with recruitment into broader irregular groups is misleading and is a challenge that the national security community needs to resolve.
Strategic Purpose
Australia’s military response to the threat posed by Islamic State was known as Operation Okra. It was a component of a US-led coalition commitment termed Operation Inherent Resolve (OIR). Examining the challenges involved in engaging irregular adversaries such as ISIS can inform both military and policy planning efforts to meet future threats. With this frame of reference, this analysis focuses on four related ways that military forces can engage with irregular forces and proxy warfare to achieve strategic objectives:
- The employment of air power against an irregular adversary
- The utility of ‘decapitation’, targeting’ or ‘counter-network operations’ against an irregular adversary
- Proxy warfare through capacity-building and provision of battlefield support
- The mechanism and utility of information operations.
President Obama’s seemingly dismissive quip that ISIS was a ‘JV’ (junior varsity) organisation certainly didn’t age well. That ISIS ultimately survived two furious applications of Western military force (2004–2010 in its earlier designation as al-Qaeda in Iraq, and again in 2014–2018) underscores the potential resilience of irregular organisations operating within a supportive population. This resilience matters when considering the contemporary challenges posed within the under-governed spaces controlled by Islamic State Khorasan Province (IS-KP) in Afghanistan; Islamic State Sahel Province (IS-SP, also termed Greater Sahara) in Mali, Niger and Burkina Faso; and Islamic State in Somalia.
An Introduction to Irregular Proxy Warfare
The conflict against ISIS has occurred within a decade characterised by major revolutionary uprisings across the Arab world, involving at least 16 of the 22 Arab states experiencing national protests or upheaval.[27] This broader political change has fuelled the development of proxy relationships as major and middle powers compete for strategic influence.
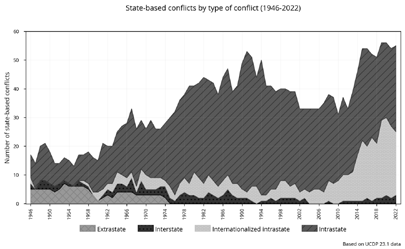
Although the ADF has experience fighting irregular forces in Timor-Leste, Solomon Islands, Afghanistan, Iraq and Syria, irregular warfare theory is generally absent from Australian professional military education and Defence policy documents.[28] This gap exists despite an increasing frequency of ‘internationalised intrastate’ conflict (i.e., proxy warfare involving non-state actors).[29] This trend is shown in Figure 1.1 below. In 2017, the Uppsala Conflict Data Program (UCDP) recorded the highest number ever of non-state armed conflicts (85). The previous peak was in 2000 at 47 non-state armed conflicts.[30]
Figure 1 drawn from UCDP data[31]
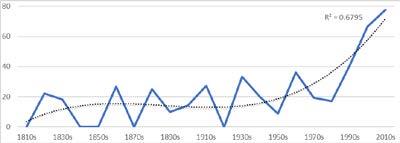
Accompanying an increasing trend towards irregular conflicts is a parallel trend towards the involvement of foreign fighters in armed conflict.[32] Foreign fighters may be state sponsored or diaspora supported, or they may be self-motivated. For example, the Tamil Tigers of Tamil Eelam (LTTE) were financially well supported by a sizeable Westernised Tamil diaspora. This phenomenon of foreign fighter mobilisation flouts regulation. States may deliberately exploit this ambiguity when they support ‘volunteers’ to travel to support a given proxy, all the while claiming such individuals are acting of their own free will. Although a detailed analysis of this phenomenon is beyond the scope of this paper, the increasing number of foreign fighters (shown in Figure 1.2 below) is likely being facilitated by the increased prevalence of information-age technologies, such as social media coupled with smartphones.[33]
The trend is provided by the dotted line with a high R-squared value of variance.[34]
The Gap
In general terms, there is a literature gap regarding the examination of irregular and proxy warfare, such as that experienced by the ADF on Operation Okra. A measure of this gap can be gauged by a review of Australia’s primary national security document, the Defence White Paper (or equivalent), over the past 45 years. The outcomes of this analysis are shown in Table 1.1 below. It demonstrates the absence of any focused analysis of non-state actors, with no explanation of the strategic objectives such threats pursue.
| Defence Policy Paper | ‘Proxy’ | ‘Irregular’ | ‘Unconventional’ |
|---|---|---|---|
|
2024 (termed National Defence Strategy—NDS) |
No mention | No mention | One mention in explaining ‘asymmetry’ |
|
2023 (termed Defence Strategic Review—DSR) |
No mention | No mention | One mention in explaining ‘asymmetry’ |
|
2020 (termed Defence Strategic Update—DSU) |
No mention | One mention in a temporal sense only | No mention |
| 2016 | No mention | No mention | No mention |
| 2013 | No mention | No mention | No mention |
| 2009 | No mention | One oblique mention | Twice obliquely mentioned |
| 2000 | No mention | One oblique mention | No mention |
| 1994 | No mention | No mention | No mention |
| 1987 | No mention | No mention | One oblique mention |
| 1976 | No mention | No mention | No mention |
The problem of limited intellectual inquiry and debate about these facets of contemporary warfare—irregular (non-state actors), proxy warfare as a component of competition, and foreign fighters—is that a soldiers’ or officers’ personal experiences become their understanding of the war. This blinkered perspective then risks a situation in which an understanding of the war becoming their understanding of warfare in general. This analysis responds to this gap.
Background: the Context for Operation Okra
One of the most notable geopolitical trends of the last five years has been the growing number of states intervening in and shaping conflicts to advance their own foreign policies and strategic agendas … powers such as Iran, Israel, Russia, Saudi Arabia, Turkey, and the United Arab Emirates (UAE) intervening in multiple conflicts across the world … Most have supported local allies or partners or proxies … this trend has been on full display in several armed conflicts in 2020 and early 2021.[35]
In 2014, Australia and its Western partners characterised the international response to the conflict in Syria and Iraq as ‘the military defeat of Islamic State’.[36] Yet ‘ISIS is a symptom’ of broader Middle Eastern social and political unrest, and therefore the military response required nuanced understanding of the international, domestic and local governance competitions occurring between sectarian and political power structures.[37] There is little evidence of efforts to address such drivers of conflict. This chapter examines these and broader issues that framed the strategy that underpinned Operation Okra.
Operation Inherent Resolve
The US military mission for OIR was ‘by, with and through regional partners, to militarily defeat ISIS in the combined joint operations area (Iraq and Syria) in order to enable whole-of-coalition governmental actions to increase regional stability’.[38] This mission statement articulates a proxy strategy—a point unrecognised by Australian policy as seen in the previous chapter. The stated purpose of ‘increased regional stability’ also demands attention: defining success as such would suggest that now that the mission is complete, the Middle East is more stable it was before the emergence of the Islamic State. Military success defined in such terms is vague at best.[39]
Speaking soon after his deployment in 2014 to Iraq, Major General (Ret.) Pittard described the situation on the ground as highly ambiguous. He observed that no one could answer the questions: ‘What is the mission? The desired endstate’?[40] Former US Secretary of Defense Ash Carter amplified these concerns, describing the situation in December 2014 as ‘lacking a comprehensive, achievable plan for success … clearly articulated objectives or a coherent chain of command for the operation’.[41] In sum, for at least the first three to four months, OIR lacked a coherent strategy.[42]
Ultimately, Secretary Carter framed America’s mission objectives in terms of deep, close, and rear strategic outcomes. Specifically, he conceptualised the mission as dealing ‘ISIS a lasting defeat in its homeland of Iraq and Syria, eliminating the cancer’s parent tumour; combatting metastases in places like Libya and Afghanistan; and protecting our homeland from ISIS terror’.[43] In December 2015, Secretary Carter testified to the Committee on Armed Services that ‘our strategy is to destroy ISIL in Syria and Iraq and anywhere else it arises’. While simplified for public consumption, this statement gives one pause due to its open-ended nature. The statement also lacks clarity as to what ‘end’. In other words, the strategy lacks the clear political purpose that Clausewitz would prescribe for such military action.[44] Further, commentary regarding an intention to destroy the Islamic State ‘anywhere else it arises’ is at odds with the ongoing existence of the franchise in Afghanistan, Somalia and the trans-Sahel.
Operation Okra
The Australian response to the threat posed by ISIS was framed by then Attorney-General George Brandis on 10 September 2014 as a collective self-defence of Iraq.[45] The mission of the Operation Okra intervention was to ‘degrade, destroy and defeat’ ISIS.[46] In this context, the purpose of Operation Okra as ultimately defined in 2019–20 is notably different from that defined in 2014. The purpose of Operation Okra was ‘ADF operations in Iraq and Syria to support the coalition response to the Iraq crisis, including the deployment of forces to disrupt and degrade Daesh [IS]’.[47] This change in language intimated a recognition that military intervention was incapable of destroying the Islamic State movement—a view that has been borne out by subsequent events.
Despite such modifications to the mission mandate, speculation remains around the policy basis for Australia’s military intervention. Parliamentary researcher Renee Westra noted that there has been ‘no substantial public discussion or parliamentary debate about any long-term plan or strategy in Syria or Iraq’.[48] Interlinked issues such as ‘aid and reconstruction efforts’ and the future role of Assad’ remain unaddressed’—facts on the ground having decided the result in December 2024.[49] In economic terms alone, the ‘cumulative real cost’ of operations against ISIS in Iraq from 2014–20 was estimated by the Australian Strategic Policy Institute to be approximately $1.3 billion.[50] Allan Behm argued that for such a cost, Australia’s net military result of Operation Okra is ‘a presence in search of a policy’.[51]
Broader Perspectives
The timing of the US and Australian interventions in Syria and Iraq warrants attention. While the execution of American James Foley in August 2014 attracted political attention, it was the coincidental pressure of the ISIS military expansion upon the security situation in Baghdad that prompted the US to consider the evacuation of its non-combatant embassy staff. These concerns were reinforced when genocidal violence was undertaken against the Yazidis.[52] These rapidly shifting dynamics prompted the US intervention and presence in Iraq which, in turn, informed subsequent planning to counter the ISIS threat.
When juxtaposed with events unfolding on the ground, the timing of the US intervention suggests that deeper political pressures were also at play. Specifically, there was a ‘sunk cost bias’ for continued support of the Iraqi government, alongside humanitarian concerns about genocide and violence against civilians. Andrew Mumford suggests that the Obama administration’s overriding policy was to avoid a large-scale conventional-force response. This explains why a low-cost proxy intervention may have appealed to US policymakers.[53]
For the Iranian government, the strategic stakes were far higher. Following a general trajectory of expanding influence beginning with the 1979 Revolution, Iran became dominant in Iraqi politics once US troops withdrew in 2010. Iran was close to consolidating power commensurate with that of a regional hegemon. The 2011 Arab Spring protests, however, threatened the vulnerable position of the Iranian-aligned Assad regime in Syria. If Assad were to be ousted, Iran’s ability to influence events in Lebanon and, indeed, to leverage its proxy, Lebanese Hezbollah, to pressure Israel, would dissipate. The potential for ISIS to spawn a new Shi’a–Sunni sectarian war in and around Baghdad in Iraq also threatened these Iranian interests. A sectarian war might fatally undermine Iraq’s Maliki regime and potentially lead to masses of Shi’a refugees fleeing to Iran. The potential for such setbacks was inimical to Tehran’s national security interests and prompted the creation of significant Iranian proxy commitments across the Levant.
Iranian influence across the region presented a threat to Saudi Arabia and like-minded Sunni partners. A ‘Shi’a crescent’ from central Afghanistan to the Mediterranean loomed. Riyadh had long contested Tehran’s influence in the Middle East, in what Dilip Hiro describes as a ‘Cold War in the Islamic World’.[54] Through longstanding organisations such as the Muslim Brotherhood, fellow travellers in Sunni Islam could be found across the region, which rose to exploit the turmoil of the Arab Spring. Extant groups, such as the Syrian arm of the Muslim Brotherhood, were at an advantage in competing for influence compared to emergent elements such as the Free Syrian Army (FSA), the Syrian National Council (SNC) and the Syrian Opposition Coalition (SOC).[55]
Humanitarian aid from the Gulf states, channelled through the Muslim Brotherhood into Syria, initially amounted to US$1 million to US$2 million per month.[56] In response, a veritable explosion in proxy relationships occurred with up to 300 groups reportedly present in Syria during its civil war. In simple terms, ‘Saudi Arabia sponsored Salafists while the United Arab Emirates supported secular liberals … Turkey and Qatar supported groups with a Muslim Brotherhood orientation’.[57] A new proxy relationship on one side presented itself as a threat to the other, requiring the generation of a counter-relationship to neutralise the perceived risk. These competing interests manifested akin to Newton’s third law—‘Every action has an equal and opposite reaction’. The International Institute for Strategic Studies (IISS) observed of this milieu:
The global geo-strategic position of the Middle East is the key to understanding why the Middle East matters. For millennia, it has been at the cross-roads between the civilisations, languages and cultures of north Africa and Asia, Europe and Africa, eastern Europe and Asia Minor, with Egypt, the Ottomans and Persia as key players. They remain so.[58]
Australian Interests
From an Australian perspective, the globalised nature of the ISIS threat metastasised into a range of challenges, spanning deep, close and rear geography—similar to the view of Secretary Carter. In the ‘deep’, the challenge posed by ISIS was complicated by the backdrop of the aforementioned competitions. Such competition was not limited to the Levant. In Libya, Sunni groups backed by Turkey and Qatar (which were generally supportive of Muslim Brotherhood-aligned ideology) competed with Saudi Arabia and the Gulf States (which generally supported Salafi ideology, moderate groups, and/or autocratic regimes).[59]
Similar competing interests for patrons of proxy warfare had emerged with the rise of ISIS-Khorasan (ISIS-K or IS-KP) in Afghanistan. Australian strategic interests in that country resulted in a long-term commitment of assistance to the government of Afghanistan. In 2015, this manifested as the capacity-building mission Operation Highroad (2015–2021). This military framework had the potential to position the Australian Government to take a strong anti-ISIS-K stance across the Middle East region. Indeed, Australia had already signalled its abhorrence of ISIS to the international community, and this was an opportunity to pressure the ISIS franchise in Afghanistan with an operational commitment. However, there is little available evidence that Australia viewed the Islamic State threat as having regional implications in Afghanistan. The reasons remain opaque.
In the ‘close’ (or regional) environment, the emergence of ISIS’s affiliation with the Abu Sayyaf Group (ASG) in the Philippines had the potential to fuel a resurgence in Jemaah Islamiyah and terrorist violence across the Indonesian archipelago. That this situation could emerge so soon after the cessation of the US-led Operation Enduring Freedom–Philippines (2002–2015) highlights the tenacity of some non-state armed groups. In response, Australia committed to a military operation in support of the Armed Forces of the Philippines in its efforts to clear Islamic State fighters out of Marawi. Regrettably, there is little material in the public domain concerning Operation Augury-Philippines (2017–2019), the ADF’s military contribution in the Philippines to this ISIS-inspired threat.[60] Again, events imply the perception of misunderstanding of the Islamic State’s globalised networked posture.
While Australia’s strategic commitment to countering ISIS remained equivocal, the regional threat posed by the group’s rise continued to grow exponentially. Analysis by the Soufan Center (see Table 2.1) suggests a greater than fourfold increase in recruitment to ASG and other extremist organisations following the emergence of ISIS in the Middle East.[61] With this context, the absence of a clear connection between Operation Augury-Philippines and Operation Okra suggests a misunderstanding among Australian policymakers of the global linkages of IS ideology.
| 2000–2005 | 2006–2010 | 2011–2015 | 2016–2021 | |
|---|---|---|---|---|
| Arrests | 244 | 240 | 397 | 1,250 |
The domestic or ‘rear’ challenge posed by ISIS was ultimately recognised by Australia in January 2015 in the Review of Australia’s Counter-Terrorism Machinery.[63] This report linked offshore actions to potential domestic consequences and drew attention to the regional ‘spillover’ effects of the ISIS phenomenon, including the threat posed by lone-actor attacks and foreign fighters. The relevance of this link to the ADF was explicitly noted:
While ADF operations overseas have not traditionally been framed as part of Australia’s CT [Counter-Terrorism] mission, they have contained significant CT elements … Consequently, ADF requirements for intelligence for Operation Okra significantly overlap with everyday CT work done by Australian national security agencies … ADF missions may also provide valuable intelligence on CT issues and developments, and this needs to be factored into CT prioritisation and coordination measures.[64]
This statement clearly recognised the interconnected nature of contemporary conflict in the information age. The challenge remained, however, for Australia to coherently address the threat of terrorism across geographic regions.
Situating Operation Okra
Western militaries subscribe to the doctrine of manoeuvre warfare, which seeks to ‘collapse the enemy’s cohesion and effectiveness through a series of rapid, violent, and unexpected actions that create a turbulent and rapidly deteriorating situation with which the enemy cannot cope’.[65] Two cases come to mind demonstrating this ideal in practice: the Islamic State’s advance on Mosul in 2014 and the Hayat Tahrir al-Sham (HTS) advance on Damascus a decade later in 2024. Theoretically, such language subscribes to a strategy of ‘annihilation’.[66]
In practice, Western forces struggle to achieve this ideal and often resort to the employment of attrition tactics.[67] A sequential, attritional approach, leveraging the technological and firepower advantages of the West, was always going to inflict significant casualties upon ISIS, which could then be exploited by Iraqi government forces to inflict a military defeat. In this sense, the strategy was effective. Questions should be asked, however, about whether the notions of manoeuvre warfare were achieved, or if the strategy might have been executed more efficiently—in terms of time, military resources, and funding.
Choosing a strategy of attrition (through the application of limited ends and means) might be entirely appropriate in an environment of strategic competition. Alternatively, an absence of action might provide space for competitors to further their strategic aims. Equally, decisive action might lead to opportunities for competitors to seize upon our military successes to secure political victories, as General Suleimani achieved at Amerli (discussed subsequently).
In the context of global competition, contemporary conflicts require a long-term, cumulative view.[68] Such nuance is arguably missing from a Western doctrinal approach that advocates annihilation without elaborating upon suitable contexts in which an attrition-based approach might be an appropriate strategy. The ongoing presence of the Islamic State, continuing political turmoil in Baghdad, unresolved questions of north-eastern Syrian sovereignty, the rising influence of Iran, and issues around foreign fighter radicalisation are second- and third-order effects of an attritionist strategy that must inform our choice of approach. In other words, consideration of such issues informs the measures of effectiveness by which the appropriateness of our strategic decisions will be measured.
As the ADF pivots towards an era of major power competition, it is intriguing that we are not looking more closely at the lessons of this past decade of competition—between the US and Russia, Sunni and Shi’a, Qatar and the Gulf States, and Turkey and Russia. These recent examples of competition demonstrate that vertical escalation carries the cost of unpredictable conflict that states wish to avoid. This is most evident in the extensive efforts taken by Russia and the US to deconflict airspace within Syria. Competition between states manifests instead in proxy wars, where patrons support irregular or non-state actors to further their strategic interests. This is a reality that is seemingly yet to be recognised within Australian policy.
By illuminating the connectivity and complexity inherent in the ISIS challenge, this chapter has provided a foundation for the paper’s further analysis. It has described the international context within which Operation Okra was conducted and identified gaps in Australia’s strategic and policy responses to the ISIS threat. Building on this context, the next chapter will propose a model for understanding the nature of irregular warfare that can aid policy and military decision-makers to better understand how ISIS was able to achieve its rapid growth and military successes.
Understanding the Enemy
In this chapter, the operations of ISIS are examined to shed light on its genesis and methods. The importance of this chapter lies in its efforts to dispel the derisive ‘terrorist’ and ‘religious’ labels, recognising instead that this group pursued strategies more akin to Communist revolutionary warfare theory. Such analysis adds nuance to our understanding of ISIS and informs the paper’s assessment of the strategies that were employed during the US’s OIR and Australia’s Operation Okra.
The Roots of Rebellion in North-Eastern Syria.
The north-eastern Syrian provinces of Deir ez-Zour, Raqqa and al-Hasakah are known as the breadbasket of Syria. However, a drought that lasted in this region from 2000 to 2010 led to significant economic deprivation, reducing approximately two to three million of Syria’s 10 million rural inhabitants to extreme poverty.[69] The drought crippled the already fragile agricultural base of this region and prompted a rural–urban migration.
In response, the Assad regime applied selective welfare on a sectarian basis. The result was that the Sunni Arab and Kurdish peoples of the north-east (comprising 58 per cent of the Syrian population) became poor.[70] Despite the wealth emanating from oil wells in this region, infrastructure was aging and there was little to no internet penetration.[71] Well-established smuggling and criminal networks between Turkey, Syria and Iraq traded in oil and antiquities and extorted the business class, decreasing businesses’ profit margins.[72]
Migration offered no reprieve for the rural poor as it overloaded a system already supporting a quarter of a million Palestinians and approximately 100,000 Iraqis who had fled the Iraq war (2003–2010). Approximately 18.2 per cent of the Syrian population had fallen below the poverty line, ‘with rural Damascus, Idlib, Homs, Dara’a, al-Sweida, and Hama governorates among the most affected’.[73]
This disaffected population of Syrian farmers offered fertile ground for ISIS. ISIS’s organisation of Syrian agriculturalists built upon a robust underground infiltration network into Iraq that had operated during the mid-2000s.[74] These local smuggling networks had served to support AQI in 2006–07 and now provided the underground function for the ISIS insurgency in the region during the 2012–13 period.[75] With increased oil supply, lower taxation and high oil prices, smuggling flourished under ISIS, resourcing the proto-state with zakat taxation income in a symbiotic relationship.[76]
The Implications of Syrian Deprivations
The competition for control over Syria’s Sunni Arab population has roots in the Alawite repression of the 1979–1982 uprisings against the Hafiz al-Assad regime, in which turmoil spread to almost all Syrian cities. This systematic and violent repression of the Muslim Brotherhood included state-sanctioned massacres.[77] Al-Qaeda strategist Abu Mus’ab al-Suri concluded from this experience that rebellion without popular support structures was hopeless against such organised repression.[78]
The Sinjar Records (a set of captured personnel records from AQI covering the period August 2006 to August 2007) show that more than half of the Syrian AQI fighters came from the north-east, most from Deir ez Zour (34 per cent) and Hasakah (6 per cent) provinces.[79] Syrian fighters also constituted 8.2 per cent of AQI recruits over this 12-month period, making it the third-highest nation represented.
The depth of the relative deprivation felt by the Sunni populations of eastern Syria produced a generation of organised resistance to authority, most pointedly demonstrated in the 1979–82 uprising. However, Nate Rosenblat and David Kilcullen argue that the chaos of the 2011 Syrian Revolution did not alleviate the deprivation felt in Raqqa, which set conditions for ISIS to present their narrative for effective governance.[80] ISIS began to infiltrate Raqqa’s governance structures in 2013, using assassination, intimidation and a ‘spiral of silence’.
Approximately 60,000 ISIS fighters controlled the 8 million inhabitants of north-eastern Syria and north-western Iraq in 2015, an area approximately the size of Great Britain. Given that ISIS represented only 0.75 per cent of the population, this level of control suggests that they were able to leverage a largely sympathetic population to establish governance functions and repress dissent.
Islamic State’s Strategy, Aims and Objectives
It has been claimed that ISIS’s strategy broadly conformed to an almost prophetic al-Qaeda ‘master plan’ authored by Sayf al-Adl, al-Qaeda’s security chief, in 2001.[81] This view is oversimplified, as al-Qaeda and ISIS (including the earlier manifestation of AQI) experienced significant friction around their differing objectives and methods. Nonetheless, ISIS did grow from al-Qaeda roots and can therefore be seen as having adopted advice from influential jihadist mentors.
ISIS exhibited strong agency in selecting its objectives and executing its strategy. Fawaz Gerges makes an interesting point in this regard, noting that ‘the two previous jihadist waves of the 1970s–1990s had leaders from the social elite, supported by ‘middle-class and lower-middle-class university graduates’.[82] In contrast, ISIS’s cadre was rural and agrarian, an echo of Mao’s strategic pivot from Leninist doctrine to his focus on the rural peasantry. In this context, evidence of ISIS’s assimilation of ‘Communist Revolutionary Warfare’ doctrine suggests a purposeful approach to the formulation of strategy.[83]
Sayf al-Adl’s strategic plan prescribed four stages from 2000 to 2013, which maps well to the actions of AQI, until its defeat in 2010. The fifth stage in his strategy, that of declaring a caliphate in Syria between 2013 and 2016, demonstrated astute analysis.[84] He recognised that Syria was weak under the Assad regime as it would be unlikely to receive American support. Syria’s Sunni majority continued to chafe under Allawite rule, and the Muslim Brotherhood networks there could be leveraged to organise an insurgency. Al-Adl’s logic was thus appropriated by Islamic State in 2014.
The nascent caliphate’s use of terrorism was part of a deliberate effort to deter Western intervention. Sayf al-Adl’s master plan asserted that terrorism could ‘make them think a thousand times before attacking Muslims’.[85] This work was published in 2004, likely influenced by the successful coercion applied by AQI to the Spanish in the wake of the March 2004 Madrid train bombings.[86] Viewed in this context, attacks by ISIS in Europe during the period 2014–2016 may have been intended to deter or fragment the Western coalition. This nuanced interpretation is generally absent from many analyses of ISIS, which are dominated by a nihilist view of such terror tactics.[87] ISIS’s efforts at deterrence, however, proved to have been ineffective.
ISIS sought to expand by creating a front organisation in Syria that could exploit the chaos of the civil war behind the façade of a grassroots militia. Abu Muhammad al-Jolani was dispatched in August 2011 to raise Jabhat al-Nusra.[88] Al-Jolani established cooperative relationships with other militants, emulating the moderate approach of united front tactics characteristic of Maoist Phase 1. Indeed, even the group’s name was evocative of this intention: Jabhat al-Nusra translates to ‘Support Front’ or ‘Victory Front’, terminology that is evocative of adherence to Maoist Phase 1 concepts.[89] Al-Jolani himself confirmed Jabhat al-Nusra’s origins within ISIS in April 2013 when he affiliated the group with al-Qaeda. Of note is that Jabhat al-Nusra and al-Jolani went on to form HTS, the de facto rulers of Syria following their success in December 2024.
By July 2013, Iraq had sunk into sectarian civil war.[90] It was fragile, weakened by ISIS subversion. By comparison, ISIS had consolidated control over eastern Syria and was poised to expand.
In sum, ISIS displayed a mature and evidence-based approach to orchestrating strategy that, while ultimately unsuccessful, had close parallels to ‘Communist Revolutionary Warfare’ doctrine for the effective conduct of insurgency. Its strategy of the rational pursuit of power over Sunni territories was wrapped in Salafi-jihadist robes that served to mobilise fighters to its cause, while distorting the understanding of its nature in the minds of Western military planners.
Islamic State’s Oxygen—Popular Grievances
Analysis of the emergence of ISIS has commonly recognised the disaffection of the Sunnis of Iraq. In Syria, the primary reason offered by interviewed fighters for joining the Free Syrian Army was ‘to take revenge against Assad’s forces’.[91] ISIS was able to derail the Arab Spring uprisings in certain areas by offering an Islamic identity that could compete against hated corrupt autocrats.[92] They thus offered a pathway for vengeance.
The Organisation of Islamic State
The organisation of violence is challenging.[93] Clandestine groups need to be secure but must accept new recruits, train, and support them, and coordinate their violent activities towards a specified political end. These tasks present what Jacob Shapiro termed ‘the terrorist’s dilemma’ as groups seek to strike an effective balance between control and security.[94] ISIS, and its earlier AQI organisation, were both aided by a strong core of former army and police officers experienced in clandestine organisations, estimated to be as much as 30 per cent of their personnel.[95]
Foundations in AQI
ISIS did not start with a blank slate. The organisation inherited from AQI a clandestine structure that was adapted with the benefit of reflection upon AQI’s failures of 2004–2007. Such lessons recognised the bureaucratic challenge of the ‘terrorist’s dilemma’, noting that bureaucratic AQI emirs were ‘more concerned with protecting their own human and material resources than distributing people and funds where they were needed’.[96] As AQI evolved into the ISI, the challenge of relying upon mercenary smugglers echoed al-Suri’s lessons from the failed Muslim Brotherhood uprising in Hama.[97] The organisation needed to be less reliant upon external parties and well integrated with the local population.[98]
Subversive Organisation
The foundation for the seizure of Mosul in 2014, and ISIS expansion in general, lies in the clandestine origins of the organisation. The Western focus on ISIS blitzkrieg tactics emanating from Syria is over-emphasised. By 2011, the AQI fighters in and around Mosul had been reduced to no more than 1,000.[99] By regressing from an insurgency to an underground ‘mafia-like’ organisation, it was able to raise money, ‘gather intelligence and spread propaganda’.[100] Verini quotes an interview with a family of Mosul court clerks reinforcing this view:
Jihadis infiltrated the criminal justice system, winning over lawyers and judges through religious appeals, intimidation, and bribery … Eventually all levels of the government were co-opted … ISI became a shadow government.[101]
The organisation thrived around Mosul City, and over time inserted operatives (or cadres) who were able to map local physical and human geography and develop nuanced localised tactics to exploit localised situations.[102] Termed ‘Operation Soldiers’ Harvest’, a prolonged campaign of intimidation and assassinations preceded and then complemented the ISIS assault of mid-2014.[103] Such tactics gave the semblance of a local popular uprising against Iraqi soldiers in conjunction with the ISIS external military assault.[104]
This underground organisation became a ‘skeleton’ to which the broader organisations could quickly adhere when transitioning from shadow governance to actual governance, while retaining roots within its localised conditions. These localised forces, known as the ‘Army of the Provinces’ or walis, retained their ties to local governance and continued to exist as guerrilla units and sleeper cells.[105] Johnston et al. give a technical description of this structure as an ‘M-form’ (multidivisional form) hierarchy in which ‘central management structure with functional bureaus is replicated at multiple lower geographic levels’.[106]
Systems of Governance
Islamic State’s administration grew from such shadow governance foundations. Diwans, or departments, which spanned education, health, precious resources, agriculture and defence, collectively demonstrated a level of organisation commensurate with that of a nation-state.[107] These systems of governance created micro-financial foundations through local taxation that were almost impervious to external disruption or interdiction. For example, ISIS was reportedly taxing (through racketeering) Mosulawis prior to Mosul’s seizure, at a rate of approximately US$8 million per month.[108] To place such figures in context, Miranova found that approximately US$230 per week was required for a Syrian group of 10 fighters to survive. This suggests that US$8 million per month could theoretically support up to 85,000 lightly armed local fighters.[109] Islamic State acquired further funding resources as it captured territory (including appropriated properties) and other assets that could be rented or sold to its members. Stable funding structures minimise looting and ‘shake-downs’ of local civilians, both of which fuel new grievances that undermine organisational governance objectives.[110]
Allegiance and Fragmentation
As organisations expand (particularly through the incorporation of existing parochial groups), this circumstance creates a countervailing risk of fragmentation. Territorial expansion may make it difficult to incorporate local groups while holding to a common ideology or objective, as was the case with the expansion of the Free Syrian Army (FSA).[111] Indeed, the factional divide between Islamic State and Jabhat al-Nusra, and its subsequent mergers, led to the creation of HTS. This challenge of allegiance and fragmentation influences the organisation’s ability to direct subordinates in a consistent manner, making a controlling or directive patron-client relationship more likely.[112]
The concepts of fragmentation and unification are closely related within the framework of organisational processes.[113] Rebel organisations will seek to create a ‘minimum winning coalition’ that possesses ‘enough aggregate power to win the conflict, but with as few partners as possible so that the group can maximise its share of post-war political control’.[114] To respond to this organisational challenge, ISIS went to great lengths to indoctrinate the rank and file in a highly bureaucratic manner.[115] Its objectives were to better control the newly absorbed factions and foreign fighters within their ranks, knowing that such indoctrination reduces the risk of factional splits and infighting within the organisation.[116]
Islamic State’s Competition for Control Over Sunni Populations
At first, they were nice with the people. They never asked to grow beards or not to smoke. But then they changed.[117]
During the period 2014–2018, ISIS conducted an effective campaign of control over six to eight million Sunnis in western Iraq and eastern Syria. This was effected by means of an initial intimidation campaign against opposing leaders, through a coercive form of governance over the population, and by a ‘complicit surround’ dynamic where individuals complied with what they perceived to be the majority view.
The dilemma faced by ISIS was that its ideological narrative became too effective. It had recruited Takfiri extremists who interpreted Shari’a law too literally for the cultural norms of Syrian society. Such extreme interpretation and enforcement of Shari’a disenfranchised local populations and created grievances against ISIS that it could not afford. Indeed, this situation ‘triggered a spiral of confrontation: the more ISIS increased its terror within the organisation, the more people became disillusioned and accused them of being non-Islamic’.[118]
Individuals who constituted a potential threat to ISIS power were targeted during the early stages of its campaigns to dominate an area. In Iraq, the killing of tribal sheikhs and Sahwa members claimed 2,313 members over several years.[119] The intent of such violence was intimidation—particularly to prevent a recurrent Sahwa or ‘Awakening’ from the Sunni populations of Anbar. The logic behind the violence was more than simply terrorism; it was to attrit or ‘nikayah’—to eliminate all centres of possible resistance.[120]
ISIS’s Coercive Governance
In the previous section, weight was given to the importance of organisation as it manifests in the rebel group’s own governance frameworks. In this section, we examine governance as it applies to the society the group wishes to control. This form of governance is coercive; it seeks to enforce compliance over the local population by controlling the flow of information and encouraging internal intelligence agents to denounce civilians.[121]
ISIS was able to expand by building upon the strong base of governance it had gained from its AQI roots. As it seized assets (such as oil fields or banks), the structures were already in place to prevent looting, to extract resources and channel them towards providing governance over the local population. In this context, services such as garbage collection might be prioritised to demonstrate effective government services to local populations. Even moderate governance demands organisational attention; approximately 18 per cent of the Islamic State’s personnel were assigned to governance roles.[122]
The presence of governance functions within civil society, however, should not be misunderstood as constituting effective governance. Reports were rife of mismanagement in ISIS-controlled areas.[123] The most complex aspect of governance for an organisation to achieve is the inclusion of welfare services for those under its control. It seems ISIS did not fully recognise the utility of ‘welfare as warfare’ as developed by Ansar al-Sharia, Hezbollah and Hamas.[124] To an extent, coalition military operations against ISIS disrupted focus away from governance services. In this sense, military pressure dampened a return to ‘normal’ economic activity and hence undermined the ISIS narrative of its competence in managing the governance of the Caliphate.[125]
How Islamic State Fights
The spark has been lit here in Iraq, and its heat will continue to intensify—by Allah’s permission—until it burns the crusader armies in Dabiq.
Abu Mus’ab al-Zarqawi.
Despite the identification of the Islamic State as the primary adversary for troops deployed on OIR and Operation Okra, beyond academic circles surprisingly little has been published about how it fought. This matters as the Western response to ISIS logically needs to address the strategy ISIS employs. This section maps the tactical application of ISIS strategy and forms the analytical basis on which Western interventions can be assessed.
ISIS narratives of a deliberate and progressive plan to establish the caliphate supported its strategy. The seminal work by Michael Ryan in 2013 titled Decoding Al-Qaeda’s Strategy presented the argument that al-Qaeda strategists subscribe to classic irregular warfare theory, which they termed ‘Revolutionary Guerrilla Warfare’.[126] This term refers to Maoist strategy, which evolved and was improved upon by General Giap in Indochina. Giap advocated a three-phase strategy: contention (involving infiltration, political subversion, and terror actions); equilibrium (involving guerrilla warfare, establishment of base camps and logistics caches); and the counter-offensive (involving mobile warfare to consolidate control).[127] In this context, George Tanham of the RAND Corporation observed that:
In both the strategic and tactical areas, it [this three-phase strategy] offered the Communists the greatest potential gain at the least possible risk. The initial low level of violence tended to preclude Western intervention, and at the same time involved the least risk of any possible loss of prestige for the Communists. It also enabled the Vietminh to pose as leaders of the insurgent nationalist movement and to gain popular support, while behind the scenes consolidating their power, which led to eventual control.[128]
Tanham’s analysis echoes Ryan’s presentation of al-Qaeda (and subsequently ISIS) as having orchestrated strategy based on its historical analysis of warfare, employing selective terrorist tactics to achieve specific effects.[129] Similarly, contemporary Salafist-jihadist strategy has learned from irregular warfare history. Indeed, in Abu Mus’ab al-Suri’s analysis of the failed Syrian uprising of 1979–1982, he strongly advocated that al-Qaeda emulate lessons from Communist revolutionary warfare theory.[130]
Al-Qaeda strategist Abd al-Aziz al-Muqrin assumed command of al-Qaeda’s Saudi Arabian insurgency efforts until his death in 2004. Muqrin’s legacy is a manual of military doctrine, Dawrah al-Tanfidh Wa Harb al-‘Asabat (A Practical Course for Guerrilla War), which advances a similar three-phase model, using the language articulated below:[131]
- attrition (strategic defence)
- relative strategic equilibrium (a policy of 1,000 cuts)
- military decision (final attack).
Another al-Qaeda strategist, Abu Bakr Naji, in The Management of Savagery, translated such guerrilla warfare theory for an Islamist context. Specifically, he captured the dynamic of polarising politics that can destroy social cohesion, particularly where ‘the catalyst is terrorism’.[132] Doctrinally, emphasising the employment of terror as a tactic conforms with Maoist Phase 1 subversion. During the initial stages of an insurgency, terrorism conforms with the perverted Bolshevik logic of the ‘heightening of contradictions’: when violence is perpetrated against civilians, the government is blamed for its inability to protect them, and inevitable government overreactions result from such violence.[133]
Once US forces had withdrawn from Iraq in 2010, the nascent ISIS began to apply such lessons from its AQI roots, employing a strategy that invoked Maoist teachings.[134] While remaining responsive to the social and political conditions within certain wilayats (provinces), its strategy was evocative of Giap’s micro-application of nuanced progression through the Maoist three phases.[135]
Professor Craig Whiteside explicitly concludes that ISIS’s strategy for seizing control over a target population is fundamentally the application of classic insurgency doctrine.[136] This application of an essentially Maoist insurgent strategy has been clearly explained by Aaron Zelin.[137] Zelin’s recognition of the Islamic State model, using the case of Wilayat Tarabulus in Libya, is worth quoting at length for its continuity with the strategy of revolutionary guerrilla warfare:
In the first phase of gaining control over a given area—the intelligence phase—ISIS is involved in the establishment of sleeper cells, the infiltration of other groups, and the creation of front groups … Sometimes simultaneously with the intelligence phase, other times after it, ISIS begins to operate militarily in the specific area where it is attempting to gain influence … ISIS employs asymmetric warfare, with tactics that include hit and run attacks, sniper assassination operations, drive-by shootings, improvised explosive devices (IEDs), car bombs, and suicide attacks …
The beginning of control over small pieces of territory, usually villages or neighbourhoods in larger cities, provides IS with the opportunity to commence its dawa program, in which ISIS members start reaching out to the local population … Beyond dawa, once ISIS has partial territorial control, it also begins its hisba activities... [to] make sure residents are praying on time, attending prayers, and closing their shops … The final phase preceding full territorial takeover is the start of basic governance. This primarily involves the introduction of taxes and exertion of its judicial powers …
Once ISIS has been able to gain full territorial control over a particular area … the intelligence apparatus also strives to ensure former officials and other insurgents repent and give up their weapons, and it provides a stopgap against potential fighters (especially foreigners) defecting or fleeing its territory. It helps with the suppression of potential awakening-type uprisings against ISIS.[138]
The logic of violence can be hidden by the simplistic language of ‘terrorism’ or ‘terrorist groups’. The abhorrent nature of violence directed toward civilians or ‘asymmetrically’ against military forces using improvised explosive devices (IEDs), suicide bombers or rockets confuses analysis. Using the Global Terrorism Database, the frequency, magnitude and nature of ISIS-inflicted casualties consistently demonstrates that, prior to the seizure of key cities, there is a phase of violence (generally conforming to Maoist Phase 1) of subversion, assassination, terrorism and intimidation.[139]
Where violence seems to have conformed to a Maoist strategic logic, the ISIS movement has generally been more effective. Where it has not, the movement has been less successful.
ISIS strategy demonstrated a correlation between violence and propaganda. In the seizure of Mosul, ISIS claimed that its spies were everywhere in the city and that Iraqi officials ‘would never know whether the soldiers on either side of them were loyal’.[140] Such a message resonated following almost five years of ISIS racketeering, assassinations and intimidation in Mosul, and a campaign of violence waged from June to September 2013 in and around the city. The message was therefore believable and overcame the manpower disadvantage of ISIS forces that made the Mosul campaign extraordinary: Approximately 1,300 men against the nominally 60,000-strong Iraqi Army, federal and local police defied conventional military logic .[141] Joby Warrick explains this operation well:
The city’s [Mosul’s] remaining defenders were ill-supplied, since much of the defenders’ armour and heavy weapons had been ordered to the south, to help retake Ramadi and other Anbar Province towns during the January fighting … On cue, ISIS cells based inside the city also opened up with grenades and sniper fire … within hours, columns of ISIS trucks had advanced to within a few blocks of the Mosul Hotel, where [General] Gharawi had set up his command center. At 4:30 p.m. came the decisive blow. A large water truck packed with explosives barrelled into the hotel, exploding in flames and killing or injuring many of the Iraqi force’s senior officers … The rest of the army’s defences collapsed soon after that … they seized control of Mosul’s main prison, releasing the Sunni inmates and summarily executing the others.[142]
The terror that followed the clear Phase 2 prosecution of guerrilla targets further reinforced this narrative. Punishing those who resisted (or were perceived to have resisted) helped ISIS to establish control over the local population in Mosul.
This ‘Maoist’ style pattern of violence is also evident in Syria. Prior to 8 April 2013, Jabhat al-Nusra (al-Nusra Front) was supposedly acting on behalf of Islamic State interests in Syria. The use of ‘front’ organisations further demonstrates Islamic State’s absorption of Maoist insurgency doctrine. Similarly to ISIS’s strategy in Mosul, Jabhat al-Nusra’s tactics included:
the gradual infiltration of villages and towns; the mapping of social, regional, and tribal groups (heads of clans, influential personalities, businessmen, activists, clerics, and dissidents); and Islamist indoctrination camouflaged as the opening of al-Dawa (the call to religion) offices.[143]
Following the public split of Jabhat al-Nusra from ISIS on 8 April 2013, the pattern of ISIS violence conforms to the progressive Maoist model in transitioning from Phase 1 subversion to Phase 2 guerrilla warfare from September to October 2012. In this phase, military competition dominates the frequency of observed violence, with a secondary focus towards control of local populations. To control local populations, ISIS disarmed them (to establish a monopoly of violence) while concurrently protecting such communities from criminal exploitation in the form of checkpoint extortion whenever they could.[144] A clear campaign of violence from June to August 2014 expanded ISIS’s area of control to all of Raqqa province by 24 August 2014. Following ISIS’s loss at Kobani in January 2015, a further campaign commenced in February 2015, culminating in the seizure of Palmyra in May 2015.
Summary
In 2010, the earlier incarnation of ISIS, AQI, was effectively defeated militarily with the killing of Abu Omar al-Baghdadi and Abu Ayyub al-Masri (who was Abu Musab al-Zarqawi’s immediate successor and the ISI’s minister for war).[145] Despite this defeat, AQI and then ISIS, have ‘remained’. The conditions from which insurgency grows evidently remained unaffected. The Levant has a population of 80 million, of which approximately 53 per cent are under 25 years old—a youth bulge that provides no shortage of disaffected young males, frustrated by a lack of opportunities.[146] These underlying social tensions have fuelled the growth of ISIS from its AQI roots—without addressing such tensions, there is a high likelihood of renewed emergence of ‘ISIS 2.0’ from seeds of discontent that remain in Iraq and Syria.
This chapter has focused on ISIS to understand the logic of violence it employs. In so doing, it has rejected the label ‘terrorist organisation’ as being an inadequate and counterproductive analytical basis on which to develop robust strategic counters. It is true that the concept of terrorism provided a strategic logic to support propagandising, intimidation and subversion, particularly during the initial stages of ISIS expansion. Nevertheless, the effectiveness of terrorism as a tool declined as governance obligations emerged. The fact that ISIS conformed with Maoist-style insurgency strategy or ‘Communist Revolutionary Warfare’ doctrine is an insight absent from Western responses to the ISIS threat.
Strategic Assessment
In this chapter, I extend the analysis of how ISIS fights to examine the counter-strategy adopted by the Operation Okra intervention. The power imbalance in favour of the US against ISIS meant that achieving military defeat through a concerted, deliberate Western campaign of attrition was a foregone conclusion. However, an examination of the performance of this is necessary to determine if the outcome could have been achieved more efficiently. Were military actions relevant to the political objectives intended? This question is vague but also points towards the inherent wisdom in the Obama Administration’s choice of a proxy strategy to limit its involvement. Assessing the efficacy of this choice, particularly in light of the complexities outlined above, will be relevant to Australia in any preparation for future conflicts of a similar nature.
This chapter examines the strategic guidance afforded to the Operation Okra intervention. How did the ADF approach its strategic relationships in a conflict setting? What can be derived from Australian and US military responses? How effective were the operational lines of effort? How do these lines of effort interact?
I conclude the chapter with inferences from several hypotheses regarding the way the coalition believed it could achieve its strategic objective to defeat ISIS. I use the term ‘hypothesis’ to encapsulate planning expectations: ‘If I do x, then y effect upon ISIS will be achieved’. By framing the problem this way, planning becomes a task conducted with reference to a hypothesis, informed by the way that ISIS fights. While this may be true, military planning is arguably also informed by subcultures of Defence organisations and heuristics formed by earlier experiences.[147] By explicitly examining lines of effort as hypotheses, I aim to illuminate counterproductive reasoning that might undermine future operations. In short, I argue that across all four ‘lines of operation’ identified, there is potential for improved efficiency and efficacy when engaging non-state armed groups.
The Counter-Strategy to Defeat ISIS
Four intertwined Western hypotheses emerged as central to the strategy adopted to defeat ISIS in Iraq and Syria. If they are effective, all hypotheses should function as ‘lines of operation’ that mutually reinforce the intended strategic objectives. The validity of these hypotheses will be examined in turn throughout this chapter.
Employment of Air Power Against an Irregular Adversary
What Is the Hypothesis?
Some analysts have argued that air power was critical to OIR and that constraining its employment may have extended the duration of the war. The employment of air power purportedly played a critical role in OIR.[148] Some argue that it could have played a greater role, yet the Chief of Staff of the US Air Force, General Mark Welsh, indicated that a moderated role was deliberate.[149] The role of air power against ISIS was thus orientated towards strategic cost imposition as a component of the overall proxy strategy. This accepted nuance suggests that a greater range of possibilities for the employment of air power were available to the OIR coalition.
What Evidence Suggests This Hypothesis Is Valid?
Air power was deliberately used as a type of ‘reassurance’ to compensate for the mixed quality of partner ground forces.[150] There is a sound logic to this approach in the context of a proxy strategy where advisors simply cannot be assured of the quality of their partners. Indeed, the debacle around the collapse of Mosul in June 2014 would suggest that Iraqi Army units had to be viewed as risky partners. Tactical reassurance to Iraqi partners could be provided through aerial supply drops, as was very publicly displayed in the initial Western response to the humanitarian crisis at Sinjar in 2014. The coalition’s allocation of resources to air power—which favoured reassurance in the ‘close’ fight (particularly with the provision of intelligence, reconnaissance and surveillance (ISR) capabilities)—came at the cost of having platforms available for the ‘deep’ fight of aerial interdiction, counter-finance, and strikes in depth. A tension thereby emerged that is relevant to considerations raised later in this section.
The efforts of special forces to assimilate lessons from counterinsurgency operations in Afghanistan were quickly applied to the Iraq context in 2014, resulting in the ‘strike cell’ concept.[151] A strike cell uses unclassified means of reporting target data into a classified coalition air coordination space—data that might facilitate air strikes in support of partner forces in real time. Strike cells represented a useful tactical adaptation for the conduct of proxy warfare, as they yet again provided a form of reassurance to partner forces. By January 2015, proxy warfare waged through Iraqi security forces supported by Western air power was generating an average of 1,000 ISIS fighters killed per month, a level of attrition that created sustained pressure upon the ISIS organisation.[152]
Several near-miss instances of Western platforms almost engaging Shi’a militia groups highlighted the challenges of ambiguous battlespace deconfliction processes and the utility of strong oversight and control.[153] The ever-present danger was that a strike against these Iraqi -government supported forces could very well reignite Iraqi sectarian civil violence—a strategic ‘sword of Damocles’.
Air power was used midway through the campaign against ISIS to target oil and other sources of finance. ‘The theory of victory … was that starving ISIS of resources would reduce its capacity to operate, thereby undermining its organisational and military strength.’[154] Counter-finance efforts purportedly reduced ISIS’s oil revenue by half, from $30 million per month to $15 million.[155]
When assessing the efficacy of such efforts, it is useful to consider both the first- and second-order effects. For example, did the regime’s reduced financial income result in increased taxes upon controlled populations, increasing the possibility of an uprising?[156] Were the civilians driving fuel trucks legitimate targets in the eyes of the local population if they were simply trying to make a living? Would a local population feel the same way about the legitimacy of financial targets that potentially included the banks that were protecting their personal savings? These questions have no easy answers. Counter-finance elements of the air campaign certainly eroded ISIS’s strength but may have created new long-term grievances among the Sunni populations of Iraq and Syria.[157]
What Evidence Suggests the Hypothesis of Air Power’s Efficacy Is Invalid?
The bombardment [on Mosul] was carried out by the government. The air strikes focused on wholly civilian neighbourhoods … The bombing hurt civilians only and demolished the generator. Now we don’t have any electricity … because of this bombardment, youngsters are joining ISIS in tens if not in hundreds because this increases hatred towards the government, which doesn’t care about us as Sunnis being killed and targeted.[158]
As far back as Douhet’s seminal work on the topic a century ago, air power theory has suggested that the infliction of costs through strategic bombing can impose sufficient punishment to ‘shatter civilian morale, unravelling the social basis of resistance, so that citizens pressure the government’.[159] The quote opening this section does not indicate that morale was shattered by air strikes against Mosul. Rather, the generation of hatred among the civilian populace was a counterproductive outcome brought about by the central Iraqi government and Western air strikes. While it is unclear if the employment of coalition air power sought to stimulate to a popular uprising against Islamic State, this outcome clearly did not occur. As Robert Pape identified, ‘punishment’—in the manner Douhet hypothesised—does not work, and it did not work in Iraq and Syria, as evidenced by the resilience shown by ISIS throughout 2014–2018.[160]
In the context of irregular warfare theory, the reason ‘punishment’ does not work is that civilian casualties are a source of new grievance which further fuels an insurgency. For example, there is considerable evidence to suggest that ISIS purposely sought to maximise and exploit civilian casualties from Western air strikes rather than protect people from this threat. This behaviour also speaks to the strategic attention given by Western militaries to efforts to mitigate such casualties. While difficult to assess, on balance the use of air power which characterised the Western approach to the counter-ISIS campaign was likely excessive. In this light, there are grounds to suggest that air planners need to better manage this variable in future counterinsurgency environments.[161]
The NGO AirWars estimates:
From the beginning of [Western] operations in 2014 to 8 August 2017, between 14,056 and 20,543 civilians are likely to have died in 1,995 separate reported Coalition incidents in Iraq and Syria … this estimate is radically different to the total of 603 for which the OIR Coalition assesses it has been responsible since the beginning of military operations in August 2014.[162]
The discrepancy between these reporting sources is of concern, and such numbers seem to suggest that restrictive target engagement authority (TEA) and the precondition of having full-motion video (FMV) surveillance were appropriate mitigations. In fact the opposite is true, as observed by a RAND analysis:
When TEA was delegated to lower echelons, air power was able to be more responsive and effective against small, mobile ISIS targets, resulting in improved battlefield outcomes and significant pressure on the organisation’s finances.[163]
A concerning tension emerges regarding the employment of air power:
The use of airpower … had been indiscriminate, inaccurate, and ineffective … [Yet] the coalition air campaign to defeat the Islamic State in Mosul was the most tightly controlled, specifically targeted, and precise in history.[164]
This tension is also evident in the statistics of aerially delivered munitions. In the three years of fighting to August 2017, a total of 98,532 weapons (predominantly precision-guided munitions) were employed by Western air power. Yet the initial estimates of ISIS strength indicated that there were only 30,000 fighters.[165] Either intelligence estimates were woefully inaccurate or there was a dynamic of ISIS recruiting (including through foreign fighter flows) sufficient personnel during the war to replace its losses and thereby mitigate the impact of coalition air attacks. Indeed, evidence that the coalition was engaged in a failing course of action might be suggested by the fact that 28,696 weapons were released in 2015, and 30,743 in 2016. By December 2015, and again in December 2016, there should logically have been no more ISIS targets left for the coalition to strike. It is entirely plausible that civilian casualty incidents and bombing of financial targets may have proven valuable for recruiting ISIS fighters from local Sunni populations.
Benjamin Lambeth notes that ‘perniciously’ the expectation of on-call FMV surveillance has become ‘an ironclad precondition for engaging a target’.[166] This blanket requirement is a maladaptation of the employment of air power that arose from experience in counterinsurgency contexts, such as in Afghanistan. But this requirement is ill suited to aerial interdiction against conventional warfighting tactics (such as those employed during the ISIS offensive of 2014–15). In a similar vein, the demand for on-call FMV surveillance will not be appropriate in the event of an outbreak of major power conflict, and this is a risk to which Western militaries need to be particularly attuned. Similar maladaptation was evident in restrictive TEA early in the campaign that was eventually addressed in 2016.[167]
These tactical misemployment factors almost certainly constrained the effectiveness of coalition air capabilities during early phases of the counter-ISIS campaign. This conclusion evidences a need for targeting procedures that are clear and responsive to the security situation on the ground.
Are There Other Options?
In his analysis of the air component of OIR, Benjamin Lambeth quotes an experienced F-15E pilot discussing the cost-benefit analysis of other types of air power more suitable to non-state armed groups.
Yesterday my two-ship cost the American taxpayer $240,000 just to put it into the air for a six-hour mission. That doesn’t include the cost of the base we operated out of, the tankers we got our fuel from, or the base they operate out of. We dropped a single $50,000 laser JDAM to kill two ISIS fighters manning a DShK [machine gun emplacement]. With an AT-6 or A-29, that $240,000 drops (using the T-6 cost per hour doubled) to $36,000, for a conservative saving of $200,000 … By my math, you would save enough money in a six-month deployment of AT-6s versus F-15Es to pay for the entire squadron of AT-6s at $20 million apiece. I think it is a compelling argument.[168]
Despite two decades of counterinsurgency operations, the ADF has been reluctant to adapt its Air Force capability to the operational context of non-state threats. Worse, opportunities for adaptation have been resisted, likely due to factors based in organisational culture. Drawing on the pilot’s observations, the PC-21 turboprop aircraft—which was acquired in recent years for use as a trainer—also had potential for employment in a dual-use close air support role. Alternatively, the acquisition of the C-27J (in addition to the existing C-130 capability) had unrealised potential for roll-on, roll-off gunship reconfigurability.[169]
Lambeth also points to a more fundamental question regarding the misemployment of air power when viewed essentially as ‘flying artillery’.[170] Late in the campaign, the US deployed AH-64 Apache helicopters and artillery systems to lessen the demand impost upon the air component while improving the responsiveness of firepower.[171] While airborne artillery platforms have undoubted utility, but there remains a proclivity for pursuing ‘flying artillery’ capabilities.
In parallel to the OIR timeframe, significant advances in loitering munition technology have been demonstrated with compelling effectiveness during the Nagorno-Karabakh war of 2020 and the Russo-Ukraine war of 2022 to the present. The author personally advocated for the trial and evaluation of early man-portable examples of such weapons, in both 2014 and 2017, by demonstrating that their acquisition could potentially offset the expensive use of air power for precision strike functions in urban terrain. The ADF’s position regarding such loitering munitions is not publicly clear and, to date, the technology has yet to be publicly acquired. In short, opportunities for adaptation—using innovative technologies to provide fire support to ground troops—have not kept pace with the changing character of war. This is a clear ‘missed learning opportunity’ from the Okra experience.
Regardless of firepower type, managing the airspace over Mosul was exceptionally difficult and portends future expectations of conflict. As commercial-off-the-shelf drone systems continue to proliferate, an air traffic control effect will need to be delivered at the lowest tactical levels. This reality has implications for the achievement of joint military effects that will involve military commanders at all levels of command. Tactical, joint-service complexity will be the new normal.[172]
How Should This Hypothesis Be Advanced in the Future?
In his concluding remarks about the efficacy of air power, Pape advocates for a ‘denial’ strategy against military vulnerabilities.[173] With this language Pape means that military vulnerabilities will differ based on the adversary. In mechanised warfare, this vulnerability is in logistics and communications, so air interdiction is of value. By contrast, in situations of guerrilla warfare, the vulnerability is in the reliance of the guerrilla upon the local population, so air strikes are of limited value (and may be counterproductive). This nuance is absent from OIR reporting despite ISIS shifting its methods of fighting from Maoist Phase 3 warfare (where air power is valuable) to a Maoist Phase 1–2 guerrilla warfare mode (where the role of air power is minimised).
Air power is touted as being characterised by its flexibility.[174] A lesson from the OIR campaign, however, is that air power will need to further improve in flexibility through rapid adjustments to strategic purpose, operational contexts, platform efficiency considerations, and target engagement procedures. A positive example of appropriate flexibility is the 7 February 2018 clash with Russian mercenaries in Syria. On this occasion, US air power effectively pivoted from a broader counterinsurgency environment to close air support in a conventional warfighting context—with devastating effect.[175]
Utility of Counter-Network Operations Against an Irregular Adversary
What Is the Hypothesis?
The hypothesis here is that ‘decapitation’—or targeted strikes against influential individuals in a threat network—can disrupt and degrade that network, thus reducing the threat. In a threat network, the targeting of ‘key nodes’ (leaders, bomb makers and financiers) presents an alluring policy. It presupposes that there is political utility in imposing ‘revenge’ or ‘punishment’, and that targeted strikes can deter individuals from terror or insurrection.[176] This approach is an adaptation that US Special Operations Command evolved against transnational non-state actors.[177]
What Evidence Suggests It Is Valid?
Daniel Byman notes that skills such as bomb-making are scarce—intimating that targeted killings and arrests must have an effect against an adversary organisation.[178] If placed under pressure and forced to constantly shift location to survive, leaders become less effective. They become reliant on dead-letter drops and couriers to communicate, and become isolated from other leaders. The tactic of decapitation strikes to isolate the al-Qaeda leadership in this way was used frequently by the US during the ‘Global War on Terror’ as a low-cost strategy.[179] To advocates of targeted strikes, the efficacy of this tactic was reinforced by al-Qaeda’s inability to conduct another spectacular attack on the US after 2001.
‘Targeting’ can be effected via both strike and raid. A policy decision to conduct raids, either unilaterally or with local partners, or both, accepts a much greater level of risk to the raiding force. Correspondingly, it also opens a significant opportunity for a joint force to gather intelligence otherwise unobtainable through remote sensing. For example, in May 2015, Abu Sayyaf, ISIS’s head of oil and gas operations, was killed in a US special operations raid that netted a ‘trove’ of intelligence regarding ISIS financing at a time when little was known about how the organisation functioned.[180] With this insight, US planners were able to identify the critical nodes of ISIS’s oil infrastructure.[181] Drawing on this example, benefits evidently accrue to militaries that maintain a selective capability to conduct raids with the aim of acquiring intelligence about threat organisation, finances, logistics and operations.
At the same time as the Operation Okra intervention, intense targeting of IS-KP was being effected by the US in Afghanistan to prevent the organisation taking root.[182] Indications are that this targeting was successful: ‘the months coinciding with and immediately following the targeted killings of IS-KP emirs witnessed some of the lowest numbers of ISIS-K attacks’.[183] IS-KP also moved quickly to secure funding from the narcotics and illegal logging industries as it tried to establish in Afghanistan.[184] IS-KP replaced its losses by recruiting militants from other organisations, which increased the potential for it to drift towards more radical views and thereby lose tactical control of its membership.[185] To illustrate this point:
In April [2017], Rangers and Afghan special operators landed at a site in Nangarhar, attacking a Daesh command post in a raid … Among the insurgents killed was the governor of the Islamic State’s Khorasan Province, an Afghan veteran of the war in Syria … The killing precipitated a succession crisis within Daesh’s Afghan branch, which the JSOC task force took advantage of, searching out and killing as many likely candidates for the governorship as it could as quickly as it could … On August 11, working its way down the Islamic State hierarchy more quickly than the group could appoint new governors, a strike in the central Pech killed four more of its leadership figures.[186]
In other words, targeted killings can be effective but this strategy can also carry the risk of increasing radicalisation within the target organisation. Further, such efforts may actually make that organisation more resilient if it is able to capture a broader base of revenue streams.
What Evidence Suggests It Is Invalid?
Osama al-Bilawi, also known by the nom de guerre Abdul Rahman al-Bilawi, was the head of ISIS’s military council until he was killed several days before the fall of Mosul in June 2014.[187] Despite the importance of al-Bilawi, ISIS functioned magnificently in subsequent weeks. Indeed, by 2015 almost all the Camp Bucca veterans (who were the core of ISIS leadership) were dead, yet the organisation was still thriving.[188] These data points suggest that special forces-led ‘targeting’ strategies are not a silver bullet.
Air power theorists consider there to be an overlap between counter-network approaches and Warden’s so-called ‘Rings’ theory, from which the ‘decapitation’ strategy is derived. This theory of victory has been pursued by the US through the pairing of precision-guided munitions and unmanned platforms and has dominated the US approach to countering terror networks. Pape argues, however, that ‘decapitation does not work’.[189] Evidence from Israel’s decades of decapitation operations and the experience of OIR reinforces but adds nuance to this assertion; decapitation can contain and degrade but cannot defeat.[190]
The flaw in decapitation theory is rooted in misplaced belief in its efficacy. Specifically, it presumes that decapitation forces leadership figures to take greater precautions—making them less effective leaders—and in this way degrades organisational effectiveness. But there can be an unintended consequence of this tactic. Specifically, since clandestine organisations require effective leadership to manage violence toward political ends, if decapitation removes such leadership, the organisation loses capacity to effectively implement strategy, and violence becomes less restrained. As a result, civilian casualties can rise and polarisation of the targeted organisation can increase in parallel. This situation can lead to defections occurring, negotiated settlements becoming less likely, counter-militias mobilising, and the associated rise in retributive violence. Therefore, decapitation may unleash a chain of events that results in the conflict becoming less ordered and more entrenched.[191]
An example of the unintended consequences of a decapitation strategy can be found in events that unfolded in Syria in 2014. On 9 September that year, Ahrar al-Sham, a Sunni Salafist movement in north-eastern Syria (with which Jabhat al-Nusra would later merge and eventually become HTS), was targeted by an explosion—the cause of which is unclear—during a top-level meeting,[192] killing 28 leadership figures and 46 people in total. Decapitation theory would suggest that such a significant blow would have an overwhelming effect upon the organisation of Ahrar al-Sham. Yet second-tier commanders were quickly advanced and the organisation continued to operate almost unaffected, albeit exhibiting a more extreme Salafi position over the following months.[193] Noting the rare occurrence of strikes killing more than one leadership figure, this vignette of minimal effect—despite 28 leaders having been killed in one event—should prompt reconsideration of decapitation theory.
While discussion has thus far focused upon the efficacy of targeted strikes, a moral question also arises as to whether such operations constitute ‘assassination’. Like the term ‘terrorism’, ‘assassination’ carries a reprehensible tone, particularly in the US following the Church Committee deliberations of 1975. The line becomes very blurry indeed when examining the 3 January 2020 strike that killed Major-General Qassim Soleimani and Deputy Commander of the Iraqi Popular Mobilisation Forces Abu Mahdi al-Muhandis.[194] The evidence of Muhandis playing a role in the 1983 embassy attacks in Kuwait and Soleimani in supporting terrorist organisations raises a vexed question—is it morally, ethically and legally acceptable to assassinate certain people? This is an awkward policy conversation that those engaged in targeting operations must reconcile.
The employment of air power for decapitation strikes may advance strategic objectives through disruption. It may nevertheless be, at times, over-resourced and over-zealously pursued, thereby creating counterproductive effects. The issues outlined above suggest that Western forces would do well to further scrutinise the military efficacy of targeted strikes as a strategy employed against the leaders of its adversaries.
Are There Other Options?
When targeting moves beyond ‘decapitation’ of individuals to accumulated pressure against a network, counter-network strategies are seemingly more effective. A case study of Task Force 714 in Iraq from 2004 to 2006 indicated that an innovative ability to ‘outpace’ AQI’s ‘capacity to adapt’ proved critical to the network’s collapse.[195] Similarly, the adaptive responses by IS-KP to US targeting proved ill suited to the Afghan context of 2015. The lesson of network targeting efforts over the past 20 years is that overcoming (or rendering inappropriate) the adaptive responses of a network may be a more effective tactic than targeted ‘decapitation’ of individuals. This statement requires nuance, as a network’s adaptive capacity might also be overcome using decapitation tactics; a prominent example is the 2024 Israeli attack on Hezbollah involving the simultaneous explosion of hundreds of handheld pagers and radios.
How Should This Hypothesis Be Advanced in the Future?
Moving forward, it is important to distinguish deliberate, intelligence-led strikes from close air support (as was examined earlier). As we have seen, in an insurgency environment (particularly within urban terrain), the risk of civilian casualties may render overwhelming firepower in the form of artillery and air strikes counterproductive. Further, by examining the maturity of the target organisation, it is possible to assess the utility of air power as an offensive tactic. Fragmented or parochial organisations have loose connections and are more vulnerable to decapitation strikes than those that are more integrated and that have a ready pool of subordinates prepared for promotion into leadership appointments.
Overcoming an opponent’s capacity for adaptive response requires a military to generate tempo, and tempo demands a sound appreciation of targetable elements of the network, alongside an understanding of the strategy that the adversary is pursuing. Ill-considered or collateral damage might aid the adaptive abilities of the network by radicalising new recruits. This being the case, a critical capability for militaries is their capacity to expedite the exploitation of intelligence gathered, particularly human intelligence. Overall, patience at the tactical level becomes essential to enable strategic-level decision-makers to develop sufficient understanding of the targeted organisation to effectively conduct targeting campaigns.
Proxy Warfare and Principal–Client Relationships
As we have identified, a proxy warfare strategy was central to the objectives of OIR, but proxy warfare is an ethereal concept. What differentiates, for example, the Iraqi divisions that crumbled in Mosul in 2014 from those that engaged in intense fighting in Mosul in 2017? Both were, after all, influenced by Western advisors. It is difficult to confirm the causal link between the operational performance of proxies and the provision of external advisory support. But long-term analyses of Western-led missions conducted in the first part of this century urge caution; they suggest that US covert efforts to ‘arm foreign militias had only negligible impacts on conflict outcomes’.[196]
What Is the Hypothesis?
This hypothesis holds that a patron state can develop the capacity of a partner to fight and achieve strategic ends on its behalf. Most studies of proxy war focus on the interests of outside sponsors and the degree of control they hold over their proxies. While this is an important issue, such analyses tend to miss the other side of the story: specifically, how such outside interests interact with civil society on the ground. This may include aspects such as pre-existing political currents, economic interests, cultural mores, religious practices and, above all, the mosaic of friendships and rivalries that help form the fabric of everyday life.[197] This hypothesis is complex indeed.
In irregular conflict, efforts by a military force to impose coercive control over a population may spawn new militias. Such an outcome may occur when excessive or illegitimate violence against civilians prompts them to recognise their need for protection.[198] For example, the Syrian regime’s employment of Shabbiha (ghost) militias as a proxy force to re-exert control over certain areas resulted in the emergence of local neighbourhood militias to protect their constituents from such groups.
When an armed group or military force uses excessive force, it can create further deprivation within the community. This situation can result in the conflict being perpetuated as new militia organisations emerge in opposition to it, often based around local (e.g., neighbourhood or familial) networks. Volunteers within such groups are mobilised by the motivation to ‘protect my family, my village, and my community’.[199] In this environment, armed organisations will compete with such localised militias through either direct conflict or, where similar ideologies exist, assimilation. Indeed, this was a common method applied by ISIS. Assimilation of local militias affords a broader organisation the local knowledge to better understand and therefore control the population. Proxy strategy leverages such local knowledge to the benefit of an external party.
What Evidence Suggests It Is Valid?
The strategy of proxy warfare is a logical option when power imbalances preclude competing nations from escalating along the spectrum of conflict. During the Cold War, for example, the ultimate threat of ‘mutually assured destruction’ provided a strong incentive to constrain the vertical escalation of tensions between protagonists into direct conflict.
In more recent times, the potential political and military costs to Western governments of intervening directly in yet another Middle Eastern or African conflict may encourage policymakers to pursue small-footprint military options involving proxy agents to achieve their strategic outcomes. In this regard, several Western governments are still smarting from the often-quoted figure of US$1 million per soldier per year cost of direct intervention in Afghanistan. A strategic climate of multipolar competition between Russia, Iran and the US has emerged within the Middle East since 2011 based on their proxy support to various armed groups. The use of proxies in this way has enabled these major powers to constrain warfare by avoiding vertical escalation that could ultimately demand direct military intervention.
Why Do Irregular Organisations Pursue Proxy Relationships?
Proxy relationships are two way. While an external patron may believe that they are leveraging a local client to act to the benefit of the patron, a client will almost always act in its own interests. External sponsorship may confer legitimacy to the movement and its cause; state sponsorship may bring military expertise that can enhance the effectiveness of rebel fighting forces; and the knowledge of state sponsorship may deter the opposing party from expanding the war. Given these realities, militaries and strategic policymakers must understand the agent’s localised interests. By seeking external support, an irregular organisation is taking a risk. It cannot afford to fragment or to lose local support by being seen as a patsy or puppet of an external state—particularly where a post-colonial or nationalist narrative exists. As recognised in most literature on proxy warfare, achieving alignment of interests between patron and proxy is of paramount importance.[200]
What Evidence Suggests It Is Invalid? Challenges in Developing Strategy Employing Proxy Relationships
A key challenge to implementing strategies involving proxy relationships is that organisational interests can change over time. Nascent organisations (also termed movements or fragmented organisations) will typically rely upon pre-war social networks. Such measures help maintain trust among members and enable nascent organisations to generate sufficient strength to exercise centralised control over their operations.
As a corollary of their centralisation, nascent organisations are susceptible to manipulation by outside interests.[201] Any effort by external actors to manipulate such groups, however, must be handled particularly shrewdly. Emerging organisations will inevitably be driven by local interests. This is a simple reflection of the social embeddedness of the local actors who drive these organisations: they need to recruit and solicit information, food, shelter and other resources from the local population and must compete for factional allegiance. These requirements demand legitimacy in their cause—a challenge when a group acts, because of external pressure, in ways that are inimical to local interests. Managing this tension is a key requirement of any successful strategy of proxy warfare.
What Was the US Approach to Proxy Warfare in Iraq?
We didn’t try to make them in our image … we took the Kurds for who they were.[202]
The US has a long-term relationship with the Kurds, yet it hesitated to provide wide-ranging support for them due to Turkey’s political interests. Turkey viewed armed Kurds as factions of a terrorist group, the Kurdistan Workers’ Party (PKK).[203] As the opening quote for this section suggests, the limitations imposed by such realpolitik beneficially affected how the US engaged the Kurdish People’s Protection Units (YPG). Specifically, unlike the case with capacity-building efforts in Afghanistan and Iraq over the 2000s, the US accepted that the Kurds had significant agency (as per their de facto state structure in northern Iraq). This recognition influenced the US proxy strategy for using this ethnic group in both Iraq and Syria.[204] Overall, the US recognised that support for the Kurds risked inflaming Arab–Kurdish and Kurdish–Turkish tensions. Accordingly, the relationship was managed particularly carefully by the US at the political level.
General Dunford, the Chairman of the Joint Chiefs of Staff, described the variables evident in the relationship the US government was expanding with Kurdistan’s Barzani government, particularly regarding the provision of weapons and ammunition to Kurdish forces. Prior to the provision of such resources, an assessment of Kurdish military capability informed US assessments as to the likelihood of the Kurds being able to positively influence the broader campaign.[205] Testimony to the Committee on Armed Services identified that the Defense Authorisation Bill of November 2015 was also required to provide arms directly to the Kurds or Sunni tribes.[206] This bill was framed around the premise of a non-inclusive government of Iraq but involved the erosion of the Weberian norm of a state holding a monopoly of violence. This is an important precedent that requires consideration before such legal provisions are adopted in other contexts.
What Was the US Approach to Proxy Warfare in Syria?
In Syria, pre-war social networks differed in nature from those in Iraq. This meant that the goals of patron states, and their capacity to exert influence, differed too.[207] In April 2012, Saudi Arabia and Qatar entered into a support agreement to fund Free Syrian Army salaries and provide logistical support.[208] Support was initially tailored to encourage further defections from the Syrian Armed Forces. Over time, divergence in proxy interests stratified: Saudi Arabia supported Salafists, the United Arab Emirates supported secular liberals, and Turkey and Qatar supported those with Muslim Brotherhood orientation.[209] The strength of pre-war Salafist and Muslim Brotherhood organisations was unsurprisingly a factor that contributed to their better rebel performance compared to that of emergent organisations.[210] Meanwhile, the US did not grant approval for the provision of non-lethal aid to what would become the Syrian Democratic Forces (SDF) until February 2013, at which time CIA vetting struggled with the proliferation of actors and interests. In these early stages, ‘U.S. policy fell victim to paralysis through analysis’.[211]
Ash Carter quotes President Obama concluding that the error was ‘more in conception than execution’.[212] Carter distils the error as being due to ‘the requirement for ironclad assurances to Congress that troops we trained and armed would fight only ISIS, and not engage in the bloody civil war to unseat Bashar al Assad’.[213] This was a naïve policy limitation that neglected the agency inherent in any proxy relationship. Such guarantees are almost impossible to provide.
In 2015, the United States started training and arming Syrian fighters to fight against ISIS … But because fighting against the regime was the main goal of almost all Syrian fighters, this program was not successful, and out of the 1,500 who passed the first stage of selection, only 200 fighters actually started training … They [those who defected] saw Jabhat al-Nusra not only as a group that shared their own goal (fighting Assad) but also as the most effective group; they could make the best use of weapons and trained fighters. As a result, there was absolutely no reason for them to fight Jabhat al-Nusra.[214]
Ultimately, US efforts to engage in the Syrian civil war lost the initiative to other actors. Instead of providing direct support to any of the hundreds of anti-Assad militias, the Obama administration reportedly worked in conjunction with the Saudis to collaboratively support CIA-trained rebels (Operation Timber Sycamore).[215] If such reporting is accurate, this represents a concerning repeat of the flawed operational construct of Operation Cyclone, the training and equipping of the Afghan Mujahideen of the 1980s where aid was channelled through Pakistan and was prioritised according to Pakistani interests.[216] The Timber Sycamore model was executed with allegations of Saudi and Qatari ‘double-dealing’ by providing ‘financial and logistical support to ISIL and other radical Sunni groups in the region’.[217] The ultimate failure of US efforts to support moderate Syrian rebels suggests the seeds of failure lay in the compromises the US made, and its failure to heed the lessons of past proxy wars.[218]
In sum, the evidence presented suggests that the US strategy for proxy warfare in Syria was a failure—yet the need to avoid future proxy strategies would not be a fair lesson. The overall success in militarily defeating ISIS entailed proxy force relationships—with the Iraqi military, Kurdish militias and numerous Syrian forces—which are yet to be declassified or examined in a public forum. The ADF similarly executed a proxy strategy via its training of Iraqi military personnel at Taji and its capacity-building efforts with the Iraqi Counter-Terrorism Service. On balance, the concerns raised in this section indicate that errors in executing a proxy strategy were clearly made, and that arguably these errors could have been avoided.
Are There Other Options?
To influence your insurgent proxy you need to be there on the ground with them, earn their respect, support them, and demonstrate your ability to improve their chances of success. You do not buy allegiances, you can only rent.[219]
Proxy warfare can be regarded as an attractive policy option by political decision-makers because it may be seen as low cost. There is a risk, however, that the implementation of proxy strategies is conflated with that of other, higher-cost military options that are available to a government—that it owns and that it can direct with confidence. Specifically, it may be easy to forget that ‘low cost’ also means ‘limited control’. By engaging in proxy warfare, decision-makers are (metaphorically) sailing with the shifting winds and tides of client interests. Where competition exists between patrons for the loyalty of a client, proxy strategy needs to be attuned to the nature of support offered by other competitors. For example, in Iraq a significant issue was the perception of Iran’s exploitation of Western military power to advance its political interests. Indeed, approximately two-thirds of the Popular Mobilisation Forces (PMF) militias in Iraq in 2018 ‘shared close links with the IRGC [Islamic Revolutionary Guards Corps]’.[220]
There is evidence that throughout OIR the coalition was attuned to the risk of Iranian influence—certainly in the early stages of the campaign. In early 2015, for example, US air power was withheld until Shi’a militias were sidelined from operations in Tikrit.[221] Ultimately, however, Iraqi forces (which included the PMF) reclaimed the city in April 2015. This operation was highly controversial with ‘many residents in Tikrit reporting that they feared the liberating force as much as ISIS’.[222] So why did the US not address the issue of PMF involvement in Iraqi-led operations rigidly and consistently? The answer is that the pressure the US felt to generate tempo against ISIS may have led to its withering willingness to hold the Iraqi government to account for the actions of its PMF (and their IRGC mentors).
Strategies that involve withholding military capability from a partner or potential partner are inimical to Western military culture. To bargain in such a way seems callous and morally fraught. Viewed in context, improving the patience of tacticians in Western militaries—to provide sufficient space for strategic decision-makers to use such levers of influence—is a lesson for future proxy wars. In the context of this paper, the Iraqi proclivity to use the non-sectarian Counter-Terrorism Service (CTS) (i.e., the preferred Western proxy force) as an operational spearhead inevitably resulted in significant attrition to this force. One could view the Iraqi Shi’a-aligned politicians’ decision to use the CTS this way as an effort to counter Western influence.
In this section, we have considered the strategy of proxy warfare in Syria and Iraq in an effort to inform future Western military interventions. The US experience of proxy support in these operational theatres demonstrates the challenges of achieving political aims through proxy warfare when tactical operators are guided by ill-informed or inappropriate strategic guidance. As has been seen, proxy relationships within competitive strategic climates can extend the duration of conflict, with resultant increases in civilian casualties and other disruptions to civil society.[223] To elicit support, rebels posture to exploit patron concerns around the broader balance of power, and this can have unintended consequences for the patron state.
The Mechanism and Utility of Information Operations or Influence Effects
What Is the Hypothesis?
The hypothesis inherent in Operation Okra was that Western information operations could influence Sunni populations in Iraq to enhance the legitimacy of the Iraqi government. This hypothesis draws on David Galula’s recognition that competition for control over the population is about perception.[224] In other words, who does the local population believe to be ascendant and legitimate? How might a local population shift its views regarding a rebel organisation? How might elements of an ambivalent majority be engaged to be at least sympathetic to government aims, if not actively involved?
Who Does the Local Population Believe to Be Ascendant and Legitimate?
Fontini Christia examined the organisation of a ‘minimum winning coalition’ that influences alliances and fragmentation, and concluded that the primary consideration here is perception: the perception of who is likely to win because of relative power.[225] To reinforce their stature, rebel organisations seek to communicate narratives that reinforce their power. Indeed, ISIS did exactly this with their publication Dabiq in July 2014.
While insurgent groups may seek to generate a perception of relative power, research by Walther and Pedersen identifies that fragmentation of such groups is quite common, since approximately ‘44 percent of armed opposition movements engaged in 114 civil wars since 1989 experienced fragmentation’.[226] Further, they identify that the ‘probability of infighting between rebel organisations is significantly higher when they are engaged in areas with drug cultivation … and when groups receive material support from foreign states’.[227] Possible reasons for this may be actual or perceived corruption within the organisation, as resources are diverted for personal use or to ideological or ethnic kin. Knowing these characteristics of insurgent organisations, foreign forces can capitalise on this awareness to, for example, undermine the perceived legitimacy of the insurgents. For example, rather than destroying oil wells, forces might achieve a greater disruptive effect by cultivating a perception within the community that the emir controlling the oil well is corrupt. Equally, a patron seeking to financially disrupt a client might choose to do so quietly, thereby enabling a perception of internal embezzlement rather than external sponsorship. The possibility of misinformation or disinformation in this context should be evident.
The objectives of military information operations must be appropriately nuanced to account for variations in political views held by members of the civilian population. For example, in his analysis of the Algerian insurgency, Galula coined the term ‘ambivalent majority’ to recognise the diversity of target audiences in a population. There will be a small segment of a population that is pro-government, yet uncommitted. These people are likely to be willing to provide information on rebels operating within their communities. To capitalise on their potential as informants, such individuals need to be defended from adversarial subversion, intimidation and propaganda. While such pockets of informants might change their political views over time, they are unlikely to become more than quietly pro-government in their sympathies. By contrast, those who are pro-rebel in their outlook but have not yet committed to the insurgent’s cause may initially be used by an irregular organisation as its auxiliary. Over time, the rebel group will escalate its expectations of such sympathisers in order to entwine them into the movement.[228] Finally, there will be committed pro-rebel elements within the population. Such individuals will not respond to government propaganda; they can only be influenced to become disillusioned with the rebel organisation and its practices. While communication with this group should point out that rebels are manipulating civilians, in the short term foreign forces cannot hope to shift such groups beyond becoming neutral. To help inform planning for information operations and targeting, the audiences and information objectives are shown in Figure 4.1 below.
How Might a Local Population be Influenced to Resist Adversarial Control?
The hypotheses examined in this chapter are interrelated. All actions create information effects. Indeed, in a hyperconnected environment, one cannot not create an information effect. A misplaced bomb does not produce ‘collateral damage’ in the eyes of the family that has now lost a mother or daughter. It conveys ineptitude, ambivalence or callousness on the part of the military coalition. Conversely, discriminate targeting reinforces an information effect of omnipotence, with due concern as a protector of the local population.
When seeking to work through a proxy force, such information actions are critical. In World War II, the British Special Operations Executive (SOE) worked through Hungarian, Bulgarian, and Romanian proxies to erode German support, with an aim of separating one or more of these Axis allies from supporting Hitler. This political warfare strategy had the most to gain in the context of Romania, due to the importance of the Ploiesti oilfields to the German economy. To ‘promote resistance’ and possibly bring targeted countries out of the war, bombing missions were conducted between November 1943 and April 1944.[229] The result was the exact opposite of that which was intended. In Bulgaria, ‘the bombing unified the Bulgarian people against the Western Allies and drove them towards their old allies, the Russians’.[230] In Romania, SOE teams faced a hostile population that would not support and hide them from Axis authorities, and active surrender negotiations between the Allies and the Romanians were paused for a period of 10 days following a particular bombing raid.[231]
This World War II vignette has echoes in US-led military efforts against ISIS in recent years. In 2014, there was a strong perception that ISIS would face local uprisings in Mosul, and elsewhere, because of its draconian policies. Local acts of civil resistance intimated the potential for insurrection.[232] Indeed, in Mosul, up to 62 per cent of survey respondents reportedly engaged in some form of non-cooperation against ISIS and 22 per cent engaged in high-risk activism.[233] Yet the population of ISIS-controlled western Iraq and eastern Syria remained generally acquiescent. Why? As with the SOE vignette, the information effect in OIR was not synchronised with efforts to cultivate civil resistance. While coalition dominance was being claimed, civilian casualties and extensive urban damage were occurring simultaneously. Being alert to this tension is a lesson for future conflicts.
Lessons about Influence Operations from Operation Okra
Recognising the importance of influence actions taken by military forces is a key outcome from OIR and Operation Okra. All battlespace actions create information effects, and they can be easily manipulated. This was the case with Western support to the Iraqi government to roll back ISIS forces outside the Iraqi town of Amerli in August 2014. Despite massive Western humanitarian airdrops to the town itself, and air strikes against ISIS forces, Iranian Major General Qassim Soleimani went to Amerli in the role of liberator.[234] The Western narrative was lost for lack of access and placement.
When all actions have an information effect, the challenges of centralised TEA are exacerbated and the importance of delegated authority comes to the fore. It is curious that throughout OIR and Operation Okra, information actions (which generally do not have lethal effects) were centrally controlled, unlike strike TEA, which was delegated over time (and proved to be more effective as a result). This makes little sense. To be operationally relevant, TEA for a tweet should not be held higher than that for a bomb. Indeed, Lieutenant General (Ret.) Mike Nagata, the first commander of US military operations with Syrian proxies, speaks persuasively about the sophistication of Iranian information operations compared to US influence efforts.[235] This is an area in which Western forces can, at relatively low cost, improve capability.
Summary
This chapter has examined the strategic guidance afforded to the Operation Okra intervention. From this, several hypotheses have been raised to generate a conceptual bridge between tactics and strategic policy. In the next chapter, the paper considers what lessons the ADF should draw from the Operation Okra experience.
Implications: What Lessons Might be Drawn from Operation Okra?
In 2007, the US ordered a troop surge in Iraq led by General Petraeus to defeat the Iraqi insurgency. While its results were disputed, the surge is credited by many as contributing to a decrease in violence within the country. The success of this effort points towards the US having learned hard-won lessons about what happens when irregular warfare is inflamed by external sponsors. Ostensibly focused around a ‘hearts and minds’ campaign, the surge suggests a deeper dynamic to counterinsurgency than this platitude would suggest. While abuses from AQI did disenfranchise the Anbari tribes, resulting in the Sahwa (Awakening), there is more to this dynamic. Multiple Sunni tribal uprisings occurred in Anbar before the tipping point of 2007 turned the war around.[236] Biddle et al. found that:
Evidence suggests that a synergistic interaction between the surge and the Awakening is the best explanation for why violence declined in Iraq in 2007. Without the surge, the Anbar Awakening would probably not have spread fast or far enough. And without the surge, sectarian violence would likely have continued for a long time to come—the pattern and distribution of the bloodshed offers little reason to believe that it had burned itself out by mid-2007.[237]
Irregular warfare that engages non-state armed groups is complex. Yet nuance is absent from contemporary Australian defence policy, indicating that there is still much to learn from the past 20 years of international warfare.
This chapter concludes by questioning what lessons might be drawn from Operation Okra. Recommendations are made in the context of a contemporary strategic narrative that asserts the existence of a ‘new’ era of major power competition. Ironically a similar global political climate was already playing out in the broader Middle East during Australia’s Operation Okra deployment.
Situating the Competition
ISIS posed a vexing challenge, as it was neither a true state nor solely a terrorist organisation but possessed attributes of both … ISIS’s hybrid nature made it difficult for the coalition to immediately discern its key pillars of strength.[238]
The Western proclivity to categorise contemporary conflict as ‘regular and irregular’, ‘conventional and unconventional’ or ‘domestic and offshore’ inhibits the crafting of suitable policy responses to contemporary strategic challenges. Broad acceptance of the view that today’s geostrategic environment is characterised by heightened competition ignores the fact that the recent past has also been distinguished by competition. For example, ideological competition is at the core of struggles between Salafism and Western democracy.[239] The past 20 years has seen competition between Sunni and Shi’a influence in the Middle East (manifest predominantly through Saudi Arabian–Iranian tensions), and between Russia and the US for influence globally.[240]
These struggles have the effect of deliberately limiting the vertical escalation of nascent tension into direct and open conflict. Instead of competing openly with one another, states use proxies to impose costs, shape perceptions, and deter adversaries. Indeed, it is poignant to consider that the Islamic State could likely have been quickly defeated militarily by the US and its allies through direct intervention, yet the US deliberately chose not to do so.
In simple dollar terms, the Department of Defense estimated that the cost to the US defence establishment of operations against ISIS to September 2017 (around the time of the fall of Mosul, and hence close to the complete military defeat of ISIS in Iraq) was approximately US$14.3 billion.[241] By comparison, the direct costs of the Iraq War from 2002 to 2010 (around double the time commitment) amounted to approximately US$800 billion. The proxy strategy pursued against ISIS was therefore relatively cheap for the coalition compared to the direct Western interventions that have occurred over the past two decades.
Policy Implications
Colonel John Boyd, who coined the OODA (Observe-Orientate-Decide-Act) loop, argued that there should be a progression of ‘people, ideas, machines’.[242] Much of Boyd’s work is orientated to the concept that, to be successful, ideas require a strong foundation in people. In the Australian context, Boyd’s thesis raises several questions. For example, who will lead development of Australian proxy warfare policy? Who will frame Australian influence policy? How does the ADF develop people with the capacity to work effectively with proxies? Indeed, who are Australia’s future strategists who might more effectively address all four hypotheses examined in this report? The challenges posed by simply asking ‘who’ point to challenges within ADF structures and processes.
In the US Department of Defense, the Goldwater–Nichols Act precipitated the elevation of the US special operations capability to a service-like stature. On the civilian side of Defense, the Office of Special Operations/Low-Intensity Conflict (SO/LIC) reports to the Secretary of Defense regarding special operations and irregular warfare related issues.[243] Thus, in the US Department of Defense there is a prominent bureaucratic basis upon which senior Defense leaders are exposed to appropriate expertise concerning irregular and proxy warfare. The IRGC-QF likewise has a position of influence within the Iranian military establishment.
The bureaucratic accessibility of such advice within the Australian Department of Defence is questionable by comparison. Recall that publicly available Australian Defence policy has been silent regarding irregular, proxy or unconventional warfare topics since 1976, despite a trend towards the increasing frequency of this type of conflict. The Operation Okra experience may point to the need for a SO/LIC-like function in the service of the Secretary of Defence to draw from and to better understand the nature of ‘grey zone’ competition through proxies. Regrettably, given the recent proximity of the conflict, opportunities for contested analysis are constrained by the paucity of unclassified primary source materials available. Most reporting regarding strategic decisions, operational frameworks, and tactical partnerships with irregular partners remains of a classified nature.
The provision of support to an irregular actor may become mired in a political decision to designate it a terrorist designation. Initially we might think this statement absurd, but Kata’ib Hezbollah was designated a terrorist organisation by the US despite the fact that it was recognised as a PMF by the Iraqi government and therefore fought alongside the Iraqi Army, police and CTS forces against ISIS. Managing the complex interactions between organisations regarded as having a legitimate political basis and those with terrorist tendencies was foremost in the mind of Western planners during OIR. Considering this challenge from the perspective of a potential adversary is a question for future policy deliberations.
Despite the complexities, the capacity to legislatively designate a terrorist organisation is a powerful lever.[244] The ability to impose travel bans and disrupt financing are authorities available to a state that can markedly aid counterinsurgency operations, and can be particularly useful in efforts to disrupt foreign proxy warfare. The strategic rationale for such legal, financial and political sanctions is also straightforward and longstanding—to reinforce the global rules-based order. This rationale is enhanced where there is evidence of organisationally sanctioned violence toward civilians. While ‘terrorism’ remains a term that is difficult to define, the wide-ranging applicability of the language provides a powerful tool for Western governments seeking to disrupt adversarial proxy relationships. Given the challenges posed by contemporary proxy warfare as a component of strategic competition, there may be a basis for expanding ‘terrorist’-related legislation to include elements of ‘state-sponsored terrorism’.
Ultimately, the requirement for overall clarity regarding where the authority vests for developing proxy relationships, and engaging in proxy warfare, demands a policy response. Assigned authorities, possibly from an Australian SO/LIC-like office, must address the Defence White Paper policy gaps highlighted at the commencement of this paper. Some might argue that such policy guidance belongs in classified annexes or separate classified guidance. Indeed, robust direction might already exist in this domain. Still, the absence of such policy guidance at an unclassified level constitutes a failure to address the considerations of strategy to satisfy the Australian public demand for clear links between Australia’s political interests and its military actions. In this regard, it is notable that the unclassified US National Security Strategy of 2020 included an irregular warfare annex.
Authorities to Work with Proxy Forces
Policy guidance will logically need to identify which agency is authorised to establish a relationship with a proxy force. This poses an important policy question: who makes the decision about partnership? An irregular actor is not a nation-state. If it were, there would be an argument for the Department of Foreign Affairs and Trade to make such decisions. When considering the employment of a 30-man militia in a limited war zone, however, timely decision-making cannot be achieved if authority vests at such a highly centralised level. Consideration might instead be given to whether the intelligence community should lead in this regard. Such a proposition raises questions, however, about the nature and purpose of the proxy relationship. What if intelligence is only a minor effect that such a partnership generates? If the primary purpose of a proxy relationship is to conduct counterinsurgency operations, then an intelligence lead might be illogical. In short, the very lack of clarity about such questions points to the need for Australian Government policy to clarify which authorities exist when the ADF is engaged in irregular conflicts that involve myriad non-state actors.
Without clear policy guidance concerning lead agencies and relevant authorities, Australian Government decision-makers, including members of the ADF, are inhibited from working confidently with like-minded partners. The absence of such mandates is odd given the political importance Australia places upon defence industry, which might be empowered with greater transparency around bureaucratic processes that could be leveraged to equip partner forces.
The provision of aid, particularly when it escalates to the provision of lethal aid to proxy forces, is fraught with political risk. The transfer of military equipment needs to be funded, tracked and maintained. The political pitfalls of TOW anti-tank missiles falling into the hands of al-Qaeda-aligned Jabhat al-Nusra are paradoxically a greater risk if advisors are prohibited from working with like-minded forces. Thus, risk to force must be accepted to mitigate strategic risk. Conversely, the checks and balances imposed by Defence bureaucracy pose challenges to tactical commanders seeking to recognise and seize opportunities to provide low-risk aid (such as small arms and ammunition) to newly established partners. Accordingly, any policy framework established by Defence must include authorities that allow for funding of and logistical support to such operations. In the context of the emphasis in the 2024 NDS on the challenges of national mobilisation, there are grounds to consider an expanded concept of ‘war stocks’ that could also be used to equip partner forces should the need arise.
Mandates Regarding Proxy Warfare
The US has adapted strongly to proxy warfare challenges over time. Specifically, its special forces capability, orientated to this type of mission, was an adaptation to Cold War competition mandated by President Kennedy.[245] In the context of more recent counterinsurgency operations in Afghanistan and Iraq, the US Army has now raised regionally orientated Security Force Assistance Brigades. Such structures drive manning requirements, with the associated requirement for specialised capabilities among personnel filling such roles.[246]
A lesson for Australia from recent operational experience, including from Operation Okra, is the need for structures and personnel to perform a proxy warfare or advisory role and the fact that such personnel cannot solely exist within Special Operations Command.[247] Within an Australian strategic context that is orientated to South-East Asia, historically dominated by ‘small wars’ or insurgencies, greater knowledge of, specialisation in and preparedness for proxy warfare are evident requirements.
When considering efforts to constrain adversarial proxy relationships, it is important to note that legal actions in home countries can be powerful. Prompt blacklisting of adversarial groups does inhibit the movement of individuals to proxy wars and should be a sustained policy consideration of the Department of Home Affairs. In this regard, it is relevant to consider that there was a wide network of civilian supporters and individuals able to travel to the Middle Eastern conflict. To be effective, various levels of legal authorities would be required to disrupt both foreign fighter recruitment and facilitation networks.
Authorities to Employ Information Effects
Terrorism is inherently communicative, as many scholars have noted. It is often propaganda by deed. As observed by Mroszczyk and Abrahms in the Handbook of U.S. Counterterrorism and Irregular Warfare Operations, ‘By using violence, terrorists reveal to the target [audience] that they possess the power to cause harm and are highly motivated to change the political status quo’.[248] Amplifying this point, ‘Judith Tinnes finds that the Islamic State conducted 2,281 camera-recorded killings from January 2015 through November 2020’.[249]
While there are readily available metrics regarding the number of bombs that have been dropped on Iraq, statistics regarding the weight of the information contest are publicly opaque.[250] Beyond numeric measures of kinetic military performance, realistic assessments of their effect in eliciting the desired response from the populations of Iraq and Syria are similarly publicly opaque.
Expertise in Irregular, Proxy and Information Effects
This paper highlights the need to improve the ADF’s understanding of irregular organisations. Further, once that understanding is achieved, efforts will be needed to enhance the ADF’s ability to work through proxies. Such improvements will undoubtedly require a nuanced appreciation of information operations that complement operations and that avoid creating countervailing narratives.
Doctrinally, the staff functions for working with militias, information effects and internal analysis of operations, are the ‘5’ (plans) and/or the ‘9’ (civil-military/interagency operations).[251] These numeric designations are based on the general staff system used by most NATO countries, including Australia, to structure their militaries’ staff functions. In this context, a lesson from the Operation Okra intervention is that the Australian Army may need to professionalise the ‘5’ and ‘9’ functions with specific training, education and management, in a manner similar to the ‘4’ (logistics), ‘2’ (intelligence) or ‘6’ (communications) functions. The generation of such expertise has been partially attempted with the periodic conduct of civil-military cooperation courses by the ADF, but does not seem to have been institutionalised in the Australian context.[252] Such expertise might be leveraged to create and maintain effective relationships with irregular actors.
Enduring Versus Episodic Relationships
A cursory analysis of the Syrian irregular organisations indicates that proxy relationships are most effective when established early. Early engagement by a foreign government gave ‘it and its armed group a chance to move faster, be more effective, and, as a result, leave competitors far behind’.[253] This outcome arose due to the importance of organisational leadership (which might be externally provided) in establishing the sustainable structures which an irregular organisation needs to continue its struggle.
As a conflict progresses, new grievances will be created, and polarising radicalisation will spawn extremist ideologies. Extremist groups, by definition, will be less likely to compromise their interests and will therefore be harder for external patrons to influence. The strength of ideological conviction will also mean that moderate groups will face defections, takeovers or destruction from such extremist groups. They must therefore be strengthened early in anticipation of an eventual competition for control over local populations. They must also then be sustained.
The failure of the OIR mission to describe the desired political state to be achieved after the military defeat of ISIS presented as a governance vacuum that was ultimately filled by HTS in December 2024. Creating the conditions for such a development may ultimately prove detrimental to Western interests, similar to the circumstances that have arisen in Iraq since the withdrawal of coalition forces. By comparison, the conduct of proxy warfare by Iran suggests that US policymakers have come to recognise the strategy’s potential in supporting the establishment of strong post-conflict political entities. Other Western militaries can learn from this example.
An inherent tension exists in the pursuit of strategic interests within the context of proxy partnerships. This tension is that of pragmatism versus loyalty. When the patron favours its own strategic interests at the expense of its proxy, episodic proxy relationships predominate as states assess their interests against the broader strategic environment. In short, enduring relationships are more effective than episodic defence engagement.[254] When loyalty and relationships dominate (sometimes due to a clear enduring strategic interest), lasting partnerships are built. The example of the US relationship with the Colombian Armed Forces is often provided in support of the value of enduring relationships, extending back to the Colombian military commitment to the Korean War. Ash Carter likewise argues that enduring engagement with a small residual force in Iraq, instead of a complete withdrawal in 2010, might have led to a different history. He argues that ‘It is possible that we could have averted much of the violence that followed’.[255]
There is a compelling argument for enduring relationships as a lesson from the past 10 years in particular (and past 20 years in general). This realisation carries with it challenges for decision-makers involved in operational force assignment and force generation.
Sources of Leverage and Coordination of Leverage
Australia’s strategic guidance has recognised that Defence preparations today exist in a context of global competition. Some have argued that this environment is that of a new Cold War.[256] If this is so, who was the enemy in 2014? ISIS is one answer; its global narrative attracted approximately 40,000 foreign fighters who subscribed to an anti-Western narrative presenting threats in deep, close and rear battlespaces. Another answer is that the enemy was actually Iran due to its potential to secure a destabilising regional hegemony. A third answer is that the enemy may have been Russia. Here the West’s strategic objective may have been to deny Putin a Middle Eastern basing location within a global balance-of-power calculus sparked by Russia’s seizure of Crimea in 2014, its seven-year proxy war in the Donbass, and its escalation into open conflict in 2022.
The nuanced answer is that perhaps all three responses are equally applicable. If so, the Operation Okra and OIR interventions demonstrate the need to improve the coordination of Western sources of leverage in response to the competing demands posed by geopolitical competition.
Conclusion
The dynamism and complexity of the decade of conflict from 2014 to 2024—termed Operation Okra by the ADF, and OIR by the US—raises questions about the adequacy of Western understanding of irregular warfare and proxy warfare, and challenges efforts to formulate effective strategy in the context of such competition. With a complex litany of actors comes a complex range of drivers and motivations. Such complexity is not going to go away. This paper has illuminated deficiencies in Australian policy and capability pertaining to irregular and proxy warfare to explain the behaviour of participants in contemporary complex environments.
The Islamic State initially thrived in the chaos of the period 2011–2015, and thus attained a quiet milestone in the evolution of war. This milestone was that a non-state actor presented simultaneously as a domestic threat to Australian society, a regional threat (through affiliates in South-East Asia), and a state-like military threat in Iraq and Syria. Understanding how the Islamic State was able to pursue such a sophisticated strategy is essential due to the ongoing threat transnational Salafi-jihadist organisations present to the contemporary rules-based global order. Somewhat unhelpfully, the issue of the Islamic State (and other Salafist-jihadist) recruitment and mobilisation has been presented as solely one of terrorist radicalisation. This over-simplification of the situation falsely escalates the phenomenon terrorism to a strategy that is, in fact, far more complex in nature.
Irregular armed groups, particularly those that have sanctuary and external support, are highly resilient. They fragment and form new alliances, they shift tactics and exploit localised conditions; a kaleidoscope of rapidly changing dynamics that William Harris described as a ‘Quicksilver War’.[257] This dynamism and resilience undermine the Australian Government’s national security objectives, yet we are not helping ourselves with our inadequate understanding of such movements. Indeed, the Islamic State remains, having reverted to a general Maoist latent/incipient phase, with guerrilla warfare characteristics in contested areas (such as Anbar province in western Iraq).[258] That such attacks have generally targeted PMF units or Shi’a militias is unsurprising—the militias are the Iraqi government’s means to contest control of the population and are the source of numerous deprivations. Overall, we can expect the Islamic State strategy of subversion that it enacted in 2012–2014 to be repeated by ‘ISIS 2.0’ as a new generation of frustrated Iraqi Sunnis come of age and question the opportunities their government provides.
As the ADF pivots to an era of major power competition, it is concerning that we do not look more closely to the lessons of the past decade of competition between the US and Russia, Sunni and Shi’a, Qatar and the Gulf States, and Turkey and Russia. These competitions demonstrate that vertical escalation of tensions carries the risk of unpredictable conflict that major and middle powers wish to avoid.
Competition manifests in proxy wars on the peripheries, where patrons support irregular or non-state actors to further their strategic interests. This paper has addressed this gap with an operational analysis of Australia’s Operation Okra commitment, employing a particular focus upon the phenomenon of multi-party competition effected by proxies. It has offered a critical reflection upon planning challenges when engaging an irregular adversary such as the Islamic State, in the context of multi-party competition. With this analysis, this paper proposes several doctrinal models for understanding irregular threats and considering the challenges of proxy warfare, with an intention to advance the preparedness of the ADF to meet such threats now and into the future.
Endnotes
[1] Rojoef Manuel, ‘Australia Ends Middle East Presence Against Islamic State’, The Defence Post, 3 January 2025.
[2] ‘FBI Statement on the Attack in New Orleans’, press release, 1 January 2025.
[3] ‘Operation Augury’, Department of Defence (website), at: https://www.defence.gov.au/defence-activities/operations/global-operations/augury.
[4] Henry Kissinger, ‘Military Policy and Defense of the “Grey Areas”’, Foreign Affairs 33, no. 3 (1955): pp. 419–427.
[5] Quoted in Malcom W Nance, The Terrorists of Iraq: Inside the Strategy and Tactics of the Iraq Insurgency, 2003–2014, Second Edition (Boca Raton, FL: CRC Press, 2015), p. 12.
[6] Raphael Israeli (ed.), PLO in Lebanon: Selected Documents (London: Weidenfeld and Nicolson, 1983).
[7] Ibid., pp. 96–101. The term ‘Special Force’ is distinct from the roles and tasks we associate with Western special forces. The purpose of such Sa’iqa training was essentially the development of terrorist capability.
[8] Syria: Muslim Brotherhood Pressure Intensifies (US Defence Intelligence Agency, 1982), declassified 1 April 2002, p. 3.
[9] Kevin Woods, ‘An Iraqi Military Perspective on the Invasion of 2003’, in Thomas G Manken (ed.), Learning the Lessons of Modern War (Stanford, CA: Stanford University Press, 2020). A minimum of 40,000 is offered by John Robb, Brave New War: The Next Stage of Terrorism and the End of Globalisation (Hoboken, NJ: John Wiley & Sons, 2007), pp. 76–77.
[10] Nance, The Terrorists of Iraq, p. 25; Carter Malkasian, Illusions of Victory: The Anbar Awakening and the Rise of the Islamic State (New York, NY: Oxford University Press, 2017), p. 31.
[11] Robb, Brave New War, p. 44.
[12] Nance, The Terrorists of Iraq, p. 20.
[13] Matthew Levitt, ‘The Role of the Islamic State in the Assad Regime’s Strategy for Regime Survival: How and Why the Assad Regime Supported the Islamic State’, The Washington Institute for Near East Policy (website), 14 July 2021, at: https://www.washingtoninstitute.org/policy-analysis/role-islamic-state-assad-regimes-strategy-survival.
[14] Brian Fishman, ‘The History of the Islamic State: From Abu Musab al-Zarqawi to Abu Bakr al-Baghdadi’, in Michael Sheehan, Erich Marquardt and Liam Collins (eds), Routledge Handbook of U.S. Counterterrorism and Irregular Warfare Operations (London and New York: Taylor & Francis, 2021).
[15] Robb, Brave New War, p. 77.
[16] Nance, The Terrorists of Iraq, p. 174.
[17] Malkasian, Illusions of Victory, p. 31.
[18] Abdel Bari Atwan, Islamic State: The Digital Caliphate (Croydon, UK: Saqi Books, 2015), p. ix.
[19] Australian focus has been upon the problem of Islamic State. However, the phenomenon also importantly includes the diasporic departure of fighters to the South Sudan conflict of 2013–2015. See David Malet’s ‘The Foreign Fighter Project’, David Malet (website), at: https://davidmalet.com/foreign-fighter (accessed 19 October 2021).
[20] Global Terrorism Index 2024 (Sydney: Institute for Economics & Peace, 2024), at: https://www.visionofhumanity.org/terrorism-worsens-as-global-conflict-drives-risk-of-new-wave/.
[21] Ibid., p. 4.
[22] Malkasian, Illusions of Victory; Nance, The Terrorists of Iraq; Michael Weiss and Hassan Hassan, ISIS: Inside the Army of Terror, second edition (New York, NY: Regan Arts, 2016).
[23] US Department of State, ‘Designation of Kata’ib Hizballah as a Foreign Terrorist Organisation’, press release, 2 July 2009, at: https://2009-2017.state.gov/r/pa/prs/ps/2009/july/125582.htm.
[24] Alex P Schmid and Albert J Jongman, Political Terrorism (New Brunswick, NJ: Transaction Publishers, 2008), p. 4, quoting RP Hoffman. Schmid and Jongman offer a more sardonic perspective: that terrorism is ‘violence of which we do not approve’ (p. 3).
[25] Benjamin S Lambeth, Airpower in the War Against ISIS (Annapolis, MD: Naval Institute Press, 2021), argues that this designation of Islamic State as a terrorist or insurgent organisation inhibited the Western response. In Lambeth’s view, the West was slow to target the organisation’s state-like capabilities as a result of this terminology challenge. See also Audrey Kurth Cronin, ‘ISIS Is Not a Terrorist Group: Why Counterterrorism Won’t Stop the Latest Jihadist Threat’, Foreign Affairs 94, no. 2 (2015), at: https://www.foreignaffairs.com/articles/middle-east/2015-02-18/isis-not-terrorist-group.
[26] Liam Collins, ‘Introduction’, in Michael Sheehan, Erich Marquardt and Liam Collins (eds), Routledge Handbook of U.S. Counterterrorism and Irregular Warfare Operations (London and New York: Taylor & Francis, 2021), p. 2.
[27] Rami G Khouri, The Decade of Defiance & Resistance: Reflections on Arab Revolutionary Uprisings and Responses from 2010–2020 (The Soufan Center, 2021).
[28] Irregular warfare was simply defined by the United States military as ‘a violent struggle among state and non-state actors for legitimacy and influence over the relevant populations’. US Special Operations Command and US Marine Corps, Irregular Warfare Joint Operating Concept (Department of Defense, 2007). This definition exhibits significant similarity to David Kilcullen’s discussion of ‘competitive control’, an idea explored later in this paper.
[29] Alexander Vacca and Mark Davidson, ‘The Regularity of Irregular Warfare’, Parameters 41, no. 1 (2011), at: https://press.armywarcollege.edu/parameters/vol41/iss1/15/.
[30] ‘Uppsala Conflict Data Program (UCDP)’, Uppsala Conflict Data Program (website), at: https://ucdp.uu.se/. This dataset is examined in Kendra Dupuy, Scott Gates, Havard Mokleiv Nygard, Ida Rudolfsen, Havard Strand and Henrik Urdal, ‘Trends in Armed Conflict, 1946–2015’, Conflict Trends 8 (2016).
[31] ‘Uppsala Conflict Data Program (UCDP)’, Uppsala Conflict Data Program (website). The chart uses Shawn Davies, Therése Pettersson and Magnus Öberg, ‘Organized Violence 1989–2022, and the Return of Conflicts Between States’, Journal of Peace Research 60, no. 4 (2023).
[32] Exemplar analysis is Vera Mironova, From Freedom Fighters to Jihadists: Human Resources of Non-State Armed Groups (New York, NY: Oxford University Press, 2019); Daniel Byman, Road Warriors: Foreign Fighters in the Armies of Jihad (New York, NY: Oxford University Press, 2019).
[33] I have addressed aspects of this Information Age or Digital Age dilemma in Andrew Maher, Information Age Proxy Warfare (MacDill Airforce Base, Tampa, FL: JSOU Press, 2019).
[34] Based upon ‘The Foreign Fighter Project’, David Malet (website). An alternative source concluded that ‘external states committed troops in support of one or both sides in 40 percent of active civil wars’. Keith Grant and Bernd Kaussler, ‘The Battle of Aleppo: External Patrons and the Victimisation of Civilians in Civil War’, Small Wars and Insurgencies 31, no. 1 (2020): 3.
[35] ‘Global Trends’, Armed Conflict Survey 7, no. 1 (2021): 16.
[36] The US-led coalition operated under Combined Joint Task Force—Operation Inherent Resolve (CJTF-OIR), whose mission was to ‘militarily defeat the Islamic State of Iraq and Syria, or ISIS, in order to enable whole-of-coalition governmental actions to increase regional stability’. ‘Operation Inherent Resolve’, US Central Command (website), at: https://www.centcom.mil/OPERATIONS-AND-EXERCISES/OPERATION-INHERENT-RESOLVE/ (accessed 7 July 2021).
[37] Renee Westra, Syria: Australian Military Operations, Research Paper Series 2017–18 (Parliamentary Library, 2017), p. 3.
[38] Ibid., p. 3.
[39] Andrew Maher, ‘The War in Iraq: Tactical Success, Strategic Ambiguity’, The Strategist, 8 November 2017, at: https://www.aspistrategist.org.au/the-war-in-iraq-tactical-success-strategic-ambiguity/.
[40] Dana JH Pittard and Wes J Bryant, Hunting the Caliphate: America’s War on ISIS and the Dawn of the Strike Cell (New York, NY: Post Hill Press, 2019), p. 95.
[41] Ash Carter, A Lasting Defeat: The Campaign to Destroy ISIS (Harvard Kennedy School Belfer Center, 2017), p. 5.
[42] Christopher Davidson quotes former Secretary of Defense Robert Gates speaking in May 2015 in support of this conclusion: ‘[W]e don’t really have a strategy at all. We’re basically playing this day by day’. Christopher M Davidson, Shadow Wars: The Secret Struggle for the Middle East (London: Oneworld Publications Ltd, 2016), p. 441.
[43] Carter, A Lasting Defeat, p. 26.
[44] The committee likewise questioned the political purpose and whole-of-government integration elements within this testimony. U.S. House of Representatives Committee on Armed Services, ‘U.S. Strategy for Syria and Iraq and Its Implications for the Region’, hearing, 1 December 2015.
[45] Westra, Syria, p. 1.
[46] Ibid., p. 1. Interestingly, the defence minister in 2015 recognised that Daesh (ISIL) posed a security threat to Australia (pp. 4–5).
[47] Department of Defence, ‘Annual Report 2019–2020’, at: https://www.defence.gov.au/annualreports/19-20/DAR_2019-20_Complete.pdf.
[48] Ibid., p. 1. This debate was essential as ‘any strategy to defeat ISIS needed to address the threat in Syria as well’, even though the legal authorities for the mission were framed in terms of Iraq’s defence (p. 3).
[49] Ibid., p. 1.
[50] Ibid., p. 13. The munitions component of this operation is estimated by the cheapest precision-guided munition, at US$18,000, multiplied by the 2,363 munitions reportedly dropped from Australian aircraft to August 2017, at approximately US$42 million. Using similar estimation methods, the cost to June 2018 of munitions expended within OIR is approximately US$1.83 billion.
[51] Allan Behm, Australia’s Interests in the Middle East: A Presence in Search of a Policy (The Australia Institute, 2020).
[52] Pittard and Bryant, Hunting the Caliphate.
[53] Andrew Mumford, The West’s War Against Islamic State: Operation Inherent Resolve in Syria and Iraq (London: IB Tauris, 2021), p. 26.
[54] Dilip Hiro, Cold War in the Islamic World: Saudi Arabia, Iran and the Struggle for Supremacy (London: Hurst & Co., 2018).
[55] Dara Conduit, The Muslim Brotherhood in Syria (Cambridge: Cambridge University Press, 2019).
[56] Ibid., pp. 180–181.
[57] David Phillips, Frontline Syria: From Revolution to Proxy War (New York, NY: IB Tauris, 2021), p. 45.
[58] Behm, Australia’s Interests in the Middle East, p. 5.
[59] Alexandra Stark, ‘The Monarchs’ Pawns? Gulf State Proxy Warfare 2011–Today’, New America, 15 June 2020.
[60] An exception is a statement from then Minister for Defence, Senator the Hon Linda Reynolds, transitioning the operation to enduring Defence cooperation in 2019, ‘Operation Augury-Philippines Transitions to Enhanced Defence Cooperation Program’, media release, 17 November 2019, at: https://www.minister.defence.gov.au/minister/lreynolds/media-releases/operation-augury-philippines-transitions-enhanced-defence.
[61] The Soufan Center, Terrorism and Counterterrorism in Southeast Asia: Emerging Trends and Dynamics (The Soufan Center, 2021), at: https://thesoufancenter.org/research/terrorism-and-counterterrorism-in-southeast-asia-emerging-trends-and-dynamics/.
[62] Data extracted from The Soufan Center, Terrorism and Counterterrorism in Southeast Asia.
[63] Australian Government, Review of Australia’s Counter-Terrorism Machinery (Canberra: Commonwealth of Australia, 2015).
[64] Ibid., p. 17.
[65] Department of Defence, ADDP-D: Foundations of Australian Military Doctrine (Department of Defence, 2012).
[66] As juxtaposed by German historian Delbrück. Gordon A Craig, ‘Delbrück: The Military Historian’, in Peter Paret (ed.), Makers of Modern Strategy: From Machiavelli to the Nuclear Age (Princeton, NJ: Princeton University Press, 1986).
[67] Carter Malkasian, A History of Modern Wars of Attrition (Westport, CT: Praeger, 2002).
[68] Peter Munson, ‘Return to Attrition: Warfare in the Late Nation-State Era’, Strategic Insights 6, no. 6 (2007).
[69] ‘75 percent of farms failed and 86 percent of the livestock died between 2006 and 2011. As a result, up to 1.5 million people migrated from rural areas to towns and cities’. Phillips, Frontline Syria, p. 29. See also Francesca De Châtel, ‘The Role of Drought and Climate Change in the Syrian Uprising: Untangling the Triggers of the Revolution’, Middle Eastern Studies 50, no. 4 (2014); Carole A O’Leary and Nicholas A Heras, Political Strategy in Unconventional Warfare (MacDill Air Force Base, Tampa, FL: Joint Special Operations University Press, 2019), pp. 21–22.
[70] Claudia de Martino, ‘Syria: Civil Society in Times of War’, Reset Dialogues on Civilisations (website), 14 June 2017, at: https://www.resetdoc.org/story/syria-civil-society-in-times-of-war (accessed 26 April 2019).
[71] O’Leary and Heras, Political Strategy, p. 28.
[72] Aisha Ahmad, Jihad & Co.: Black Markets and Islamist Power (Oxford University Press, 2017), p. 6.
[73] Fawaz A Gerges, ISIS: A History (Princeton, NJ: Princeton University Press, 2016), p. 172. These governorates became hotspots in the Syrian Civil War.
[74] Even upon the commencement of the Iraqi conflict, ‘many of the human smugglers al-Qa’ida uses in Syria are freelancers working for money rather than al-Qa’ida’s ideological allies’. Joseph Felter and Brian Fishman, Al-Qa’ida’s Foreign Fighters in Iraq: A First Look at the Sinjar Records (West Point, NY: Combating Terrorism Center Harmony Program, 2008), p. 25.
[75] For example, Nate Rosenblatt and David Kilcullen, ‘How Raqqa Became the Capital of ISIS: A Proxy Warfare Case Study’, New America, 25 July 2019, notes that ‘Abu Luqman, formerly in the business of smuggling jihadists to fight Americans in Iraq, and one of hundreds of suspected jihadists released by the Assad government in 2011 … gave ISIS deep tribal ties in Raqqa’ (p. 25).
[76] Ibid., pp. 167–168.
[77] Thomas Friedman, From Beirut to Jerusalem (New York, NY: Picador, 1989).
[78] Michael WS Ryan, Decoding Al-Qaeda’s Strategy: The Deep Battle Against America (New York: Columbia University Press, 2013) highlights al-Suri’s conclusion that ‘the clandestine, regional organisations like those in Africa, Egypt, Syria, and elsewhere must come to an end. He concluded in 1990–1991 that the time of clandestine groups was over … They were either destroyed by security forces or forced to compromise with a powerful central government, as the Muslim Brotherhood in Egypt had done over time’ (p. 228). Al-Suri’s original analysis can be examined in Lessons from Jihad Waged by Muslim Brotherhood Against Hafiz al-Assad 1976–1982, AFGP-2002-600080 (full translation) (West Point, NY: Combating Terrorism Center Harmony Program), at: https://ctc.westpoint.edu/harmony-program/lessons-learned-from-the-jihad-ordeal-in-syria-original-language-2/.
[79] Felter and Fishman, Al-Qa’ida’s Foreign Fighters in Iraq.
[80] Rosenblatt and Kilcullen, ‘How Raqqa Became the Capital of ISIS’.
[81] Brian H Fishman, The Master Plan: ISIS, Al-Qaeda, and the Jihadi Strategy for Final Victory (New Haven and London: Yale University Press, 2016).
[82] Gerges, ISIS, p. 10.
[83] The terminology of ‘Communist Revolutionary Warfare’ was raised to a doctrinal understanding of the Vietnamese (and the Chinese before them) ‘way of warfare’ during the 1960s by Geoffrey Fairbairn, Revolutionary Warfare and Communist Strategy: The Threat to South-East Asia (London: Faber and Faber, 1968); John J McCuen, The Art of Counter-Revolutionary War: The Strategy of Counter-Insurgency (London: Faber and Faber, 1966); and Robert Thompson, Defeating Communist Insurgency: Experiences from Malaya and Vietnam (London: Chatto and Windus, 1966).
[84] Fishman, The Master Plan.
[85] Ibid., p. 239.
[86] Brynjar Lia and Thomas Hegghammer, ‘Jihadi Strategic Studies: The Alleged Al Qaida Policy Study Preceding the Madrid Bombings’, Studies in Conflict and Terrorism 27, no. 5 (2004).
[87] A hundred years ago, British policy recognised that the reality of jihadist rhetoric, then espoused by Ibn Saud’s Ikhwan, was a ‘political society in the cloak of religion’. Davidson, Shadow Wars, p. 88.
[88] Brian Fishman, ‘The History of the Islamic State’, p. 62.
[89] Atwan, Islamic State, p. 56.
[90] Ibid., p. 56.
[91] Mironova, From Freedom Fighters to Jihadists, p. 57. The analysis found that 78.7 per cent offered this reason, and 44.6 per cent offered this as the primary reason. Supporting the need for further examination of the importance of self-defence, the second reason was ‘to defend my community’ (70.5 per cent). Among Islamist groups, these grievances were more acute: 79.6 per cent sought ‘to take revenge against the Assad regime’, and 90% ‘to defend the community’. Of interest is that 71 per cent wished ‘to build an Islamic state’ and 71 per cent ‘wanted to gain combat training and experience’, suggesting either an expectation of defending the Islamic state or their local community, or returning to home locations to continue armed struggle (p. 60).
[92] Discussed in Gerges, ISIS. Gerges amplifies his argument with an emphasis on the ISIS narrative being centred upon ‘Sunni Islamic’ identity politics (p. 28).
[93] Jacob Shapiro is authoritative on this topic. Jacob N Shapiro, The Terrorist’s Dilemma: Managing Violent Covert Organisations (Princeton and Oxford: Princeton University Press, 2013).
[94] Ibid.; Scott Gates, ‘Recruitment and Allegiance: The Microfoundations of Rebellion’, Journal of Conflict Resolution 46, no. 1 (2002).
[95] Gerges, ISIS, p. 149.
[96] Harmony Documents NMEC-2008-612449 and NMEC-2008-658086 quoted in Brian Fishman, Dysfunction and Decline: Lessons Learned from Inside Al Qa’ida in Iraq (West Point, NY: Combating Terrorism Centre Harmony Project, 2009), pp. 21–25.
[97] The Global Islamic Resistance Call (da’wat al-muqawamah al-islamiyyah al-alamiyyah), 2005, examined by Brynjar Lia, Architect of Global Jihad: The Life of Al-Qaida Strategist Abu Mus'ab al-Suri (London: Hurst, 2007, 2014).
[98] Fishman, Dysfunction and Decline, pp. 21–25; Patrick B Johnston, Jacob N Shapiro, Howard J Shatz, Benjamin Bahney, Danielle F Jung, Patrick K Ryan and Jonathan Wallace, Foundations of the Islamic State: Management, Money, and Terrorism in Iraq, 2005–2010 (Santa Monica, CA: RAND, 2016), p. 2.
[99] Johnston et al., Foundations of the Islamic State, quoting Harmony Documents NMEC-2008-614685 and NMEC-2009-633789, suggest a much lower number: 792 in September 2007 to 357 in January 2009.
[100] Fishman, ‘The History of the Islamic State’, p. 60.
[101] James Verini, They Will Have to Die Now: Mosul and the Fall of the Caliphate (London: Oneworld Publications, 2019), pp. 69–70.
[102] Fishman, The Master Plan, p. 134.
[103] Davidson, Shadow Wars, p. 385.
[104] This language was used by Patrick Cockburn, The Rise of Islamic State: ISIS and the New Sunni Revolution (London: Verso, 2015), p. 16.
[105] Craig Whiteside, Anas Elallame, Moorthy Muthuswamy and Aram Shabanian, The ISIS Files: The Islamic State’s Department of Soldiers (Washington, DC: George Washington University Program on Extremism, 2021).
[106] Johnston et al., Foundations of the Islamic State, p. 7.
[107] Aymenn al-Tamimi, ‘The Evolution in Islamic State Administration: The Documentary Evidence’, Perspectives on Terrorism 9, no. 4 (2015).
[108] Cockburn, The Rise of Islamic State, p. 49.
[109] Mironova, From Freedom Fighters to Jihadists, p. 229. The number of fighters that can be supported is necessarily reduced by other financial demands on the organisation, such as supporting the underground and auxiliary components, and the costs of increasing the fighters’ military capability. However, local fighters can generally rely on familial support networks for food and shelter.
[110] Haroro J Ingram and Devorah Margolin, The ISIS Files: Inside the Islamic State in Mosul: A Snapshot of the Logic and Banality of Evil (Washington, DC: George Washington University Program on Extremism, 2020); Aymenn Jawad al-Tamimi, The ISIS Files: The Islamic State’s Real Estate Department: Documents and Analysis (Washington, DC: George Washington University Program on Extremism, 2020).
[111] Olivier J Walther and Patrick Steen Pedersen, ‘Rebel Fragmentation in Syria’s Civil War’, Small Wars and Insurgencies 31, no. 3 (2020): 455.
[112] This concept is discussed by Anand Gopal and Jeremy Hodge in Social Networks, Class, and the Syrian Proxy War (New America, 2021), p. 13.
[113] Walther and Pedersen, ‘Rebel Fragmentation’.
[114] Fotini Christia, Alliance Formation in Civil Wars (New York, NY: Cambridge University Press, 2012).
[115] Whiteside et al., The ISIS Files.
[116] Factional splits and ideological in-fighting were a significant threat to Islamic State, as discussed by Mironova, From Freedom Fighters to Jihadists. The ISIS media arm was also centralised, likely with consideration to this ideologicial function. Whiteside et al., The ISIS Files.
[117] An interview with a 73-year-old Moslawi quoted in Verini, They Will Have to Die Now.
[118] Mironova, From Freedom Fighters to Jihadists, p. 185.
[119] Haroro J Ingram, Craig Whiteside and Charlie Winter, The ISIS Reader: Milestone Texts of the Islamic State Movement (London: Hurst & Company, 2020).
[120] Hassan Hassan, Out of the Desert: ISIS’s Strategy for a Long War, Policy Paper 2018–8 (Middle East Institute, 2018).
[121] Eli Berman, Joseph H Felter and Jacob N Shapiro, Small Wars, Big Data: The Information Revolution in Modern Conflict (Princeton, NJ: Princeton University Press, 2018).
[122] Daniel Milton, Structure of a State: Captured Documents and the Islamic State’s Organisational Structure (Combating Terrorism Center, United States Military Academy, 2021), p. iv. Milton’s report identifies that in Iraq alone, over 200,000 people were supported by the group’s payroll (including wounded, widows, spouses and children). Referring to irregular warfare theory, this number supports the notion of an underground and auxiliary element much larger than the armed component in the ISIS organisation.
[123] Eric Robinson, Daniel Egel, Patrick Johnston, Sean Mann, Alexander Rothenberg and David Stebbins, When the Islamic State Comes to Town: The Economic Impact of Islamic State Governance in Iraq and Syria (Santa Monica, CA: RAND, 2017), p. xiv.
[124] Alexus G Grynkewich, ‘Welfare as Warfare: How Violent Non-State Groups Use Social Services to Attack the State’, Studies in Conflict & Terrorism 31, no. 4 (2008).
[125] Robinson et al., When the Islamic State Comes to Town, p. xxv.
[126] Ryan, Decoding Al-Qaeda’s Strategy. Nor is an irregular warfare framework limited to al-Qa’eda. Michael WS Ryan, ISIS: The Terrorist Group That Would Be a State (Newport, RI: Center on Irregular Warfare and Armed Groups Case Studies, US Naval War College, 2015), p. 10.
[127] George K Tanham, Communist Revolutionary Warfare: The Vietminh in Indochina (New York: RAND, Praeger, 1961).
[128] Ibid., p. vi.
[129] Ryan, ISIS.
[130] Lessons from Jihad Waged by Muslim Brotherhood Against Hafiz al-Assad 1976–1982, AFGP-2002-600080, at: https://ctc.usma.edu/harmony-program/lessons-learned-from-the-jihad-ordeal-in-syria-original-language-2/.
[131] Ryan, Decoding Al-Qaeda’s Strategy, p. 136.
[132] Ibid., p. 160.
[133] This recognition is made in Verini, They Will Have to Die Now, p. 70.
[134] Guillaume N Beaurpere, ‘ISIS and Protracted War: Why Violent Extremists Persist in the Face of Defeat’, Counter Terrorist Trends and Analyses 6, no. 8 (2014). This form is not illogical—as Thomas Marks argues, ‘it is a technique of purposive (i.e. deliberate) action’. Thomas A Marks, Maoist Insurgency Since Vietnam (London: Frank Cass & Co. Ltd, 1996), pp. 1–2.
[135] Hassan, Out of the Desert; Ryan, ISIS; Rosenblatt and Kilcullen, How Raqqa Became the Capital of ISIS.
[136] Craig Whiteside, ‘The Islamic State and the Return of Revolutionary Warfare’, Small Wars and Insurgencies 27, no. 5 (2016).
[137] Aaron Y Zelin, The Islamic State’s Territorial Methodology, Research Notes 29 (The Washington Institute for Near East Policy, 2016).
[138] Ibid., pp. 1–3.
[139] Islamic State dataset, at: https://www.start.umd.edu/gtd/ (accessed 10 May 2021).
[140] Fishman, ‘The History of the Islamic State’, p. 64.
[141]Cockburn, The Rise of Islamic State, p. 11.
[142] Joby Warrick, Black Flags: The Rise of ISIS (London: Transworld Publishers, 2015), pp. 302–303.
[143] Gerges, ISIS, p. 161.
[144] Davidson, Shadow War, p. 383.
[145] Fishman, ‘The History of the Islamic State’, p. 61.
[146] Benedetta Berti, ‘Contemporary Conflict and Political Violence in the Levant’, in Michael Sheehan, Erich Marquardt and Liam Collins (eds), Routledge Handbook of U.S. Counterterrorism and Irregular Warfare Operations (London and New York: Taylor & Francis, 2021), p. 71.
[147] A similar ‘experimental’ view of strategy is argued by Richard P Rumelt, Good Strategy/Bad Strategy: The Difference and Why It Matters (New York, NY: Currency, 2011), p. 241.
[148] Becca Wasser, Stacie Pettyjohn, Jeffery Martini, Alexandra Evans, Karl Pueller, Nathaniel Edenfield, Gabrielle Tarini, Ryan Haberman and Jalen Zeman, The Air War Against the Islamic State: The Role of Airpower in Operation Inherent Resolve (Santa Monica, CA: RAND, 2021), p. xv.
[149] Lambeth, Airpower in the War Against ISIS; Wasser et al., The Air War Against the Islamic State, p. 84.
[150] Ibid., p. 195; also discussed in detail by Pittard and Bryant, Hunting the Caliphate.
[151] Ibid.
[152] Ibid., p. 254.
[153] An example case is discussed by Pittard and Bryant, Hunting the Caliphate, p. 194.
[154] Wasser et al., The Air War Against the Islamic State, p. 203.
[155] Ibid., p. 209. By the end of the counter-finance campaign, oil revenue had been depleted by 90 per cent. Of note is that Australian F/A-18s participated in strikes against ISIS oil assets (p. 215).
[156] Taxation was purportedly the primary source of ISIS revenue, between $400 million and $800 million in 2015. Ibid., p. 235.
[157] Hesitancy in targeting finance sources is suggested by the recognition that ISIS ‘raised most of its revenues locally’ (as opposed to doing so from external, centrally managed sources) and did so deliberately, noting the lessons Abu Musab al-Suri took from the failed Hama uprising. Patrick B Johnston, Jacob N Shapiro, Howard J Shatz, Benjamin Bahney, Danielle F Jung, Patrick K Ryan and Jonathan Wallace, Foundations of the Islamic State: Management, Money, and Terrorism in Iraq, 2005–2010 (Santa Monica, CA: RAND, 2016), p. 185.
[158] Quoting a letter from a Sunni woman in Mosul in 2014. Cockburn, The Rise of Islamic State, pp. xvii–xviii.
[159] Robert A Pape, Bombing to Win: Air Power and Coercion in War (Ithaca and London: Cornell University Press, 1996).
[160] Ibid., p. 316. Pape is particularly scathing about this theory for the employment of air power. He notes: ‘Reviewing literally thousands of planning documents for the preparation of this book, I found … no document, at any level of government, of more than a page to explain how destroying the target was supposed to activate mechanisms (popular revolt, coup, social disintegration, strategic paralysis, or even thwarting enemy military strategy) which would lead to the desired political change’ (p. 328).
[161] Support for this position is offered by Jason Lyall, Bombing to Lose? Airpower, Civilian Casualties, and the Dynamics of Violence in Counterinsurgency War (Social Science Research Network, 2017), at: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2422170.
[162] Westra, Syria, p. 11.
[163] Wasser et al., The Air War Against the Islamic State, p. 11.
[164] Quoting Stephen Renner, ‘Air Power in the Battle of Mosul’, in P Haun, C Jackson and T Schultz (eds), Air Power in the Age of Primacy: Air Warfare Since the Cold War (Cambridge University Press, 2021).
[165] ‘Operation Inherent Resolve Airpower Summary’, as of 31 August 2017, U.S. Air Forces Central Command Combined Air Operations Center, at: https//www.afcent.af.mil%2FPortals%2F82%2FDocuments%2FAirpower%2520summary%2FAirpower%2520Summary%2520-%2520August%25202017.pdf%3Fver%3D2017-09-07-104037-223&usg=AOvVaw1l4W6IQhpkuIrggpRWezeJ&opi=89978449
[166] Lambeth, Airpower in the War Against ISIS, p. 14.
[167] Ibid., p. 177.
[168] Ibid., p. 248.
[169] Discussed by Malcolm Davis, ‘Spartan Lifter Could Be ADF’s First Gunship’, The Strategist, 26 February 2019. Also discussed in ‘MC-27J Multimission Aircraft’, Airforce Technology (website), at: https://www.airforce-technology.com/projects/mc27j-multimission-aircraft-italy/ (accessed 20 October 2021).
[170] Lambeth, Airpower in the War Against ISIS, p. 73.
[171] Wasser et al., The Air War Against the Islamic State, p. 90.
[172] ‘A positive evolution in air-ground coordination employed in Mosul was the use of the so-called Android Tactical Advise Kit (ATAK). ATAK often took the form of Samsung tablets that were provided to partner forces to relay information to the coalition on potential targets for strikes (e.g. GPS coordinates, imagery), as well as the position of the partner forces to deconflict strikes with friendly forces’. Wasser et al., The Air War Against the Islamic State, p. 178.
[173] A similar conclusion is identified by The United States Strategic Bombing Surveys (Maxwell Air Force Base, AL: Air University Press, 1987).
[174] Michael Trimble, ‘Air Force Strategic Bombing and Its Counterpoints from World War I to Vietnam’, Joint Forces Quarterly 91 (2018).
[175] This incident is discussed by Lambeth, Airpower in the War Against ISIS, pp. 172–173.
[176] These themes are discussed in Ronen Bergman, Rise and Kill First: The Secret History of Israel’s Targeted Assassinations (New York: Penguin Random House, 2018).
[177] The importance of adapting to this type of threat is explored by Richard H Shultz Jr, Transforming US Intelligence for Irregular War: Task Force 714 in Iraq (Washington, DC: Georgetown University Press, 2020).
[178] Daniel Byman, ‘Do Targeted Killings Work?’, Foreign Affairs 85, no. 2 (2006).
[179] Explored by Andreas Krieg and Jean-Marc Rickli, Surrogate Warfare: The Transformation of War in the Twenty-First Century (Washington, DC: Georgetown University Press, 2019); Thomas Waldman, Vicarious Warfare: American Strategy and the Illusion of War on the Cheap (Bristol: Bristol University Press, 2021).
[180] Carter, A Lasting Defeat, p. 16. Speaking about the intelligence picture only several months earlier, Carter surmised that ‘intelligence on ISIS was almost entirely lacking’ (p. 13).
[181] Wasser et al., The Air War Against the Islamic State; U.S. House of Representatives Committee on Armed Services, ‘U.S. Strategy for Syria and Iraq and Its Implications for the Region’, hearing, 1 December 2015.
[182] A similar insurgency strategy to that of Islamic State central was being applied. Indeed, in places it emulated classic ‘oil-spot’ doctrine. Antonio Giustozzi, The Islamic State in Khorasan: Afghanistan, Pakistan and the New Central Asian Jihad (London: Hurst, 2018).
[183] Amira Jadoon and Andrew Mines, Broken, but not Defeated: An Examination of State-Led Operations Against Islamic State Khorasan in Afghanistan and Pakistan (2015–2018) (Combating Terrorism Centre, 2020), p. v.
[184] Giustozzi, The Islamic State in Khorasan.
[185] Ibid., p. vii.
[186] Wesley Morgan, The Hardest Place: The American Military Adrift in Afghanistan’s Pech Valley (New York, NY: Random House, 2021), pp. 484–485.
[187] Gerges, ISIS, pp. 151–153.
[188] Whiteside et al., The ISIS Files, p. 7.
[189] Pape, Bombing to Win, p. 316. Jenna Jordan, ‘When Heads Roll: Assessing the Effectiveness of Leadership Decapitation’, Security Studies 18, no. 4 (2009) also finds that ‘decapitation does not increase the likelihood of organisational collapse beyond [that of] a baseline rate of collapse for groups over time’ (p. 720).
[190] Ronen Bergman, Rise and Kill First.
[191] A similar chain of logic is described in detail by Max Abrahms, Rules for Rebels: The Science of Victory in Militant History (New York, NY: Oxford University Press, 2018).
[192] Discussed by Mironova, From Freedom Fighters to Jihadists.
[193] Abrahms, Rules for Rebels, p. 153.
[194] See Ben Rich, ‘Political Assassinations Were Once Unthinkable. Why the US Killing of Soleimani Sets a Worrying Precedent’, The Conversation, 14 January 2020, at: https://theconversation.com/political-assassinations-were-once-unthinkable-why-the-us-killing-of-soleimani-sets-a-worrying-precedent-129622.
[195] Richard Shultz, Military Innovation in War: It Takes a Learning Organisation. A Case Study of Task Force 714 in Iraq, JSOU Report 16–6 (MacDill Air Force Base, FL: Joint Special Operations University, 2016).
[196] Mark Mazzetti, ‘CIA Study of Covert Aid Fuelled Scepticism About Helping Syria Rebels’, New York Times, 14 October 2014.
[197] Gopal and Hodge, Social Networks, p. 10.
[198] Ugur Ümit Üngör, ‘Shabbiha: Paramilitary Groups, Mass Violence and Social Polarisation in Homs’, Violence 1, no. 1 (2020).
[199] This example quoting Assad Mohsen (born 1984) is a typical response describing an individual’s motivation to join an armed militia. Ibid., p. 69.
[200] For example, this point is made by Gopal and Hodge, Social Networks, p. 5.
[201] This phenomenon is discussed by Gopal and Hodge, Social Networks, p. 6.
[202] Joseph Votel in ‘Irregular Warfare Podcast: How a Group of Women Brought the Fight to the Islamic State’, Modern War Institute (website), 4 June 2021, at: https://mwi.usma.edu/the-daughters-of-kobani-how-a-group-of-women-brought-the-fight-to-the-islamic-state/.
[203] The proxy strategy using Iraqi Kurds in 2002–2003 during the invasion of Iraq is examined by Andrew L, Mick Mulroy and Kenneth Tovo, Irregular Warfare: A Case Study in CIA and US Army Special Forces Operations in Northern Iraq, 2002–03 (Middle East Institute, 2021).
[204] Robert Ford, ‘U.S. Strategy in Syria Has Failed’, Foreign Affairs, 25 January 2021, in which Ford notes the cost of 6 years of support to the Kurds at approximately US$2.6 billion, with a likely long-term dependency due to their location.
[205] U.S. House of Representatives Committee on Armed Services, ‘U.S. Strategy for Syria and Iraq and Its Implications for the Region’, hearing, 1 December 2015, p. 15.
[206] Ibid.
[207] Gopal and Hodge, Social Networks, p. 12.
[208] Phillips, Frontline Syria, p. 45.
[209] Ibid., p. 45.
[210] Gopal and Hodge, Social Networks; Mironova, From Freedom Fighters to Jihadists.
[211] Phillips, Frontline Syria, p. 49.
[212] Carter, A Lasting Defeat, p. 15.
[213] Ibid., p. 14.
[214] Mironova, From Freedom Fighters to Jihadists, p. 279.
[215] Keith Grant and Bernd Kaussler, ‘The Battle of Aleppo’, p. 23.
[216] Steve Coll, Ghost Wars: The Secret History of the CIA, Afghanistan, and Bin Laden, from the Soviet Invasion to September 10, 2001 (New York, NY: Penguin Books, 2005); Steve Coll, Directorate S: The CIA and America’s Secret Wars in Afghanistan and Pakistan (New York, NY: Penguin Press, 2018).
[217] Carlotta Gall, ‘Saudis Bankroll Taliban, Even as King Officially Supports Afghan Government’, New York Times, 6 December 2016.
[218] Mazzetti, ‘CIA Study of Covert Aid Fuelled Scepticism about Helping Syria Rebels’. This study importantly noted that ‘negligible impact’ was made when ‘unaccompanied by a direct U.S. supporting intervention’. This point seemingly supports findings regarding the importance of coercive support, informed by close understanding of client actions, as discussed by Walter C Ladwig III, The Forgotten Front: Patron-Client Relationships in Counterinsurgency (Cambridge: Cambridge University Press, 2017).
[219] Jan Gleiman, ‘Unconventional Warfare and Strategic Optionality’, The Strategist, 1 October 2014, at http://www.aspistrategist.org.au/unconventional-warfare-and-strategic-optionality/.
[220] Alex Vatanka, ‘The Modern History of Iran and the Birth of the Shia Proxy Model’, in Michael Sheehan, Erich Marquardt and Liam Collins (eds), Routledge Handbook of U.S. Counterterrorism and Irregular Warfare Operations (London and New York: Taylor & Francis, 2021), p. 153
[221] ‘The fundamental issue was that Iranian-backed militias, the so-called PMF, provided the bulk of the manpower for the operation. Early signs from villages “liberated” on Tikrit’s outskirts revealed these militias’ excesses, including looting and revenge killings.’ Wasser et al., The Air War Against the Islamic State, p. 152.
[222] Ibid., p. 153.
[223] An exemplar report discussing this phenomenon in today’s urbanised environments is International Committee of the Red Cross, ‘I Saw My City Die’: Voices from the Front Lines of Urban Conflict in Iraq, Syria and Yemen (Geneva: International Committee of the Red Cross, 2017), at: https://www.icrc.org/en/publication/i-saw-my-city-die-voices-front-lines-urban-conflict-iraq-syria-and-yemen.
[224] David Galula, Counterinsurgency Warfare: Theory and Practice (Westport, CT: Praeger Security International, 1964, 2006).
[225] Christia, Alliance Formation in Civil Wars.
[226] Walther and Pedersen, ‘Rebel Fragmentation’, pp. 445–446.
[227] Ibid., pp. 447.
[228] This mobilising activity is discussed in detail by Lucian W Pye, Guerrilla Communism in Malaya: Its Social and Political Meaning (Princeton, NJ: Princeton University Press, 1956).
[229] Alan Ogden, Through Hitler’s Back Door: SOE Operations in Hungary, Slovakia, Romania and Bulgaria 1939–1945 (Barnsley, UK: Pen & Sword Military, 2010), p. 146. Raids had been conducted against the strategic Ploiesti oilfields in Romania from 11 June 1942.
[230] Ibid., p. 146.
[231] Ibid., p. 255.
[232] The civil journalism group Raqqa is Being Slaughtered Silently is an exemplar of this phenomenon. See also Mike Stevens, ‘Resistance and Information Warfare in Mosul and Raqqa’, The RUSI Journal 165, no. 5 (2020), at: https://rusi.org/publication/rusi-journal/resistance-and-information-warfare-mosul-and-raqqa-darkness-light; and Isak Svensson, Jonathan Hall, Dino Krause and Eric Skoog, ‘How Ordinary Iraqis Resisted the Islamic State’, The Washington Post, 22 March 2019, at: https://www.washingtonpost.com/politics/2019/03/22/civil-resistance-against-islamic-state-was-much-more-common-than-many-think/.
[233] Svensson et al., ‘How Ordinary Iraqis Resisted the Islamic State’.
[234] Pittard and Bryant, Hunting the Caliphate.
[235] Andrew Milburn and Kyle Atwell, ‘American Decline: Losing the Campaign for Influence’, Modern War Institute (website), 18 June 2021, at: https://mwi.usma.edu/american-decline-losing-the-campaign-for-influence/.
[236] William Knarr, The 2005 Iraqi Sunni Awakening: The Role of the Desert Protectors Program, JSOU Report 15–4 (MacDill Air Force Base, FL: JSOU Press, 2015).
[237] Stephen Biddle, Jeffrey A Friedman and Jacob N Shapiro, ‘Testing the Surge: Why Did Violence Decline in Iraq in 2007?’, International Security 37, no. 1 (2012): 10.
[238] Wasser et al., The Air War Against the Islamic State, p. 199.
[239] General (Ret.) Joesph Votel notes that ‘combating terrorism is a form of strategic competition. Being good at this, demonstrating our value to partners in this particular area, building relationships around this is really important’. Paul Cruickshank, Don Rassler and Kristina Hummel, ‘Twenty Years After 9/11: Reflections from General (Ret) Joseph Votel, Former Commander of U.S. Central Command’, CTC Sentinel 14, no. 7 (2021).
[240] Russian objectives within this intervention were argued to be ‘keep Assad in power, secure its Mediterranean port at Tartus, refine its military capabilities, and demonstrate its weaponry for the global arms market’. Carter, A Lasting Defeat, p. 36.
[241] Lambeth, Airpower Against ISIS, p. 246.
[242] Chris McInnes, ‘We Have People, We Have Machines. What’s Missing?’, Australian Defence Business Review,(3 August 2021).
[243] See ‘Assistant Secretary of Defense for Special Operations and Low-Intensity Conflict’, Office of the Under Secretary of Defense for Policy (website), at: https://policy.defense.gov/Offices/ASW-for-Special-Operations-Low-Intensity-Conflict/.
[244] See ‘Foreign Terrorist Organizations’, U.S. Department of State (website), at: https://www.state.gov/foreign-terrorist-organizations/.
[245] Alfred H Paddock, US Army Special Warfare: Its Origins (Washington, DC: National Defense University Press, 1982).
[246] These themes are explored in Andrew Maher, An Australian Doctrinal Concept for Special Warfare: Lessons and Considerations (Directorate of Future Land Warfare, Australian Army, 2016), at: https://researchcentre.army.gov.au/library/occasional-papers/australian-doctrinal-concept-special-warfare-lessons-and-considerations.
[247] The requirement for Australian specialisation in this type of warfare was explored in greater detail in Andrew Maher, ‘Strategic Planners: A Response to Operational Complexity’, Australian Army Journal 13, no. 1 (2016).
[248] Joseph Mroszczyk and Max Abrahms, ‘Countering Extremist Organisations in the Information Domain’, in Michael Sheehan, Erich Marquardt and Liam Collins (eds), Routledge Handbook of U.S. Counterterrorism and Irregular Warfare Operations (London and New York: Taylor & Francis, 2021), p. 425.
[249] Ibid., p. 425.
[250] Based upon the readily available information at Operation Inherent Resolve: Combined Joint Task Force (website), at: https://www.inherentresolve.mil/.
[251] ‘Joint Publication (JP) 3-33 Joint Task Force Headquarters’, U.S. Joint Chiefs of Staff (website), 31 January 2018, at: https://www.jcs.mil/Doctrine/.
[252] In contrast, the US has long held specialisation through its special forces capability (which rotationally undertakes postings in conventional formations), psychological operations, civil affairs, and the US Army’s new Security Force Assistance Brigades.
[253] Mironova, From Freedom Fighters to Jihadists, p. 274.
[254] Episodic relationships may emerge deliberately or accidently (due to shifting political priorities). The case for deliberate control over relationships to be coercive in nature is made convincingly by Ladwig, The Forgotten Front; and Eli Berman and David Lake (eds), Proxy Wars: Suppressing Violence Through Local Agents (Ithica, NY: Cornell University Press, 2019). The benefit of coercive control is lost, however, when a lack of focus allows a client to manipulate those who believe themselves to be patrons. This risk is likewise examined by Ladwig, Berman and Lake.
[255] Carter, ‘A Lasting Defeat’, p. 3.
[256] For example, Hal Brands and John Lewis Gaddis, ‘The New Cold War,’ Foreign Affairs, 19 October 2021.
[257] William Harris, Quicksilver War: Syria, Iraq and the Spiral of Conflict (New York, NY: Oxford University Press, 2018).
[258] Michael Knights and Alex Almeida, ‘Remaining and Expanding: The Recovery of Islamic State Operations in Iraq in 2019–2020’, CTC Sentinel 13, no. 5 (2020).