Abstract
The announcement of a new ‘Information Warfare Division’1 within the Australian Defence Force acknowledges the need for cyber-enabled warfare strategies to address the challenges of the information age.
Implementing such force modernisation demonstrates a positive, albeit belated, approach to address the disruptive nature information technology is having on the character of modern warfare. This announcement presents an opportunity for Australia’s Special Operations Command (SOCOMD) to maintain its position as the Government’s military-strategic vanguard by developing a cyber-enabled ‘Special Information Warfare’ concept. This concept will call for bottom-up action that senior Government and Defence decision makers can support through policy and doctrinal debate.
The paper frames the future operating environment and hypothesises a technologically-enabled Special Operations Task Group (SOTG) deployed against a hybrid threat, demonstrating the utility in developing a unified strategy of ‘Special Information Warfare’. Outlining Australia’s current state
of play will highlight the current gaps in policy and doctrine, demonstrating the need for a novel, asymmetric strategy. Analysis of Russia’s New Generation Warfare, Chinese Distributed Warfare and Integrated Network Electronic Warfare, and the Islamic State’s use of mass media will illuminate why Australia needs to adapt rapidly towards a strategy that can achieve ‘information dominance’ in future conflict. US cyber-enabled warfare strategies and doctrine provide an excellent point of reference to further support a unique Australian SOCOMD strategy. By benchmarking against Russia, China and the US, the political and military pressure for change can be realised, instigating debate and action aimed at implementing an innovative solution to maintain military relevance in the information age.2 Cyber-enabled ‘Special Information Warfare’ seeks to weaponise information, operationalise cyberspace effects and normalise an offensive adoption of Information Warfare within SOCOMD that spans the strategic to tactical level.
Characterising Future War & the Need for a Cyber-Enabled Asymmetric Approach
‘The evolving character of conflict that we currently face is best characterized by convergence.3 This includes the convergence of the physical and psychological, the kinetic and non-kinetic, and combatants and non-combatants.’
- Frank Hoffman 4
The character of war is developing towards an increasingly lethal battlefield fought amongst population centres in both a contested and congested environment.5 The proliferation of connected devices is expected to reach fifty billion by 2020, highlighting cyberspace as a critical operational medium.6 An increased level of parity is emerging where military- technological advantage previously enjoyed by Western forces may not be so decisive in future conflict.7 Russia, China and the Islamic State have identified the importance of ‘information’ for strategic success and continue to pursue strategies to affect success in cyberspace—a realisation that has yet to reach full maturity within the Australian context. Future conflict will consist of contested norms and persistent disorder, permeating through physical and virtual realms, necessitating an approach that combines the full suite of cyberspace capabilities with traditional physical military actions.8 These elements are explored in the following vignette.
Set no more than ten years into the future, a SOTG has been deployed at short notice against a hybrid threat consisting of military-strategic conventional forces and a surrogate proxy. The operating environment is dense and distinguishing threat actors amongst the civilian population is near impossible. This is a multi-vector, multi-front and multi-theatre battlespace where effects are generated in milliseconds across the physical, informational and human domains.9 The Commander is determined to provide niche Special Operations (SO) effects, as requested by Government, which encompass indirect10 and direct11 effects. Special Forces (SF) teams project into the operating environment, employing cyber-enabled strategies in an environment where military communications have been denied.12
Cyber-enabled SF relay voice and data in real-time across mobile, ad-hoc and wireless mesh networks that have been encrypted.13 The multi-protocol mesh networks enable communications with a surrogate partner force and will be solar powered, enabling the facilitation of lethal effects through joint enablers.14 Manoeuvring through hyper-connected dense urban populations, the SF teams employ rolling cyber-enabled ‘Movement to Contact’ tactics, like rolling penetration tests to probe local networks, and exploitation of ‘Internet of Things’ devices.15 Another technically savvy SF team infiltrates an enemy’s rear administrative area, utilising close-access waveforms, delivering a payload to spread malware throughout the adversary’s air defence systems. Disruption of the enemy’s cognitive capacity occurs in real-time as a neighbouring SF team initiates a critical influence campaign, utilising strategic reach-back capabilities to deliver cyberspace effects aimed at degenerating trust in the adversary’s C2 and logistics nodes through cyberspace. Combat advisors working with cyber-enabled partner forces utilise cyberspace tools to generate disproportionate ‘human domain’ effects, influencing a large proxy force and shaping support among the civilian populace. Meanwhile, specialists within the Operations Centre are monitoring opportunities to deliver effects in, through and external to cyberspace to disable the adversary’s ability to provide effective command and control. The combination of effects required a unified strategy that adopted an ‘information dominance’ approach. This strategy was ‘Special Information Warfare’.
Defining the Problem – Australia’s ‘State of Play’ in the Information Age
Australia’s establishment of an ‘Information Warfare Division’ within the Australia Defence Force (ADF) demonstrates serious consideration of cyber-enabled warfare and acknowledgement of the challenges imposed by the information age as it relates to modern warfare. The announcement indicates a workforce that will grow from 100 to 900 personnel, presenting an opportunity to spark action and debate about force design, structure, training and doctrine.16 This is a chance for the ADF to define its strategic identity regarding a cyber-enabled warfare strategy, one that can incorporate the full spectrum of information-centric capabilities across all warfighting domains. The gaps in the latest Defence White Paper’s strategic direction regarding cyber-enabled capabilities, dated Information Operations and Network-Centric Warfare doctrine, assessed task-saturation for the Australian Signals Directorate (ASD) in meeting Australia’s cyberspace capability needs, and recent announcements from the Senior Leadership Group within the ADF all merge to suggest the need for a bottom-up plan of action for an asymmetric strategy to fight future, information-centric conflict where strategic risk is at its greatest. By unpacking the current state of play in the Australian context, it will highlight how pursuing an SO concept can contribute to the ADF’s effort to maintain relevance in the information age.
The Australian Prime Minister’s announcement that an offensive cyber capability exists within the Australian Signals Directorate indicates a growing capability to produce effects in and through cyberspace.17 Liam Nevill argues that this announcement also imbues a responsibility for Defence to formulate its thinking on how such a capability will be used and how it can be employed in support of military operations.18 This carries a degree of risk whereby the whole-of-government responsibilities entrusted in ASD may lead to task-saturation and an inability to employ cyberspace effects effectively in support of full-spectrum military operations during future conflict. Ormrod and Turnbull’s Military Cyber Maturity Model (MCMM) highlights a capability progression and field of employment model for ASD into the future, indicating the potential for task-saturation in support of future military operations.
The announcement of an ‘Information Warfare Division’ lead by Major General Marcus Thompson could not have come at a more critical time in the ADF’s force modernisation and will warrant innovative solutions in adopting asymmetric advantage with a relatively modest defence force.20 Since 2003, Australia’s military capability development has been geared towards the concept of Network Centric Warfare (NCW).21 This approach is likely to be surpassed as Australian senior leadership seeks to align modern strategy against the newly-defined US Multi-Domain Battle (MDB) concept.
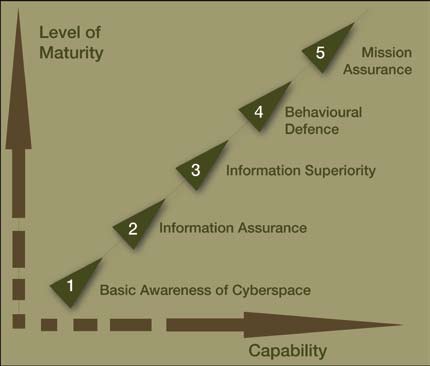
Figure 1. ASD Military Cyber Maturity Model (variation by Major Conway Bown). See the Endnotes for the various stages of the model. 19
Senior military figures within the ADF have commented on the challenges posed by the information age and the need to include cyber-enabled effects, yet have been unable to clearly define a unified strategy. Brigadier David Wainwright, Director General Land Warfare, during a panel discussion at the Williams Foundation seminar on integrated force design, commented:
…future land forces will face unprecedented levels of complexity in cluttered, congested, hyper-connected and lethal future operating environments… where the additional layers of informational and human complexity further complicate traditional geo-physical challenges.22
A slide from the presentation captures the key challenges presented to the land force, which provides a foundation for discussion on the need for a novel Australian SO concept. ‘Information Activities’ is the traditional Australian doctrinal approach to operations in the Information Environment (IE),24 documented in ADDP 3-13 Information Activities, 2013. It does not include cyberspace effects in great detail, as should be expected given the highly compartmented and relatively under-developed cyberspace capabilities within the ADF, particularly in comparison to the US, Russia and China. This doctrine presents an opportunity for concept development given the recent announcement for organisational change within the ADF towards a cyber-enabled warfare capability. It also serves as a reminder that Australia currently sits well below the base-line in comparison to the expanse of open-source US doctrine and strategy documents, highlighting the need for more open engagement and discussion to harness lessons learned by our principal partners.

Figure 2. A slide from Brigadier Wainwright’s presentation at the Williams Foundation seminar 2017 (Image recreated by Major Conway Bown) 23
Australia’s reaction to the challenges imposed by technological proliferation in the information age can be summarised as slow at best. A number of challenges face the ADF as it attempts to identify a pathway to success for a new ‘Information Warfare’ workforce. It has become apparent through open debate by ADF’s senior leadership that cyber- enabled, information- centric strategies that achieve supremacy across the physical, informational and human dimensions will be critical to future military advantage. As the Australian Army’s former Commander-Forces Command, Major General Gus Gilmore commented at an address to the Royal United Services Institute:
‘Cyber opportunities and risks must be an ongoing discussion. We have only scraped the surface of what this disruptive technology offers to us, and what combat vulnerabilities it exposes. The value and availability of information is changing, and through the modernisation process we must ensure that we are structured to maximise the benefits and mitigate the risks of the cyber and digital revolution.’ 25
Additionally, as former Chief of Army, Lieutenant General Angus Campbell stated in his address at the Lowy Institute:
‘…the Australian Army is aware of the need for a change in approach. The Defence White Paper sets us a challenge well beyond the continental force of today. Some things we can see now. The linear progression of typical military practice is an uncertain path; our security interests in the 21st Century Indo- Pacific will require ‘multiple domain’ thought and action. We also know that we cannot rely on technology alone. Technology works best when enabling or partnering human endeavour.’ 26
Statements from ADF’s senior leaders highlight an appetite for ground-up action within Defence, invoking greater debate around a strategy capable of spearheading a complementary asymmetric approach in support of the newly established ‘Information Warfare Division’. Such a strategy is suggested for the Australian SO community, which can serve as a test- bed for a concept of ‘Special Information Warfare’, where the importance and centrality of the IE in executing technologically-enabled direct and indirect special operations in support of a Joint Force Commander can be realised. Such a concept acknowledges that future warfare will remain a human endeavour and as such requires an approach where cyber-enabled effects in the IE are nested with operations in the physical dimension. As Australia is in its preliminary phase of capability development, several lessons can be gleaned by understanding adversary and potential adversary capabilities being employed and developed by Russia, China and the Islamic State, among others.
The Rise of the Hybrid Threat and Information- Centric Challenges
Russian and Chinese military doctrine continues to evolve with a clear appreciation of ‘information dominance’ as key for modern military success. Russian synchronised political, diplomatic, military kinetic, cyberspace, SO, surrogates and mass information operations characterise a contemporary hybrid threat worth studying and presents an indication of how Australia may have to fight in future conflicts.27 The Ukraine conflict demonstrates a contemporary example where Russia employed an asymmetric strategy that successfully synergised cyberspace effects with traditional physical actions.28 A battle in cyberspace raged on, with secure communications being hacked, telecommunication lines severed, Distributed Denial of Service (DDoS) attacks targeting government websites, offensive cyberspace effects penetrating financial and military institutions contributing to large-scale civil unrest.29 The strategy of New Generation Warfare, or ‘hybrid warfare’ as it is defined by the West, was adapted by General Valery Gerasimov, the Russian Chief of General Staff, and employs ‘indirect action, informational campaign, private military organisations, SO Forces, and internal protest, backed by the sophisticated conventional and nuclear military capabilities’.30 This strategy combines a 1980s reconnaissance- strike approach aimed at disrupting Command, Control, Communications, Computers, Intelligence, Surveillance, and Reconnaissance (C4ISR [or C4ISTAR when Target Acquisition is added to the capability]) systems with non-kinetic Electronic Warfare and maskirovka - Russian military deception doctrine which focuses on denial, deception, disinformation, propaganda, camouflage and concealment.31 Figure 3 represents the synergy between technological and psychological effects which underpins the New Generation Warfare approach.
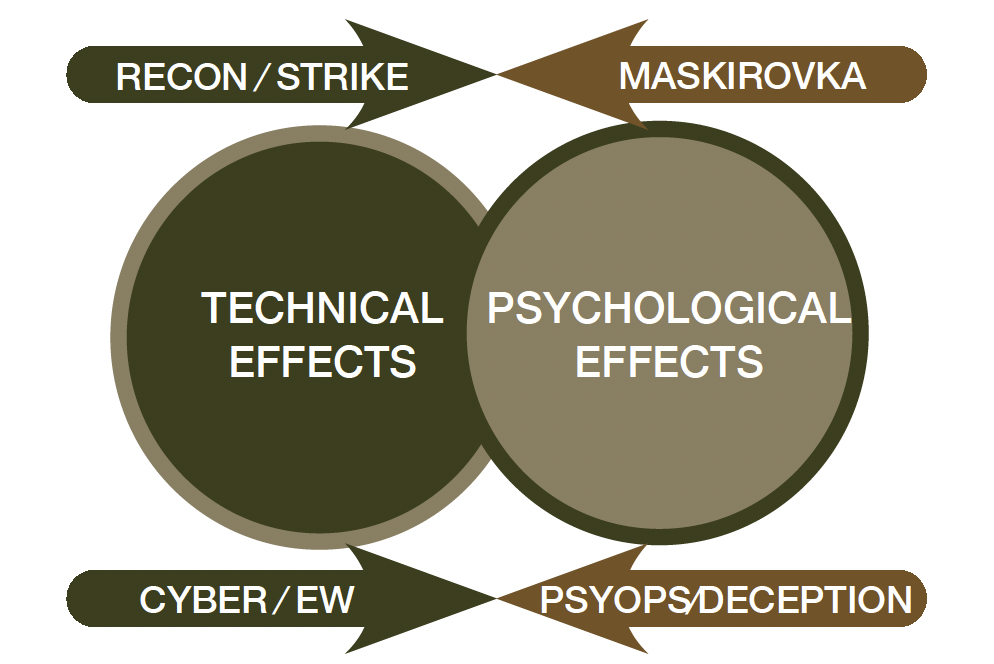
Figure 3. Russian ‘New Generation Warfare’ Strategy (Image derivative by Major Conway Bown)
Advancements in Chinese ‘distributed warfare’ acknowledge the benefit of cyber-enabled strategies at lower level formations, widely dispersed to achieve strategic effects in distant theatres.32 This strategy should resonate with any modern military, whereby the application of cyberspace effects in support of disaggregated land forces, aimed at achieving superiority in the IE, give cause for new thinking. China has also nested cyberspace and electromagnetic spectrum capabilities at the strategic level, under the concept of Integrated Network Electronic Warfare (INEW) and aimed at disrupting an adversary’s ability to process and use information.33 While the Chinese People’s Liberation Army (PLA) has moved slowly to adapt to the opportunities presented during the information age, it has studied the US war machine and is developing inter-service capabilities that encompass advanced command and control systems and technologically advanced C4ISTAR capabilities able to ‘fight and win localised wars under informatised conditions’.34 The Chinese approach to cyberspace operations, and information warfare more broadly, is likely to reach maturity within the next ten years. While this may seem like a distant future, it presents a case-study of high importance for any middle power where flashpoint conflicts involving cyberspace, human and physical domain battle may eventuate at short notice.
State-based capability development is also coupled with the Islamic State’s employment of cyberspace, particularly social media platforms, to spread violent extremist propaganda. The ability to shape and influence a global audience, mobilise willing Islamic fundamentalists across international borders, facilitate lethal aid and exercise command and control by issuing orders through cyberspace presents an international problem that spans the political, strategic, operational and tactical levels of conflict. A key lesson is the use of mass media and social media platforms to influence a global audience towards a common cause, demonstrating superiority in the ‘contest of wills’. Former Prime Minister Malcolm Turnbull commented in an address in Washington DC that the Coalition was losing the battle of the narrative in cyberspace.35 This statement alone indicates the need for novel, asymmetric strategies that employ cyberspace capabilities nested with standing military options to shape and influence through cyberspace against potential state and non- state adversaries.
The future operating environment will include a hybrid threat landscape in which the physical and virtual environments will converge. Among others, Russia, China and the Islamic State offer timely lessons from which Australia can learn in the development of organic information-centric strategies. The lessons combine to form a foundation of understanding, which is further reinforced by acknowledging the pace-setting contribution of the United States.
A Comprehensive Approach – The US and Multi Domain Battle, Cyberspace Superiority and Special Operations
Throughout the history of warfare, militaries have sought advantage through actions intended to affect the perception and behaviour of adversaries. Information is such a powerful tool, it is recognized as an element of U.S. national power – and as such, the Department must be prepared to synchronize information programs, plans, messages, and products as part of a whole-of-government effort.
- Former US Secretary of Defense, Ash Carter 36
A combination of open-source US strategic direction and doctrinal documents provides a sound foundation that supports the development of an Australian concept of ‘Special Information Warfare’. The US has realised that technological parity in the information age is increasing, leading to the introduction of the Third Offset Strategy. Multi Domain Battle has emerged in response to the Third Offset Strategy, addressing a cross-domain, holistic approach to fight and win future conflict against a peer adversary. US Special Operations Command’s (USSOCOMD) involvement includes an increase in Special Warfare, operating in the Grey Zone short of traditional armed conflict. The conventional and SO strategies are both underpinned with an increased integration of cyberspace effect operations.
The MDB concept defines an approach for combat operations targeted against a peer adversary in the 2025-2040 timeframe.37 The MDB concept acknowledges the overlapping and interconnected nature of the land, sea, air and space domains with the human and cyber domains.
This operational approach acknowledges the centrality and importance of achieving ‘information dominance’ both in and through cyberspace. The characterisation of a future involving contested norms and persistent disorder places significant emphasis on cyberspace, the IE more broadly, and the cognitive components of warfare.38
In understanding the MDB concept, future strategic direction can be understood as it applies to the ADF. Lieutenant General Angus Campbell recently addressed the Lowy Institute, presenting a clear indication that future Australian joint operations in the littoral would resemble the characteristics of US MDB:
Innovation in today’s non-geographically bound domains – air, space and cyber – is driving connectivity and complexity across the Indo-Pacific region. It’s bringing the region closer and more tightly networked. And I think it means the idea of ‘an army for a multiple-domain strategy’ rather than only for a ‘maritime strategy’ might be a more useful holistic concept… We need to generate, coordinate and anticipate multiple cross-domain actions and reactions… Perhaps future conflict in the Indo-Pacific will require greater thought about the development and use of indirect approaches. Our security interests in the 21st Century Indo-Pacific will require ‘multiple domain’ thought and action. We also know that we cannot rely on technology alone. Technology works best when enabling or partnering human endeavour. 39
The last two decades have instigated transformation within the US Army in its application of Information Operations doctrine, simply because the nature of information and its availability has evolved so rapidly.40 The US Department of Defense (DoD) defines Information Operations as the ‘integrated employment, during military operations, of Information-Related Capabilities (IRCs)41 in concert with other lines of operations to influence, disrupt, corrupt, or usurp the decision-making of adversaries and potential adversaries while protecting our own’.42 Highlighting cyberspace operations as a sub-component within information operations further exemplifies the importance of an over-arching ‘Information Warfare’ concept that unifies the effects generated in and through cyberspace.
A newly released publication is the US Army’s FM 3-12 Cyberspace and Electronic Warfare Operations 2017. It states that the US Army conducts cyberspace and EW operations in the IE, which includes the physical, informational and cognitive dimensions.43 FM 3-12 highlights the relationship cyberspace has with the IE by describing the cyberspace layers, which includes the physical network layer, logical network layer and cyber- persona layer.44 This relationship proves important when understanding the connection between cyberspace and the human domain, and between physical and virtual effects which continue to converge. Figure 4 highlights the level of connectedness a soldier has on today’s modern battlefield through the cyber-persona layer, which in turn provides an opportunity to provide effects in and through cyberspace in support of a higher ‘information dominance’ strategy.The US DoD Strategic Cyberspace Operations Guide 2016 stresses how complementary cyberspace operations enhance physical domain effects as well as supporting other IRCs.46 This publication highlights the relationship of cyberspace operations when supporting information operations, which focuses on the denial or manipulation of enemy and potential adversary decision making.47 Further detail highlights effects which may include targeting an information medium (such as a wireless access point in the physical domain), the message itself or a cyber- persona (an online identity co-ordinating C2 decision making and the dissemination of propaganda).48
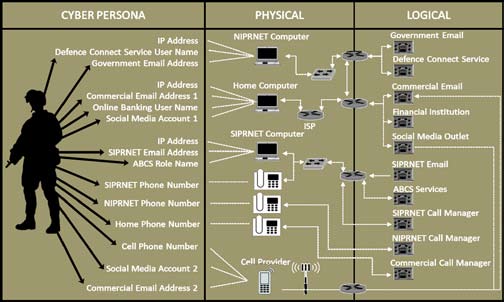
Figure 4. Layers of Cyberspace in the US context 45
Another powerful capability is the strategic reach-back support offered by organisations such as United States Cyber Command (USCYBERCOM) and its sister organisation, the National Security Agency (NSA), which can be compared to the Australian Signals Directorate. The recent release of USCYBERCOM’s ‘Beyond the Build’ envisions a Joint Force of 2020 where Cyberspace Operations are fully integrated and are a natural precursor for any future land, maritime, air and space-based operations.49 US Army Cyber Command’s (ARCYBER) Land Cyber White Paper 2018 - 2030 presents a foundational argument where innovative integration of land and cyberspace operations at all levels of conflict is a necessity for future success in war.
The convergence of land and cyberspace operations continues to inform a model applicable in the Australian context, where a complex operating environment requires increased interdependence, disaggregation and an ability to operate over strategic distance in disrupted and denied environments.50
The establishment of US ARCYBER in 2010 has provided a significant amount of time to develop cyberspace operations in support of joint land forces. Australia can benefit from a slow start and the application of lessons learned can be applied modestly in support of a holistic strategy with ‘information dominance’ at its core. US cyberspace operations highlight effects in, through and external to cyberspace that can be synchronised to achieve desired operational objectives against an adversary’s decision- making process. These actions ‘in’ cyberspace can be used to disrupt an adversary’s information, information systems or networks.51 Operations ‘through’ cyberspace can include standard joint functions to maintain operational functionality such as command and control, intelligence, fires, manoeuvre and sustainment functions.52 Figure 5 illustrates how effects can be generated in, through and external to cyberspace.
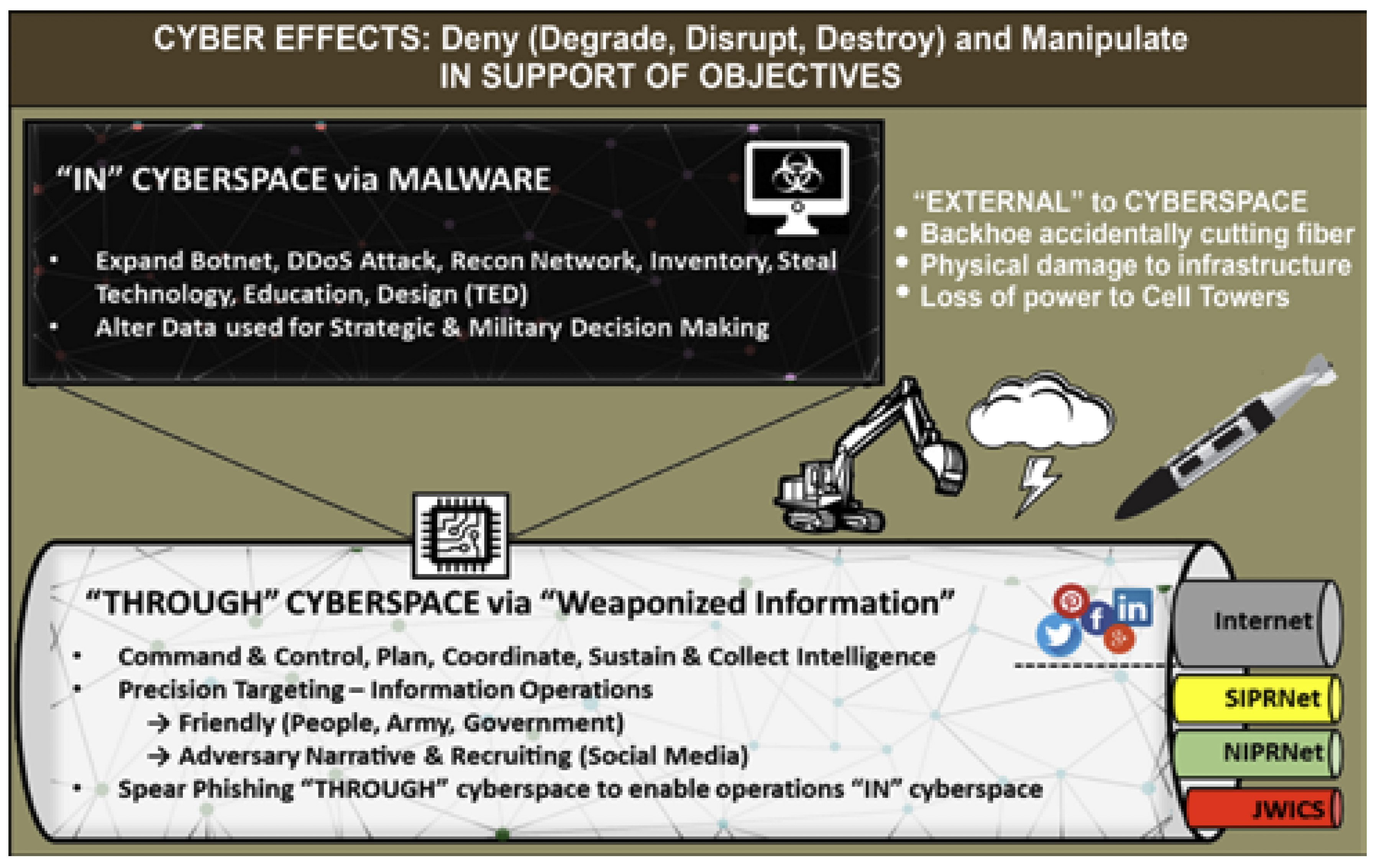
Figure 5. Example of Cyber Effects in the US context 54
The deeper dimension of US cyber-warfare that extends beyond information operations or cyber-effect operations can be seen in the expansive amount of information-centric doctrine, publications and public debate which places a premium on prompt ‘information dominance’.53 Cyberspace operations continue to serve as a subordinate component to a broader Information Warfare strategy, yet are fundamental when considering a unique ‘Special Information Warfare’ concept. A truly powerful combination is Cyberspace Operations, as part of a broader Information Warfare strategy, mixed with the potent direct and indirect capabilities of Special Operations Forces.
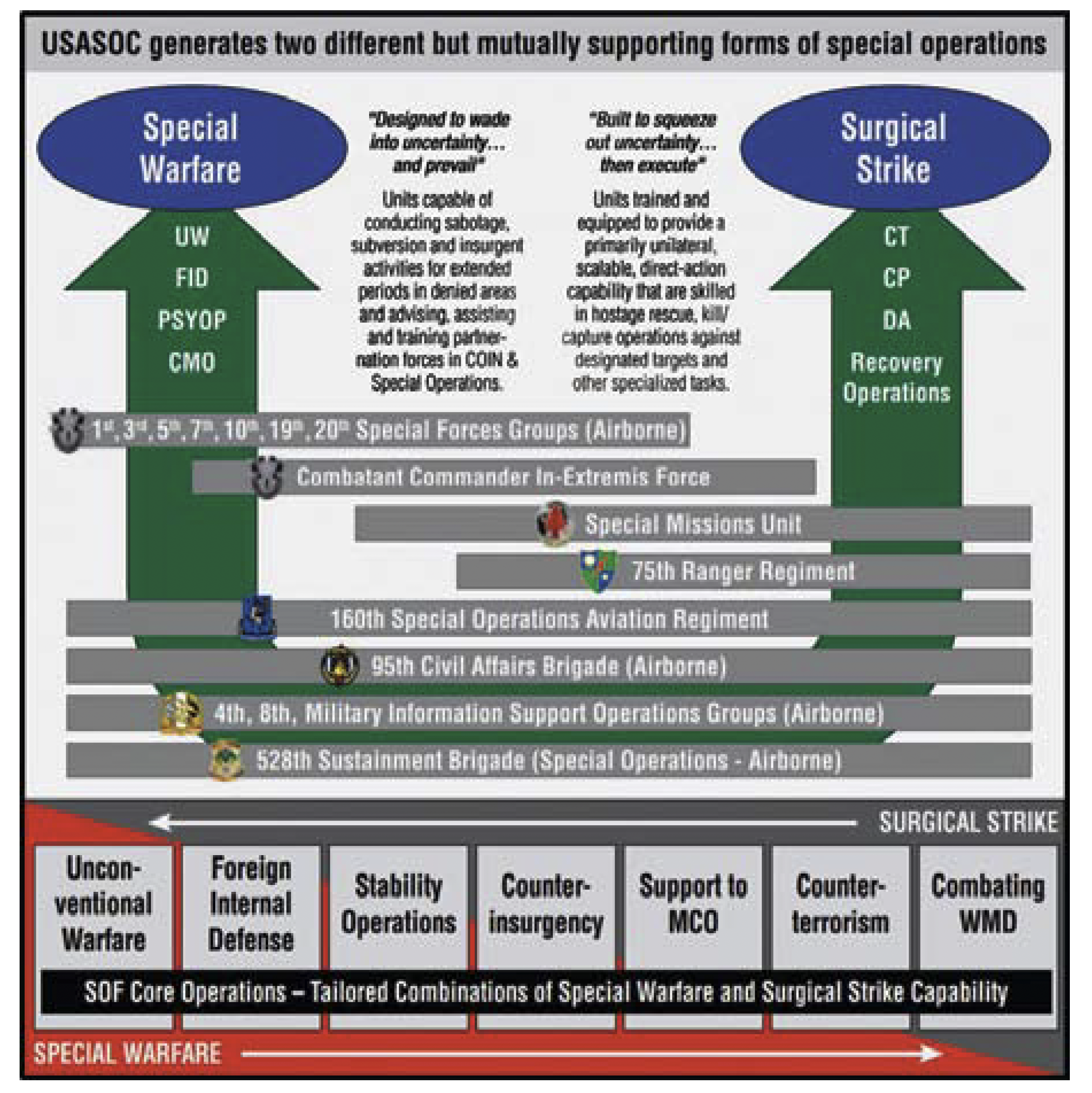
Figure 6. USASOC mission sets 58
A history of cyberspace effects in support of US special operations can be traced back to 2007, where a Computer Network Operations Squadron was raised to support SF operators during the Iraq War.55 United States Army Special Operations Command (USASOC) Army Special Operations Forces (ARSOF) 2022 White Paper provides a key point of reference to support the development of a ‘Special Information Warfare’ concept that suites the modest size of Australia’s Army and especially Australia’s SO community. USASOC’s delineation between Special Warfare56 and Surgical Strike57 presents an opportunity to develop a synchronised ‘Special Information Warfare’ concept that bridges the gap between the two mission sets. The figure above provides an insight into USASOC’s two forms of special operations and their mutually supporting relationship.
ARSOF 2022 stresses the importance of identifying innovative ways to execute Find, Fix, Finish, Exploit, Analyse and Disseminate (F3EAD) targeting operations59 as part of its surgical strike capability, as well as building and fostering relationships in the human domain as part of its Special Warfare capability. ARSOF 2022 highlights how both concepts require a mastery of the cyber domain for future success, where Army SF personnel will be trained in cyber operations and have an ability to utilise cyberspace to enable operations.60 ARSOF 2022 covers potential solutions which include the formalisation of cyberspace synchronisation, manning, training and capability development across USASOC. Lastly, not only are offensive and defensive cyberspace capabilities included, but the increasing emergence of smart phones, mobile devices and social media and the capabilities they provide to influence campaigns.61
Given Australia’s comparatively small SO community, a concept of ‘Special Information Warfare’ that can blend cyberspace operations with human domain operations is worth investigating. This would enable Australian SOCOMD to spearhead an ‘information-centric’ warfighting strategy that takes advantage of the lessons learned from the US example, the opportunities presented by the information age and better align to the trends of future warfare.
‘Special Information Warfare’ – A Cyber-Enabled Special Operations Strategy for the Australian Defence Force
Machines don’t fight wars. Terrain doesn’t fight wars. Humans fight wars. You must get into the mind of humans. That’s where the battles are won.
- Colonel John Boyd 62
The Australian Government depends on the SO community to provide SO effects through direct and indirect means in politically and strategically sensitive operating environments.63 An example of the direct approach includes the Direct Action (DA) missions conducted by Australia’s SOTG to target insurgent leaders in Afghanistan.64 The indirect approach includes Australia’s strong history in training indigenous partner forces, most recently demonstrated in a SOTG’s ‘advise and assist’ mission to support the Iraqi Counter Terrorism Service during the battle to retake Mosul from Islamic State militants.65 Australia’s SO community provides an important military option for Government, which includes options that cannot be undertaken by conventional forces, such as inserting at strategic distances behind enemy lines or in a theatre where there are no lines at all.66
Traditional SO mission sets will not be exempt from the evolving nature of modern warfare caused by the information age. Contemporary applications of the direct and indirect approach require adoption of ‘best practice’ methods aimed at maintaining a capability-edge over adversaries that are actively seeking to modernise using emerging disruptive technologies.67 The announcement of an Australian ‘Information Warfare Division’ presents an opportunity to instigate debate amongst policy-makers and the senior Defence leadership as well as action through bottom-up development of capability that acknowledges the centrality of ‘information dominance’. The concept of cyber-enabled ‘Special Information Warfare’ is a potential solution. Colonel Boyd’s quote is a timely reminder that the human factor will continue to underpin actions in, through or external to cyberspace and should be considered when addressing a holistic strategy geared towards ‘information dominance’. War will continue to be fought for the people and amongst the people in a contest of wills.
The vision for ‘Special Information Warfare’ is to develop technologically- enabled, human terrain-oriented SOF tethered to strategic enablers that are capable of projecting power and influence in, through or external to cyberspace to target the cognitive decision-making of an enemy, potential adversary or designated stakeholder. Figure 7 highlights a conceptual vision, effects and desired end-state.
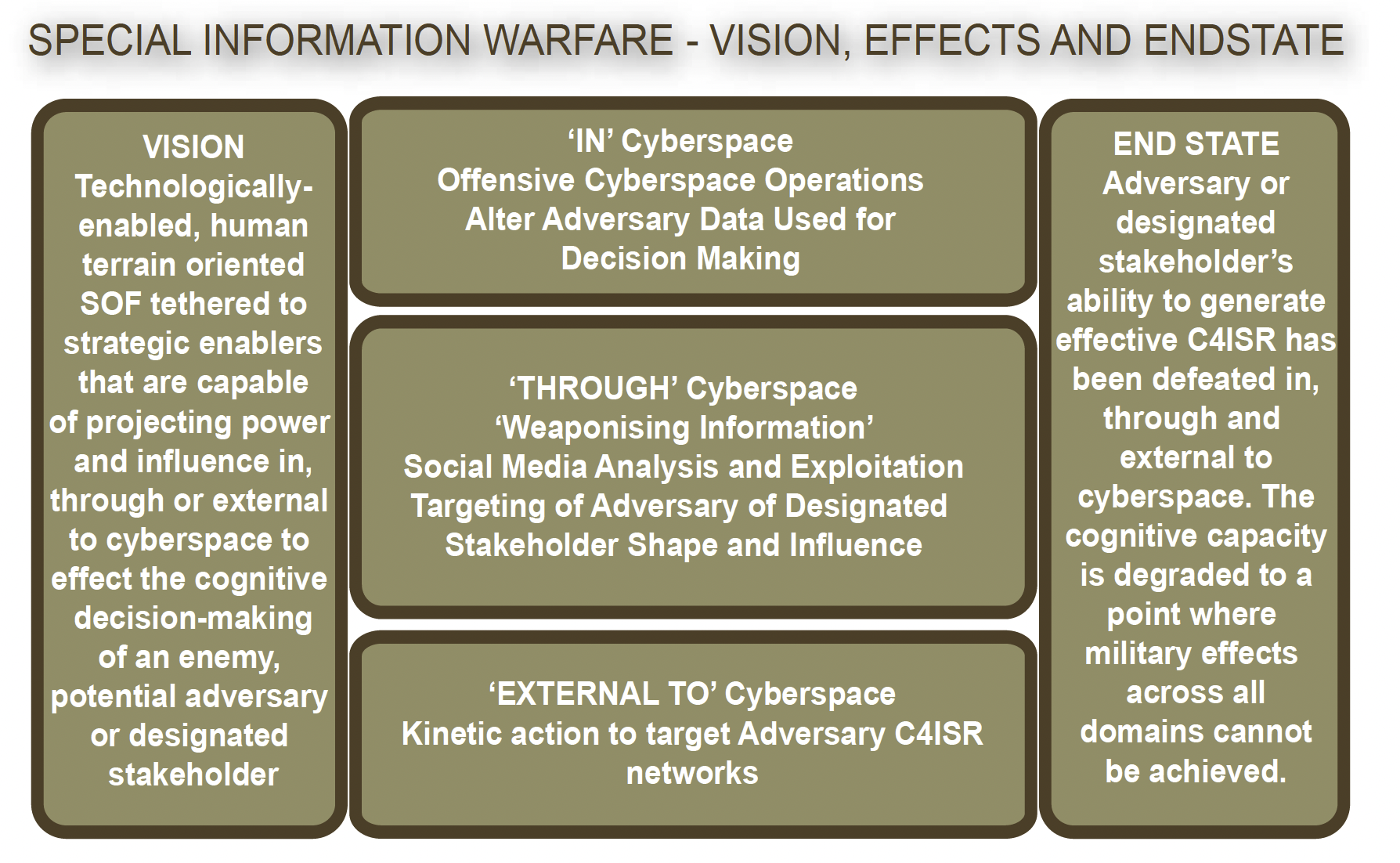
Figure 7. Special Information Warfare Vision, Effects and End-State
At a fundamental level, the concept of ‘Special Information Warfare’ can be defined as a blend between special warfare and surgical strike,harnessing the capabilities of cyberspace operations with traditional notions of information operations, with a unique relationship to the human domain. The term has been chosen specifically to break the model of traditional ‘information activities or operations’ and reinforce the necessity to evolve a cyber-enabled SO concept as an offensive form of warfare that accentuates the importance of ‘information dominance’. Australian SOF represents a suitable force element for such a capability that employs small-scale, disaggregated forces over strategic distance empowered with cyber- enabled tools in contested and congested operating environments.
The USASOC ARSOF 2022 mission sets diagram provides a foundation to nest the ‘Special Information Warfare’ concept as a third SO mission set. The adapted diagram below aims to spark further debate on how policy- makers and senior leadership can harness an asymmetric strategy that compliments current Australian SO mission sets.
For any new capability to succeed, it needs two things. The first is a name and the second is a home. This could take the form of a ‘Special Information Warfare Branch’ which could reside within the newly established ‘Information Warfare Division’ to support raise, train, sustain and capability development functions. Brigadier Jason Blain, Director- General Force Options and Plans, Force Design Division, recently presented the various capability programs within Defence at the Williams Foundation seminar on integrated force design. The presentation highlighted six capability streams across the core warfighting functions, presenting an opportunity to nest ‘Special Information Warfare’ under the Intelligence, Surveillance, Reconnaissance and Electronic Warfare (ISREW), space and cyber capability stream within Joint Integration. The responsibility would reside within Vice Chief of the Defence Force Group (VCDF Group) and seek to provide the link between the ‘Warfighting Innovation’ and ‘Asymmetric Response’ capability programs.69 This suggestion is coupled with an acknowledgement that the concept of ‘Special Information Warfare’ would require further ground-up action within SOCOMD’s tactical units.
To provide further detail to spark debate and inform action, the ‘Special Information Warfare’ force design would include a tailored and tethered workforce, where operational effects are provided from the strategic to tactical level. The broader cyberspace workforce debate is a largely unanswered question and the suggested ‘Special Information Warfare’ force design is aimed to complement broader workforce modernisation within the ADF. Figure 9 provides a prospective force design model as to what could constitute a ‘Special Information Warfare’ capability.
The Special Information Warfare Force Design includes the development of a Tactical Special Information Warfare Operator (SIWO). A Tactical SIWO is a Special Forces soldier who has received cyberspace awareness, influence and information operations training and is able to effectively utilise cyberspace tools to influence in, through and external to cyberspace. The cyberspace awareness training would focus on the physical layer of cyberspace, facilitating a tethered approach where proximity and access to prospective targets in denied areas can be brought into effect through coordinated reach-back. Additional training in the cyber-persona layer to shape and influence partner forces, surrogates and the populace would also occur.
A Technical SIWO is a Signals Corps soldier, who has received advanced technical training in the application of offensive cyberspace tools to provide support at the tactical level. The relationship between the Tactical SIWO and Technical SIWO is complementary as the Special Forces soldier would bridge the human domain whilst the Signals Operator would specialise in technical skills.
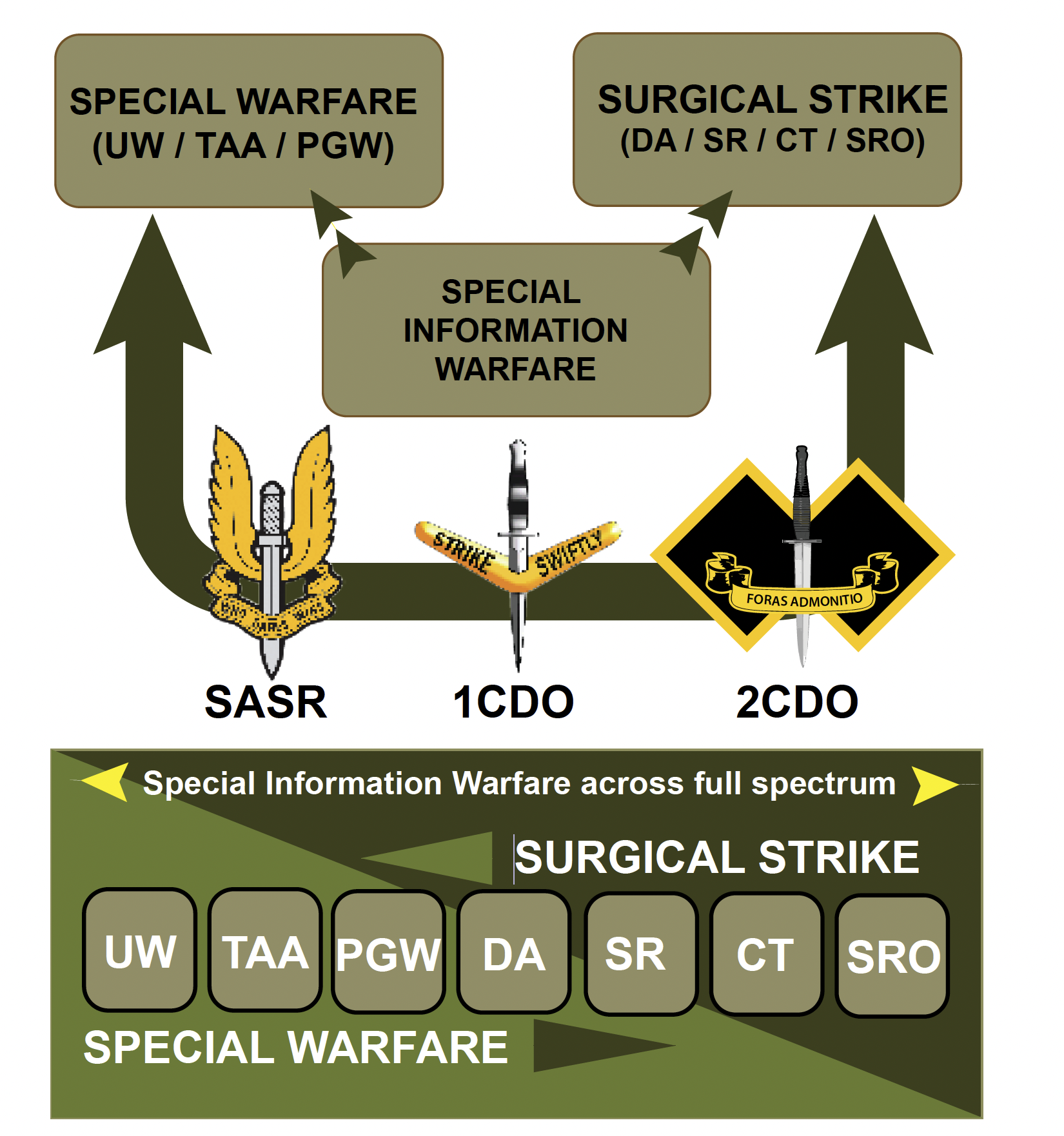
Figure 8. Special Information Warfare Force Design showing the seven core SF functions within surgical strke and special warfare domains. (This diagram has been derived from the author’s by Major Conway Bown)
A SIWO planner is an officer, warrant officer or senior non-commissioned officer (SNCO) position consisting of Intelligence, Signals or Arms Corps. The SIWO planners will have received an information operations and cyberspace operations-centric curriculum coupled with influence and critical thinking training. The SIWO planner position is nested at the tactical, operational and strategic operations centres where detailed planning occurs and would require a headquarters staff designation.
The strategic reach-back includes a formalised relationship with the ASD and the broader Australian intelligence community. Additionally, the raising of a Military-Civilian Cyber Corps is included, which is suggested for broader discussion as an enabler to support the full suite of military cyberspace operations. The unique nature of this strategy is the generation of SO effects (both direct and indirect) in, through and external to cyberspace under a unified theory aimed at achieving ‘information dominance’.
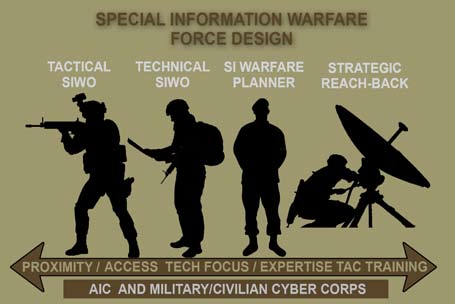
Figure 9. Special Information Warfare Force Design (This image has been derived from the author’s and has been created by Major Conway Bown)
An operational design focused on SO effects utilising the indirect approach has been recommended to further instigate debate which focuses on influencing an adversary, population and partner or surrogate force aimed at achieving cyber-enabled relative superiority.70 SOF are well suited to wage influence campaigns given their niche cultural skills and access to surrogate or partner ‘special’ forces during a conflict.71 Enablement with cyber-tools to maximise influence through social media will only enable greater influence and access. Figure 10 provides a point of reference for the concept of ‘Special Information Warfare’ utilising the indirect approach during Phase Zero operations.
As the adversary is weakened, and the partner force demonstrates increasing capability, the point of cyber-enabled relative superiority is achieved and a transition occurs to focus military effort on rebuilding the confidence and capability of the indigenous partner force, maintaining positive support from the population and degrading the remaining adversarial threat.
While future cyber-warfare and the contest for ‘information dominance’ may require more keyboard warriors, small-scale SOF operating at strategic distances in congested and contested environments will be necessary for future success. Enabling such forces with an ability to operate with a technological advantage in, through and external to cyberspace, as well as the ability to interface with strategic cyber-warfare capabilities, will provide battlespace situational understanding and effects that cannot be achieved by any other force.
Conclusion
The creation of an ‘Information Warfare Division’ within the ADF highlights an evolving understanding of the importance for cyber-enabled warfare strategies. While Australia has much ground to cover in comparison to pacesetting countries like the US, Russia and China, it demonstrates much needed progression. Australia’s modest defence force warrants niche, novel and asymmetric solutions to meet the demands of the information age and calls for modernisation within its ranks. A concept of cyber-enabled ‘Special Information Warfare’ seeks to spark action and debate amongst policy makers and senior Defence leadership, presenting a technologically and socially aware SO option to address future conflict where strategic risk is at its peak. A congested, contested future operating environment riddled with persistent disorder, amongst hybrid adversary threats that have adopted information-centric strategies and hyper-connected population centres necessitates a commensurate asymmetric approach. Through indirect and direct special operations enabled with technological means at strategic distance, tethered to strategic joint enablers and capabilities, Australian SOCOMD can contribute to Australia’s Information Warfare capability, maintaining relevance in an era where technological parity continues to rise.
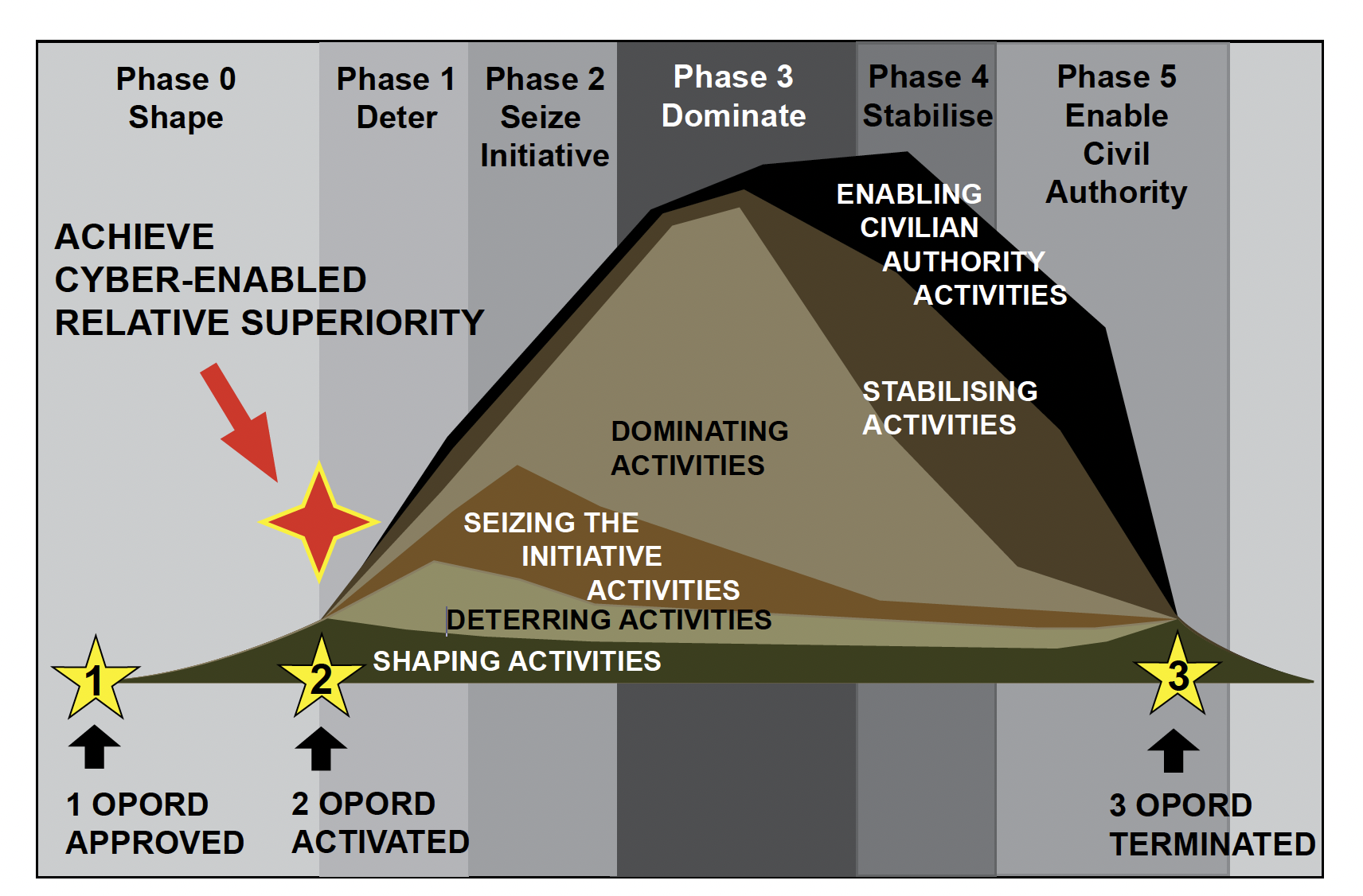
Figure 10. Special Information Warfare – Achieving cyber-enabled relative superiority. (This image is derived from the author’s and was created by Major Conway Bown)
Endnotes
- The ABC’s Ashlynne McGhee released an exclusive report highlighting ‘a major transformation’ within the Australian Military with the announcement of a new Information Warfare unit to be established within the ADF. A McGhee, 2017, ‘Cyber Warfare Unit Set to be Launched by Australian Defence Forces’, at: http://www.abc. net.au/news/2017-06-30/cyber-warfare-unit-to-be-launched-by-australian-defence- forces/8665230. accessed 1 Jul, 2017.
- G Austin, 2016, ‘Middle Powers and Cyber-Enabled Warfare: The Imperative of Collective Security’, at: http://www.unsw.adfa.edu.au/australian-centre-for-cyber- security/sites/accs/files/uploads/DISCUSSION%20PAPER%20Middle%20Powers% 20REARMED%2027%20Jan%202016.pdf, accessed 12 Jun, 2017
- ‘Convergence’ relating to cyberspace is further explained in the US Army TRADOC Cyber ‘Army 2050, Report 2016’, “The consequent attribute of the cyber future will be convergence… between land and cyberspace operations. … between all the legacy domains, as cyberspace constitutes the connective ether that readily transfers effects from one domain to another … between time and space as enhanced information and communication technologies decrease the time and expand the reach of cyber actions… between electromagnetic (EMS) and cyberspace action … between defensive and offensive cyberspace operations to ensure one function informs the other … between information management (IM) and knowledge management (KM) as largedata is leveraged to achieve advantage … between Army operational and institutional activities, creating an unprecedented level of interaction where operations impact institutional activities and vice-versa.” US Army TRADOC, 2016, The 2050 Cyber Army, at: https://www.google.com.au/url?sa=t&rct=j&q=&esrc=s&source=web&cd= 3&cad=rja &uact=8&ved=0ahUKEwiitOqQpqHUAhXHjZQKHWUXAzYQFgguMAI&url=https%3 A%2F%2Fcommunity.apan.org%2Fcfs-file%2F key%2Ftelligent-evolution- components-attachments%2F01-9016-00-00-00-13-82-05, accessed 18 Jun, 2017, pp 45-46
- F Hoffman, 2009, ‘Hybrid Warfare and Challenges’, at: http://smallwarsjournal.com/ documents/jfqhoffman.pdf, accessed 17 Jun, 2017, p 34
- M Pomerleau, 2017, ‘The Relationship Between Third Offset Strategy and Multi- Domain Battle’, at: http://www.c4isrnet.com/articles/the-relationship-between-third- offset-strategy-and-multi-domain-battle, accessed 10 Jun, 2017
- R Brown, 2017, ‘The Indo-Asia Pacific and the Multi-Domain Battle Concept’, at: https://www.army.mil/article/184551/the_indo_asia_pacific_and_the_multi… battle_concept, accessed 9 Jun, 2017
- J McGrath, 2016, ‘21st Century Information Warfare and the Third Offset Strategy’, at: http://ndupress.ndu.edu/Portals/68/Documents/jfq/jfq-82/jfq-82_16- 23_McGrath.pdf. Accessed Jun 12, 2017, p 17
- US Army TRADOC, 2016, p 4
- G Austin, 2016, Shaping the Cyber Arms Race of the Future, at: https://www.unsw. adfa.edu.au/australian-centre-for-cyber- security/sites/accs/files/uploads/Shaping%20 Cyber%20Arms%20Race%20of%20th e%20Future.pdf, accessed 10 Jun, 2017
- The indirect approach is defined as Special Warfare in the US context, referring to the “execution of activities that involve a combination of lethal and nonlethal actions taken by a specially trained and educated force that has a deep understanding of cultures and foreign language, proficiency in small-unit tactics, and the ability to build and fight alongside indigenous combat formations in a permissive, uncertain, or hostile environment”. Proxy Guerrilla Warfare, Special Support Operations (Train/Advise/ Assist and Advance Force Operations including Information Operations), and Support Operations constitute the indirect approach in the Australian context. A Davies, 2014, A Versatile Force: The Future of Australia’s SO Capability, at: https://www.aspi.org.au/ publications/a-versatile-force-the-future-of- australias-special-operations-capability/ Special_operations_capability.pdf, accessed 16 Jun, 2017, pp 10-11
- The direct approach is defined as surgical strike in the US context, referring to the “execution of activities in a precise manner that employ special operations in hostile, denied or politically sensitive environments to seize, destroy, capture, exploit, recover or damage designated targets, or influence adversaries or threats”. Special reconnaissance, precision strike/direct action and special recovery operations constitute direct actions in the Australian context. A Davies, 2014, pp 9-10
- P Duggan, 2016, ‘To Operationalise Cyber, Humanize the Design’, at: http:// smallwarsjournal.com/jrnl/art/to-operationalize-cyber-humanize-the-design, accessed 9 Jun, 2017, p 2
- Duggan, 2016, p 2
- Duggan, 2016, p 2
- Duggan, 2016, p 2
- McGhee, 2017
- L Nevill, 2016, ‘Thinking Deeper About Australia’s Offensive Cyber Capability’, at: https://www.aspistrategist.org.au/thinking-deeper-about-australias-offe…- capability/, accessed 14 Jun, 2017
- Nevill, 2016
-
D Ormrod and B Turnbull, 2015, ‘Toward a Military Cyber Maturity Model’, at: https:// www.unsw.adfa.edu.au/australian-centre-for-cyber- security/sites/accs/files/uploads/ Military%20Cyber%20Maturity%20Model%20v1.pdf, accessed 10 Jun, 2017.
Due to space limitations in the text, the individual constructs of each step in the Military Cyber Maturity Model could not be included. They are provided here instead.Basic Awareness of Cyberspace: •ASD Top 4, •A focus on providing services to users, security as a cost of business •Patching through physical action, •Basic training in cyber-security for all personnel.
Information Assurance: •ASD Top 35, •Ability to detect system attacks, •Automated patching, •Cyber-systems census included in battle preparations at the unit level, including social media profiles, individual wearables, mobile phones and IoT-enabled devices, •Security audits conducted on high value supply chains and software code,
•Training for all personnel.
Information Superiority: •Cyber red teaming by dedicated assets and regular attack exercises, •Ability to dynamically manage the network under attack, •Independent security audits of the supply chain, software code and active networks, •Training for all personnel in cyber-security using simulation and active learning, •CERT and forensic capabilities at the Brigade level, •Cyber integrated ino combined arms teams
Behavioural Defence: •Utilising honey nets and honey pots and information deception to defend networks in conjunction with active and passive toolsets,
•Dedicated assets tasked with providing false networks, reports, electronic emissions and data down to company/squadron level, •Integration of cyber and physical deception plans with kinetic action, •The ability to revert to alternative services and maintain a basic level of operational capability when systems are compromised.
Mission Assurance: •Cultural transition from the information assurance/superiority paradigm to mission assurance, •Degeneracy provides the ability to respond to shock and catastrophic system attacks, •All personnel trained to ‘work around’ digital systems as a part of normal business, •Deception plans and counterintelligence measures are carefully integrated with the false movement of troops and the employment of networks that transmit false data, •Training on information security parallels training on deception, • Training and regular exercises in ‘actions on’.
- McGhee, 2017
- A Davies and M Davis, 2016, ‘ADF Capability Snapshot 2016’, at: https://www.aspi. org.au/publications/adf-capability-snapshot-2016-c4isrwinning-in- the-networked- battlespace/SI107_ADF_capability_snapshot_2016_C4ISR.pdf, accessed 6 Jun, 2017, p 3
- R Laird, 2017, ‘Designing the Integrated Force’, at: http://www.sldinfo.com/designing- the-integrated-force-the-australian-defense-force- repositions-for-the-next-phase-of- 21st-century-force-structure-development/, accessed 16 Jun, 2017
- Laird, 2017
- US Army Publication FM 3-12 defines the Information Environment as the aggregate of individuals, organizations, and systems that collect, process, disseminate, or act on information which is drawn from the US Joint publication, JP 3-13
- G Gilmore, 2016, ‘Raising and Training the Australian Army’, at http://www.rusinsw. org.au/Papers/20160628.pdf, accessed 2 Jun, 2017, p 12
- A Campbell, 2016, ‘Address to the Lowy Institute’, at: https://www.army.gov.au/ sites/g/files/net1846/f/speeches/20161004_ca_address_lo wy_institute_4_oct_16_ edited_1500_4_oct.pdf, accessed 7 Jun, 2017
- USASOC, 2017, USASOC White Paper, at: http://www.soc.mil/USASOCTalks/ Expandingmaneuver21Century.html, accessed 16 Jun, 2017, p 2
- M Nordmoe, 2015, ‘The Ghost in the Machine: Defining SOF in Cyberspace’, at https://_Operations_Forces_in_Cyberspace, accessed 10 Jun, 2017, p 69
- Nordmoe, 2015, p 70
- D Adamsky, 2015, ‘Cross-Domain Coercion: The Current Russian Art and Strategy’, Institut Francais des Relations Internationales, at: http://www.ifri.org/sites/default/files/ atoms/files/pp54adamsky.pdf, accessed 27 Apr 2017, pp 22-23
- Adamsky, 2015, pp 27-28
- Austin, 2016, p 7
- E Lasiello, 2015, ‘Are Cyber Weapons Effective Military Tools?’, at: http://www.inss.org.il/he/wp-content/uploads/sites/2/systemfiles/2_Iasi…, accessed 9 Jun, 2017, p 25
- G Austin, 2016, Australia Rearmed! Future Needs for Cyber-Enabled Warfare, ACCS Discussion Paper No 1, at: https://www.unsw.adfa.edu.au/unsw-canberra- cyber/sites/ accs/files/uploads/DISCUSSION%20PAPER%20AUSTRALIA%20REAR MED.pdf, p 10
- M Turnbull, 2016, Australia and the United States: New Responsibilities for an Enduring Partnership, at: https://www.pm.gov.au/media/2016-01-18/australia-and- united- states-new-responsibilities-enduring-partnership, accessed 18 Jun, 2017
- US DoD, 2016, Strategic Cyberspace Operations Guide, at: https://publicintelligence. net/usarmy-strategic-cyber-ops/, accessed 1 Jun, 2017
- US Army TRADOC, 2016, p 1
- US Army TRADOC, 2016, p 4
- Campbell, 2016
- US Army, 2016, FM 3-13 Information Operations, at: http://www.apd.army.mil/epubs/ DR_pubs/DR_a/pdf/web/FM%203- 13%20FINAL%20WEB.pdf, accessed 14 Jun, 2017, p vi
- An IRC is a tool, technique or activity employed within the Information Environment that can be used to create operational effects and conditions. Other IRCs include Military Deception, Military Information Support Operations (MISO), Leadership Engagement, Civil Affairs, Combat Camera, Operations Security (OPSEC), Public Affairs, Cyberspace Electromagnetic Activities, Electronic Warfare, Cyberspace Operations, Space Operations and Special Technical Operations. US Army, 2016, pp 2-3
- US Army, 2016, p 1
- To further describe the three dimensions that make up the Information Environment, the Physical Dimension includes the tangible network elements, communications networks, information systems and network infrastructures. The Informational Dimension consists of information itself, which acts as the link between the physical and cognitive dimensions. The Cognitive Dimension consists of the minds of those who transmit, receive, and respond to or act on information. US Army, 2017, FM 3- 12 Cyberspace and Electromagnetic Activities, at: https://fas.org/irp/doddir/army/fm3-12. pdf, accessed 18 Jun, 2017, pp 12-13
- To further describe the layers of cyberspace, the Physical Network Layer includes the geographic component within the physical dimension, it includes the hardware, system software, and infrastructure that supports the network and the physical connectors. The Logical Network Layer consists of the components that represent
- the requisite data moving through the network. The Cyber-Persona Layer is the digital representation of the individual or identity in cyberspace, which are the people using the network. US Army, 2017, pp 13-14
- US Army, 2017, pp 13-14
- US DoD, 2016, p 17
- US DoD, 2016, p 24
- US DoD, 2016, p 24
- US CYBERCOM, 2015, ‘Beyond the Build, Delivering Outcomes Through Cyberspace’, at: https://www.defense.gov/Portals/1/features/2015/0415_cyber- strategy/docs/US- Cyber-Command-Commanders-Vision.pdf, accessed 30 May, 2017 US ARCYBER, 2013, The US Army Land Cyber White Paper 2018-2030, at: http:// dtic.mil/dtic/tr/fulltext/u2/a592724.pdf, accessed 4 Jun, 2017, p v
- US DoD, 2016, p.15
- US DoD, 2016, p 15
- Austin, 2016, p 8
- US DoD, 2016, p 15
- Pomerleau, 2016
- Special Warfare is designed to work through and with an indigenous partner force or surrogate, with soldiers being training in combat-advisory skills, military deception, sabotage, foreign languages, relationship-building skills, cultural understanding, adaptive decision making and cognitive problem solving. This may include Foreign Internal Defence (working with a Host-Nation’s security forces) or Unconventional Warfare/Proxy Guerrilla Warfare (working with surrogate, proxy forces). USASOC, 2016, ARSOF 2022, at: pdf, accessed 19 Jun, 2017, pp 10-11
- Surgical strike represents mainly a unilateral, direct action capability aimed at kill/ capture, hostage rescue against specialised and designated targets. USASOC, 2016, p 16
- USASOC, 2016
- The F3EAD targeting cycle was first developed by General Stanley McCrystal during the Iraq War in 2004. It sought to synergise kinetic kill/capture operations with intelligence and exploitation functions to target Insurgent networks. It has since been adopted as the targeting model of choice within the Special Operations community. S McChrystal, 2013, My Share of the Task: A Memoir, ed P Group, Penguin, p 152
- USASOC, 2016, p 26
- USASOC, 2016, pp 26-27
- Osinga, F, 2007, Science, Strategy and War: The Strategic Theory of John Boyd, Routledge, p 44
- Langford, I, 2014, Australian Special Operations: Principles and Considerations, at https://www.army.gov.au/sites/g/files/net1846/f/australianspecialoperat…. pdf, accessed 2 Jun, 2017, p 15
- Davies, 2014, p 9
- A Greene, 2016, ‘Islamic State: Australia’s Special Forces to assist Iraq Military in Battle for Mosul’, at: http://www.abc.net.au/news/2016-10-17/australian-special- forces-to- assist-military-operation-to-retak/7939556, accessed 11 Jun, 2017
- Davies, 2014, p 8
- Langford, 2014, p 15
- UW – Unconventional Warfare, PGW – Proxy Guerilla Warfare, TAA – Train, Advise, Assist, PSDA – Precision Strike/ Direct Action, SR – Strategic Reconnaissance, CT – Counter-Terrorism, SRO – Special Recovery Operations. This has been adapted from the traditional mission sets of Special Reconnaissance, Special Recovery Operations, Precision Strike/Direct Action, Special Support Operations and Support Operations
- J Blaine, 2017, ‘Achieving an Integrated Force by Design’, at: https://www.slideshare. net/robbinlaird/brig-jason-blaine-force-design-department-of- defence-australia, accessed 12 Jun, 2017, p 9
- Will McRaven originally defined ‘Relative Superiority’ as a condition that exists when an attacking force gains a decisive advantage over an enemy. Cyber-Enabled Relative Superiority is defined as the moment in a campaign where effects in, through and external to cyberspace have successfully degraded the physical and cognitive decision- making of an adversary, reinforced support from the civilian population and enhanced the legitimacy and relationship with the partner force. The original phases of conflict graphic has been adapted from ADDP 3-13
- Langford, 2014, p 28
